authentication server
What is an authentication server?
An authentication server is an application that facilitates the authentication of an entity that attempts to access a network.
Such an entity may be a human user or another server. An authentication server can reside in a dedicated computer, an Ethernet switch, an access point or a network access server.
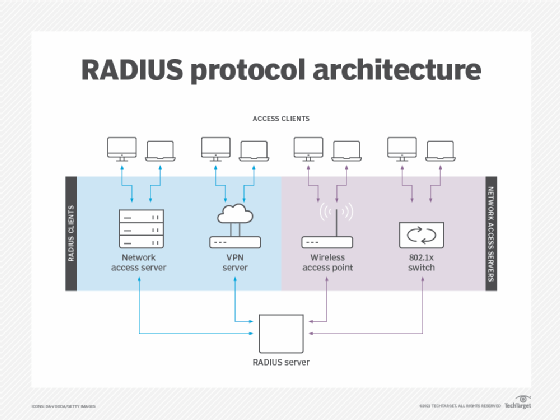
Different types of authentication servers
There are multiple authentication web servers. Different hardware and algorithms are used for different authentication protocols, such as Remote Authentication Dial-In User Service (RADIUS), Active Directory, Lightweight Directory Access Protocol, Secure Sockets Layer and Transport Layer Security.
RADIUS is one of the most commonly used authentication methods. Terminal Access Controller Access Control System Plus (TACACS+) is similar to RADIUS but is used with Unix networks. RADIUS employs User Datagram Protocol, and TACACS+ employs TCP.
Different types of authentication protocols
End-user authentication for accessing user accounts is the process of determining whether someone or something is who or what it declares itself to be.
There are two broad types of authentications: single-factor and multifactor authentication (MFA).
Single-factor authentication
When a potential subscriber accesses an authentication server, a username and password may be the only identifying data required. The authentication process is completed once the user identity is verified.
Multifactor authentication
Apart from entering the user credentials, the user is required to complete an additional step to gain access, such as completing a CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) or using a one-time password.
For example, in Kerberos, the subscriber must request and receive an encrypted security token that can be used to access a particular service.
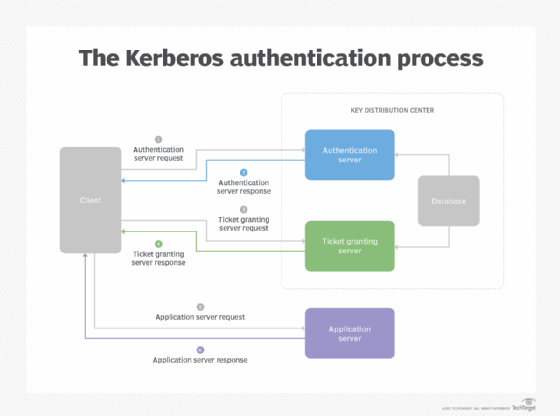
Some specialized authentication servers employ smart cards, IP addresses or biometric verification in addition to one or more of the above mentioned technologies.
See also six user authentication types to secure networks, authentication factors, the most common digital authentication methods, three steps to create a low-friction authentication experience and knowing the difference between identity management vs. authentication.








