What is biometric verification?
Biometric verification is any means by which a person can be uniquely identified by evaluating one or more distinguishing biological traits. These biological identifiers include fingerprints, hand and earlobe geometries, retina patterns, voice prints and written signatures.
What is the purpose of biometrics and biometric verification?
Biometrics are mainly used in digital environments to identify a person via their unique biological identifiers. A biometric-based system can answer the question: Who is this person?
Everyone has biological traits or biometrics unique to them and only them. This makes it very difficult to fake or spoof biometrics for unauthorized or malicious purposes. This is why biometric verification methods provide a more reliable, trustworthy way to identify a person, verify their identity (ID) and grant them access to a system in a digital environment. Biometric identification is used in many different applications, including mobile access, airport security, building access, online banking, "know your customer" ( KYC) compliance and fraud prevention.
How does a biometric verification system work?
The authentication process is similar for all biometric identifiers, regardless of the application.
The system first captures a person's unique biometric characteristic -- fingerprint, face, voice print, etc. -- and stores it in a database. When the person returns to the system, say, to open a locked door in an office's server room, ID verification is needed. Suppose the system is fingerprint-based -- say, a thumbprint of the right hand. The user places their right thumb on the biometric system's scanner, which then captures this new record and compares it with the one stored in the database. If the new thumbprint matches the stored database record, the person's identity is confirmed and the door opens. If there is a mismatch, the door remains shut.
Cloud technology is often used to make biometric information more accessible and portable. Cloud-based systems enable organizations -- companies, governments, militaries, etc. -- to perform biometric identification on any individual, regardless of their location. While this can be useful for a range of applications, cloud security remains a concern. Privacy invasions and data breaches are worrisome.
Information storage for biometric data is another security challenge. If a database containing biometric ID records is compromised, the entire system is vulnerable to hacks, putting system reliability in question and making the owners of the biometric identifiers vulnerable to identity theft, fraud and other problems.
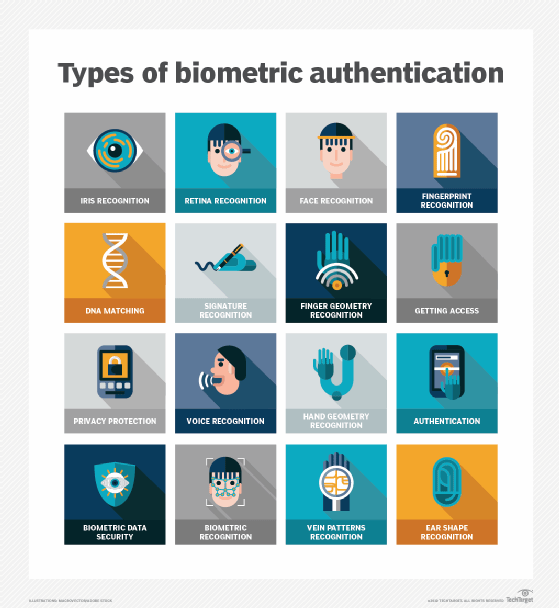
What are the different types of biometric verification?
There are several ways to accurately and securely verify a person's identity using biometrics.
Fingerprint identification
Fingerprint ID remains one of the most common forms of biometric authentication because of its reliability, convenience and historical success. Fingerprints are the oldest type of biometric verification. Thumbprints were used on clay seals in ancient China as unique identifiers.
Almost all smartphones use fingerprint identification to quickly verify a user's identity. A sensor or scanner in the device first captures a user's fingerprint or thumbprint. The print is converted into a digital format and stored inside the phone. When the user provides their fingerprint, say, to unlock the phone, the phone's built-in recognition system compares this new input with the stored input. If it matches, the phone will unlock. If there is a mismatch, the user will see an error message.
Fingerprint technology is reliable for verification because it is difficult to replicate. However, it's not impossible for a determined threat actor to hack into devices using authorized users' fingerprints. If they have access to the user's fingerprints, they can create 3D-printed molds of each user's finger. Fortunately, it's not easy to manipulate another person's fingerprint or create molds to access a device or physical location.
