antispoofing
What is antispoofing?
Antispoofing is a technique for identifying and dropping packets that have a false source address.
In a spoofing attack, the source address of an incoming packet is changed to make it appear as if it is coming from a known, trusted source. Spoofed packets are commonly used to carry out denial-of-service (DoS) attacks, exploit network and system vulnerabilities, and gain unauthorized access to corporate networks and data.
The principal goal of any cybersecurity offering, such as antispoofing technology, is to protect an organization's data and other information from attacks that might compromise the confidentiality, integrity and availability of that information. Using antispoofing techniques, along with other cybersecurity resources, protects personally identifiable information (PII), critical business data and an organization's reputation.
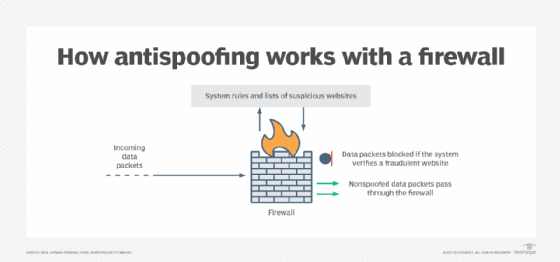
Antispoofing measures are usually embedded in the rules set up on network gateway devices that examine incoming packets. Internet service providers also implement antispoofing measures on behalf of their customers.
Types of spoofing
Spoofing attacks are based on replicating known and trusted sources, such as websites, and fooling victims into accessing them. The following are eight types of spoofing attacks:
- Website spoofing. Attackers create domains and websites that are almost identical to true and existing sites. They often use advertisements, special offers and other inducements that appear to be the same as the true website to lure victims to the hostile site. Once the victim accesses the fake site, the attacker tricks them into providing PII such as Social Security, phone and bank account numbers.
- Email spoofing. Attackers send an email designed to appear to be from a trusted source, such as a utility company, department store or bank. Clicking on the email link might download malware or move the victim to another website where information can be captured. One easy and often reliable way to spot email spoofing is to hold the cursor above the email message to see if the actual sending address is presented visually. If the address looks different from what might be expected, the message can be deleted before any damage is done.
- Biometric spoofing. With this type of spoofing, the attacker replicates human biometric characteristics, such as a fingerprints, to trick a security device. For example, an overlay could be created that replicates a victim's thumbprint. The overlay is placed on top of the attacker's thumb and is then used to fool a thumbprint-reading device and gain access to a system or physical facility. Voice replication is another biometric approach. It's more difficult to fool an eye retina scanning device because duplicating a person's eye retina pattern is difficult.
- MAC address spoofing. Attackers change the media access control (MAC) address of a network interface to impersonate another device. This can allow an attacker to bypass access controls or network restrictions as the spoofed MAC address is considered trusted. By modifying the MAC address, an attacker can deceive network devices into accepting their communication and gain unauthorized access.
- Frame spoofing. Also known as Ethernet frame spoofing, this is a technique where an attacker forges the source or destination information within an Ethernet frame. By modifying the frame header, the attacker makes it appear as if the frame is originating from a different source or going to a different destination. This can be used to redirect network traffic, conduct man-in-the-middle attacks and evade network security measures.
- Internet Protocol spoofing. In these attacks, a network packet's source IP address is altered to deceive the recipient into believing the packet is coming from a trusted source. By modifying the IP header, attackers can hide their true identity, bypass filtering mechanisms or launch DoS and other attacks.
- Data replay attacks. Attackers intercept data packets, record the transmission of legitimate network traffic and then replay those packets to target systems. This can result in consequences, such as unauthorized access, data corruption and disruption of services.
- Authentication replay attacks. Attackers capture authentication data, such as user names, passwords and authentication tokens, and replay them to authenticate themselves without knowledge or consent. The purpose of these attacks is to impersonate authorized users and gain access to sensitive information, systems or resources, leading to potential data breaches, account compromise or unauthorized actions.
How is antispoofing implemented?
Antispoofing technology usually consists of some type of scanning device designated to look for code patterns that can be compared to a list of known spoofing locations. When a match is made, the system blocks the code from getting past the device. Packets that pass the authentication test are permitted.
Spoofed network packets are detected based on rules set up on a network gateway, such as a firewall or router. For example, a rule can be configured to use ingress filtering to single out packets that have conflicting source IP addresses. Packets that show a source address from the internal network will be automatically dropped because internal packets are never filtered by outside-facing interfaces.
Antispoofing technology
Many offerings are available to protect against spoofing and other malware. Most products address a variety of security threats; antimalware systems often include antispoofing and antiphishing tools, as well as resources to block viruses, spam, distributed DoS and other types of cyber attacks.
Spoofing is a big part of wireless network attacks. Find out about the various types of wireless network attacks and how to prevent them.






