virtual local area network hopping (VLAN hopping)
What is virtual local area network hopping (VLAN hopping)?
Virtual local area network hopping (VLAN hopping) is a method of attacking the network resources of the VLAN by sending packets to a port not usually accessible from an end system. The main goal of this form of attack is to gain access to other VLANs on the same network.
In VLAN hopping, a threat actor must first breach at least one VLAN on the network. This enables cybercriminals to create a base of operations to attack other VLANs connected to the network.
How does VLAN hopping cause network security vulnerabilities?
The vulnerabilities of VLANs relate to their key features, including the following:
- enabling network administrators to partition one switched network to match the functional and security requirements of their systems without needing to run new cables or make significant changes in their network infrastructure;
- improving network performance by grouping together devices that communicate frequently; and
- providing security on larger networks by enabling greater control over which devices have access to each other.
By separating users, VLANs help improve security because users can access only the networks that apply to their roles. In addition, if outside attackers access one VLAN, they will be contained to that network.
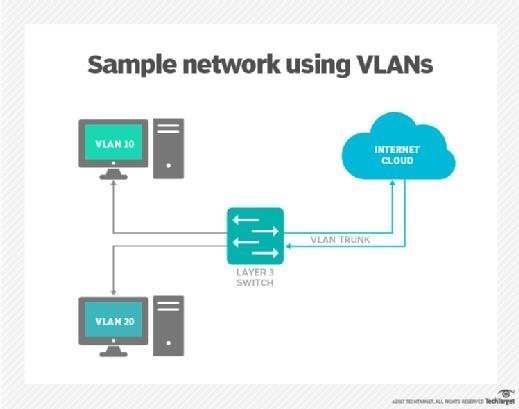
However, when threat actors gain access to VLANs, they can compromise network security protocols quickly and take almost complete control of the network. They can do this because VLANs use a process called trunking, in which VLAN switches are programmed to look for specific channels to send or receive data.
Hackers use this process to penetrate and infiltrate other VLANs connected to the same network. In addition to enabling bad actors to steal passwords and other sensitive information from network subscribers, VLAN hopping can be used to modify or delete data, install malware and propagate threat vectors, such as viruses, worms and Trojans, throughout a network.
Methods of launching VLAN hopping attacks
A VLAN hopping attack can occur in one of two ways:
- double tagging
- switch spoofing
1. Double tagging
Double tagging attacks occur when threat actors add and modify tags on the Ethernet frame. This approach enables the sending of packets through any VLAN as the native untagged VLAN on the trunk and takes advantage of several switches that process tags.
The hacker transmits data through one switch to another by sending frames with two 802.1Q tags: one for the attacking switch and the other for the victim switch. This fools the victim switch into thinking that the frame was intended for it. The target switch then sends the frame along to the victim port.
This can happen because most switches remove the outer tag only before forwarding the frame to all native VLAN ports. For example, if a network switch was set for autotrunking, the attacker turns it into a switch that appears as if it has a constant need to trunk to access all the VLANs allowed on the trunk port. As the encapsulation of the return packet is impossible, this security exploit is essentially a one-way attack. It is possible only if the hacker belongs to the same native VLAN trunk link.
2. Switch spoofing
Switch spoofing occurs when the attacker sends Cisco's Dynamic Trunking Protocol (DTP) packets to negotiate a trunk with a switch. It is possible only when using the dynamic auto or dynamic desirable default switch modes. Once there is a trunk connected to the computer, the attacker gains access to all VLANs. This is a misconfiguration as interfaces should not be configured to use the dynamic switch port modes.
Network security hacking tools
Yersinia is one of the most popular network security hacking tools for Unix-like operating systems. The primary aim of this VLAN hacking tool is to exploit weaknesses in network protocols such as:
- Cisco Discovery Protocol
- Cisco Inter-Switch Link
- DTP
- Dynamic Host Configuration Protocol
- Hot Standby Router Protocol
- IEEE 802.1Q
- IEEE 802.1X
- Spanning Tree Protocol
- VLAN Trunk Protocol
How to prevent VLAN hopping
Good security hygiene helps reduce the risk of VLAN hopping. For example, unused interfaces should be closed and placed in a "parking lot" VLAN. Using VLANs on trunk ports should be avoided unless they are necessary. Additionally, access ports should be configured manually with the switchport mode access.
Proper switch configuration can help mitigate the effects of switch spoofing and double tagging. To reduce the risk of switch spoofing, turn off the autotrunking feature (DTP off) on all switches that do not need to trunk. Additionally, ports that are not supposed to be trunks should be set up as access ports.
Preventing double tagging includes three steps:
- Hosts should not be put on the default Ethernet VLAN, or VLAN 1.
- The native VLAN on every trunk port must be an unused VLAN ID.
- Explicit tagging of the native VLAN should be enabled for all trunk ports.
Learn from experts discussing stretched VLAN use cases, see how to set up a VLAN for enterprise networks and explore 10 network security best practices.