The advent of computerized databases and the digitization of analog data led to the emergence of new technologies that accurately, securely, and near-instantaneously identify a person and verify their identity. These include:
Facial recognition
Along with fingerprint identification, facial recognition is one of the most common verification methods because of the number of unique points on an individual's face. These systems map human facial features and compare them to stored facial biometric data to identify a person and authenticate their ID.
Smartphones are among the earliest adopters of facial recognition, with Apple Face ID being the most well-known application of the technology for consumer handheld devices. With Face ID, an iPhone or iPad Pro user need only glance at the device to unlock it, sign in to apps and even authenticate online purchases. An advanced TrueDepth camera system enables authentication through Face ID. It captures accurate face data and an infrared image of the user's face, then creates a depth map of the face and a neural engine that creates a mathematical representation of the depth map and infrared image. This representation is then compared to the already-enrolled facial data to facilitate facial recognition and its applications.
Facial recognition is also used in buildings to limit access to authorized individuals. As this technology becomes more affordable and mainstream, it will find even more applications -- from ID verification for banking, healthcare, taxation and insurance, to theft prevention, law enforcement, event registration, and online shopping.
Iris and retina pattern recognition
Like fingerprints, the human eye's iris and retina patterns are unique and diverse, which makes them another reliable biometric identifier. An iris scanner can capture high-resolution images of human irises using infrared light, analyze the unique features of each eye, and create a mathematical representation of the captured image. Then, when an individual provides their eye print to identify themselves, the scanner compares this new image to the stored image to confirm their identity and allow or deny access.

Given the strength of security and reliability of this form of identification, banks are using iris and retina pattern authentication methods to verify automated teller machine (ATM) users. The U.S. military also uses iris scanning technology to screen people entering military facilities in certain locations and to identify and track detainees. Increasingly, iris scanning is also used in smartphones, national ID programs, government facilities, borders, and time tracking applications.
Voice waveform recognition
Voices are another form of biometric authentication used in a range of applications. For example, some financial institutions use voice recognition to identify clients over the phone and confirm that they are who they say they are. Voice recognition can help deter criminals attempting to pose as known individuals to perpetrate voice phishing (vishing) scams, preventing them from fooling the bank into revealing a genuine customer's assets or information.
Biometric authentication and fraud prevention solutions are also available that use voice biometrics technology to protect customer interactions and prevent fraud. Such solutions often combine AI-based voice and conversational biometrics with call validation and anti-spoofing technologies to help businesses authenticate real customers and improve the customer experience (CX).
Earlobe and hand geometry identification
Hand and earlobe geometry are also used to ID individuals, although these systems are less common than fingerprint- or face-based systems. Hand-based biometric identification systems measure finger length and the distance between various parts of the hand.
Deoxyribonucleic acid (DNA) matching
Genetic material from an individual can be compared with existing DNA databases to verify a person's identity. This method is commonly used in criminal investigations for forensic purposes. Police officers collect DNA samples from a person -- usually a suspect -- in the form of hair, spit or urine. The sample is then compared with DNA evidence collected at the scene of a crime to determine whether the suspect was involved in that crime.
Vein recognition
Scans of finger veins can also verify an individual's identity. The vascular pattern in a person's finger can be compared to data that was previously obtained to make an identification.
Signature comparison
Signatures are another biometric verification method, albeit one of the least reliable. They can be useful as an additional layer of authentication. One common application of signature analysis is to spot ID fraud by comparing a person's signature with existing records. Mismatches might indicate fraud. However, due to reliability concerns, the method exists more as a forensic tool than an immediate form of verification.
