WLAN Authentication and Privacy Infrastructure (WAPI)
What is WLAN Authentication and Privacy Infrastructure (WAPI)?
WLAN Authentication and Privacy Infrastructure (WAPI) is a wireless local area network security standard officially supported by the Chinese government. WAPI was the first LAN national standard developed by China with the goal of strengthening the country's information industry.
First implemented in 2003, WAPI is composed of Wireless Authentication Infrastructure (WAI) for identity authentication and Wireless Privacy Infrastructure (WPI) for data encryption.
Understanding WAPI
The IEEE 802.11 wireless networking standard includes an encryption capability called Wired Equivalent Privacy (WEP). However, since WEP is vulnerable to cyber attacks, IEEE supplemented 802.11 with Wi-Fi Protected Access (WPA) to temporarily enhance the security of wireless networks.
China announced its WLAN specification in 2003 independently of WEP/WPA. This standard is similar to the 802.11 standard. However, the one crucial difference is that the Chinese standard uses WAPI.
Since 802.11 relies on WEP, WAPI is not part of 802.11, and it isn't interoperable with 802.11. This raised concerns that these two incompatible wireless security standards for networking equipment would splinter the market and inconvenience users.
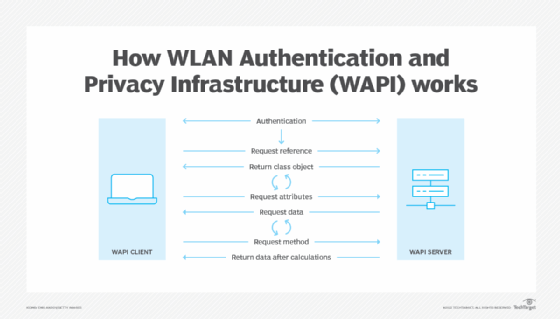
WAPI access and authentication process
WAPI uses a block cipher for encryption (WPI) and an authentication mechanism (WAI). WAI adopts a port-based authentication architecture that is identical to the IEEE 802.1X standard. WAI in WAPI includes three entities: a mobile guest station (STA), access point (AP) and authentication service unit (ASU). Moreover, it is composed of two submodules:
- certificate authentication
- key agreement
The STA and AP are involved during both the certificate authentication and key agreement processes. The ASU is only involved in getting the certificate authentication request from the AP and in sending the certificate authentication response to the AP.
Certificate authentication
During this process, the STA sends an access authentication request to the AP. This request includes the STA's public key certificate and access request time. The AP then sends the STA's certificate and access request time, plus its own certificate, to the ASU in a certificate authentication request.
The ASU validates the two signatures and the AP's signature and then sends all the below to the STA and AP:
- certificate validation result
- STA's access request time
- ASU's signature on them
Key agreement
The key agreement request/response process starts with the STA and AP negotiating the cryptography algorithm. They each generate a random value. The STA's random value is encrypted with the AP's public key and vice versa. The STA and AP send these encrypted values to each other. Both parties then decrypt these values and derive the session key.
In the implementation plan, WAI is the same as the original WAPI. However, the implementation plan makes a big improvement in the key agreement process. The key agreement request initiated by the AP includes the Security Parameter Index, AP's signature on the encrypted random value. Further, in the key agreement response, the message authentication code is calculated through hash-based message authentication code (HMAC)-Secure Hash Algorithm (SHA)-256.
Finally, the STA and AP first calculate the host key and then derive the session key, the authentication key and the integration check key. Here, the host key is extended with KD-HMAC-SHA256 to get the other keys.
The WAPI access and authentication process consists of three submodules:
- certificate authentication process
- unicast key agreement process
- multicast/station key notification process
Certificate authentication process
In this process, three entities are involved:
- Authentication Supplicant Entity (ASUE)
- Authentication Entity (AE)
- Authentication Service Entity (ASE)
Here's how the paper "Security Analysis of WAPI Authentication and Key Exchange Protocol" explains the certificate authentication process.
To initiate the process, the AE and ASUE need mutual certificate authentication. After successful authentication, communication is established between the AE and ASUE. The AE allows ASUE access, and the ASUE allows the dispatch and receipt of data through the AE. The ASE is responsible for certificate authentication of both the AE and ASUE.
The AE sends the authentication and activation packet to initiate authentication. The ASUE receives the packet and checks and distinguishes each word section. If the requirements are met, the ASUE produces an access and authentication request and sends it back to the AE. Next, the AE sends the certificate authentication packet to the ASE. It also receives a response from the ASE of the certificate authentication received, puts this response into an authentication response packet and sends it to the ASUE. The ASUE checks the state of the packet and the AE's certificate authentication result and finally decides whether to access the AE.
The unicast key agreement process between the AE and ASUE begins once the certificate is successfully authenticated.
Unicast key agreement process
After authenticating the certificate, the AE sends the unicast key agreement packet to the ASUE. The ASUE then checks the present state and calculates the local unicast session key. It then constructs a unicast key agreement response packet and sends it to the AE. Once the unicast key agreement is successfully executed, the AE sends a multicast/station key packet. This starts the multicast/station key process.
Multicast/station key notification process
This process utilizes the unicast session key for encryption and a key transmission mechanism. The key security depends on the unicast session key quality.
Advantages and disadvantages of WAPI
WAPI relies on three independent elements -- ASUE, AE and ASE -- to ensure proper authentication and security. During the authentication and encryption process, encryption keys are generated only after negotiation. WAPI uses the SM4 algorithm for authentication. It supports 802.1X authentication, making it suitable for large-scale networks. Further, WAPI applies best to scenarios where high security is required.
China developed WAPI as its own independent wireless security standard to benefit its own information and telecom industries. Nonetheless, its downsides cannot be ignored. For one, the WAI module in the original WAPI and its key agreement protocol are vulnerable to unknown key-share (UKS) and key compromise impersonation (KCI) attacks.
The WAI implementation plan improves on these key agreement weaknesses in the original WAPI to better resist UKS and KCI attacks. For this and other reasons, WAPI is used throughout China's telecommunications system, particularly at government agencies and contractors. But, despite these improvements, other weaknesses remain.
Hardware needs to be upgraded to support WAPI, adding to costs and inconvenience for users. In the long term, WAPI could disrupt global technological infrastructure and the global networking and wireless market -- not only by providing an additional standard for global wireless network communications, but also by enabling China to strengthen its own communication and wireless security sectors. Further, foreign vendors aiming to produce WAPI-compliant products would have to sign coproduction agreements with Chinese companies. They would also have to disclose their technology, while getting little or no control over what goes on from a security perspective.
Finally, vendors will have to comply with two sets of standards: one for China (WAPI) and another for the rest of the world (802.11). These issues could raise concerns about product security and liability, which could affect both the vendor and their customers.
In 2003, WAPI was at the center of a U.S.-China trade dispute when the Chinese government said that wireless devices sold in China would be required to support WAPI. In 2004, China agreed to postpone enforcement of this directive. In addition, in 2006, the International Organization for Standardization rejected China's request that WAPI be recognized as a standard. Despite this rejection, the Chinese government said that it would continue to support the use of WAPI in China.
In 2010, Apple added a WAPI option to the iPhone for use in China.
See also: how to defend against the most common wireless network attacks and wired vs. wireless network security best practices.








