access log
What is an access log?
An access log is a list of all requests for individual files -- such as Hypertext Markup Language files, their embedded graphic images and other associated files that get transmitted -- that people or bots have made from a website. Internet-based users make digital footprints in the form of web usage data that is recorded in access logs on web servers. These server logs record the history of page requests made to the server and other pertinent information.
Sometimes referred to as the raw data, the access log can be analyzed and summarized by other programs. Raw log files might also be referred to as audit records, audit trails, audit logs or Event logs.
Access log analyses can provide the following information:
- number of visitors (unique first-time requests) to a specific homepage;
- origin of the visitors, including their associated servers' domain name -- for example, visitors from .edu, .com and .gov sites and from other online services;
- how many requests for each page on the site, presented with the pages with most requests listed first; and
- use patterns related to the time of day, day of the week and season.
Why are access logs important?
Access logs are a valuable business tool because they provide an overview of web traffic, and data from these logs provide insight into how end users interact with web properties. Understanding when users come to a site and where on that site they go is valuable to getting a handle on customer needs. In marketing, for example, data from access logs provides insight into user behavior and helps companies use their websites and address customer needs more efficiently.
As with all types of computer logs, using access logs for monitoring helps pinpoint where errors occurred and what strategies are working -- or not. In addition to monitoring web use over time, access logs show which files were accessed recently, how a company responded to a web request and if there were any unusual requests or anomalies that might suggest a flaw or security vulnerability.
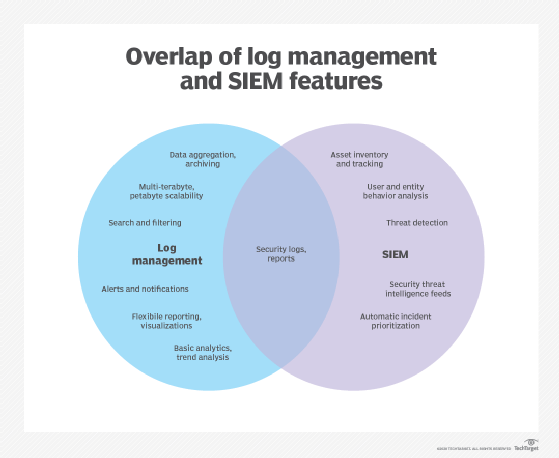
Types of access logs
Different types of access logs collect different types of data. Access logs providing security control include antivirus, firewall and web filter logs:
- Antivirus logs contain data on scanned objects, the settings employed for each task and a history of actions performed on each file.
- Firewall logs provide information about source and destination IP addresses, as well as port numbers, and can be used to analyze an attack.
- Web filter logs might show users attempting to access restricted URLs and how the system responded.
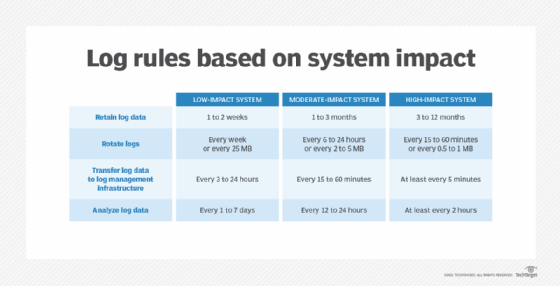
Organizations developing a log strategy should not overlook web server logs; although these logs are common, they provide valuable business insight. Access log keepers and analyzers can be found as Shareware on the web or may come with a web server.
Examples include the following:
- Server access logging offers comprehensive records of all requests made to an Amazon Simple Storage Service (S3) bucket. When logging is enabled, the server access log includes information about the request, type of request, the resources required by the request, and the time and date of the processed request. Administrators can use this information to perform access audits and security audits. This data also helps businesses learn about their customer base or better understand their Amazon S3 bill.
- The Nginx open source web server logs client requests processed by the web server in the access log. Here, you see the accessed files, the browser used by the client, the client's IP address and how Nginx responded to those requests. By default, Nginx access logs are located at /var/log/nginx/access.
- Linux access log files are records maintained by Linux for Linux server administrators. These Linux access logs contain data about the server, kernel, applications and services. These access log files are located by default in a centralized repository under /var/log directory.
- A user access logging service is a Microsoft Windows Server feature that aggregates client usage data by products and roles on the local server. User access logging services help Windows Server administrators quantify all the roles and services requests sent from client computers to the local server.
- An Apache access log is a log file created by an Apache Hypertext Transfer Protocol (HTTP) server. It is part of several log files produced by the Apache server and records data for all requests processed by the server.
- The server software application WebLogic maintains a record of all HTTP transactions in a text file called access.log.
- Other types of access logs include activity logs, error logs and start server logs used for IBM's WebSphere application server.
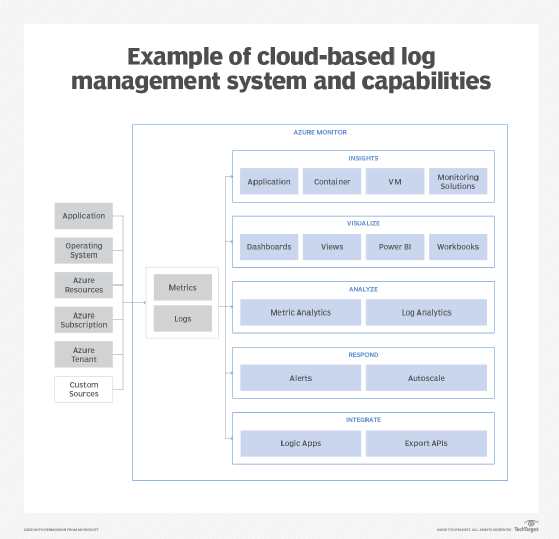
Related terms
Related terminology to access logs includes logical access and logical access control. In IT, logical access describes the process of remotely accessing hardware and interacting with it. Logical access often features authentication protocols, Authorization protocols and identification protocols. In contrast, physical access describes the act of physically interacting with hardware in the environment where it is stored -- for example, a server room or data center.
After establishing the user's identity, logical access controls enable or prevent access to available resources. Once logged in, authorized users have access only to resources that have been already assigned and deemed necessary for them to perform their duties.
See how log analytics tools have gained application performance support skills and log analytics use cases set better ops in motion. Also, gain deeper IT insight with machine learning for log analysis, and consider the pros and cons of AI-based log analysis tools.