Pros and cons of biometric verification
Biometric verification depends on the use of biological characteristics that can't be changed or replicated. It's hard to replicate some characteristics like fingerprints -- and more importantly, misuse them -- since they are unique to each person. This is why biometric systems provide more reliable digital security than traditional password-based systems and are now a crucial aspect of multifactor authentication (MFA), a popular approach to safeguard people and data. It is also easier to use biometric systems. The person only has to press their fingerprint or look into a camera. There's no need to create, remember, or change complex passwords. Verification occurs quickly, minimizing wait time and improving user experiences.
Despite these benefits, biometric verification is not perfect. As effective and convenient as it is, facial recognition has some cons. It raises concerns around privacy and personal freedom, since some tools collect information without the user's knowledge. Some such information is shared with third-party companies without the user's knowledge. This makes the technology invasive and intrusive and makes it harder for the user to maintain anonymity or protect their sensitive personal data from becoming public knowledge.
Security is another concern. If the facial data collected is improperly stored or protected, it might be misused. It might also be compromised or stolen as part of a broader data breach. Finally, a lack of diversity in training a facial recognition system's algorithm can cause it to produce biased or incorrect results. This can have serious implications for some applications like law enforcement. For example, the system might misidentify an innocent person as a wanted criminal.
Similarly, voice recognition also has some weaknesses. A threat actor could record the voice of a user and replay it for the voice recognition technology. Despite this, it remains an effective way to segment customers. Voice-based technologies, like Siri, Google Assistant and Alexa, all use some form of voice biometrics. Google has users repeat a series of phrases to be able to recognize their voices when they speak certain commands.
The main weakness of hand-based biometric systems is that hand geometry changes with age, necessitating regular updates to the underlying database. Earlobe geometry is one of the few biometrics that does not change with age.
DNA matching is one of the most accurate approaches to verifying identities. However, it is also among the
most intrusive methods and the testing can be time-intensive, with several weeks often required to provide results. This can slow down a criminal investigation and its downstream activities (arrest, arraignment, etc.).
Finally, signature verification is not a reliable biometric identification method because, unlike other biometrics, signatures are vulnerable to replication and manipulation. One well-known, real-
world example of this weakness was demonstrated by the "Zodiac Killer" case. The self-proclaimed "Zodiac Killer" sent letters to the Federal Bureau of Investigation throughout the 1960s and early 1970s. These letters could never conclusively identify the killer because of the lack of handwriting analysis technology.
Common applications of biometric verification
Biometric verification is used to identify people in all sorts of settings:
- Financial institutions are using voice recognition and other biometrics to identify customers and protect their information and assets from fraudulent phone callers.
- Healthcare providers are finding biometrics to be a reliable way to identify patients and also to design and deliver more targeted healthcare interventions.
- Law enforcement agencies use fingerprints, facial recognition, iris scans and other types of biometric ID to identify criminals, conduct forensic analyses, build cases against suspects, assess and mitigate potential threats to the public or to law enforcement officers, conduct criminal background checks, and more.
- Government entities worldwide are looking into using use biometric identifiers in passports, national ID cards, for border security, voter registration and welfare distributions.
- Companies use biometrics to control access to sensitive areas and prevent tailgating (that might lead to theft or social engineering).
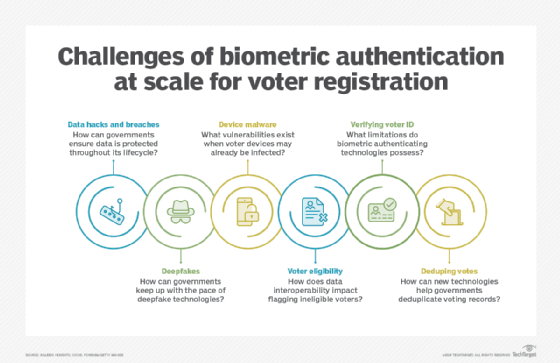
Biometric authentication can successfully supplement passwords when securing data and systems. Understanding its positives and potential drawbacks is essential, however. Explore the pros and cons of biometric authentication and get to know biometric privacy and security challenges.






