What is SecOps? Everything you need to know
SecOps, formed from a combination of security and IT operations staff, is a highly skilled team focused on monitoring and assessing risk and protecting corporate assets, often operating from a security operations center, or SOC.
Cybersecurity attacks are on the rise, and the new challenge of supporting a largely remote workforce amid the pandemic and beyond only makes threat detection and prevention more difficult. Staying ahead of attackers is a constant battle, and the cost is unsustainable, according to 69% of executives surveyed for Accenture Security's 2020 State of Cyber Resilience report. Organizations, therefore, are relying more heavily on dedicated SecOps teams to hunt for, detect, prevent and mitigate cyberthreats. This carefully curated guide, complete with links to more information, explains the benefits of creating a dedicated SecOps team, how to build a security operations center to support SecOps, the tools that underpin SecOps and implementation best practices.
SecOps benefits and goals
Security and IT operations teams often work apart from one another, making the task of identifying cybersecurity threats and defending against them -- or, if they turn into attacks, mitigating them -- incredibly difficult. Combining security and IT operations into a dedicated SecOps team enables organizations to rapidly and intelligently predict and address security concerns.
SecOps has the following business benefits and goals:
- continuous protection;
- a quick and effective response;
- decreased costs of breaches and operations;
- threat prevention;
- security expertise;
- compliance;
- communication and collaboration; and
- an improved business reputation.
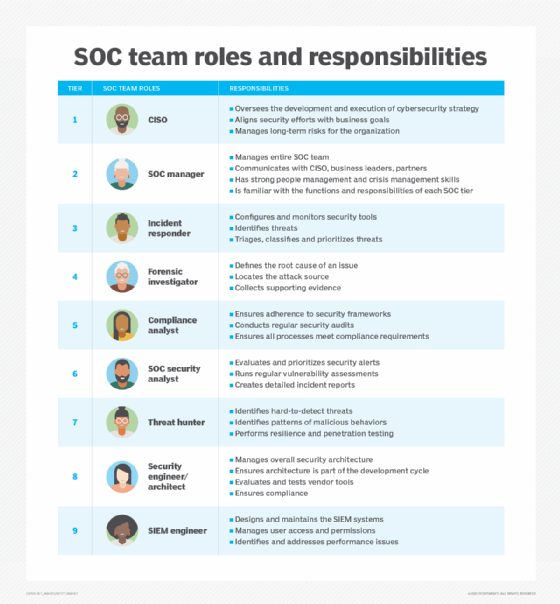
Key roles on a SecOps team
How an organization assembles its SecOps team determines how successful it will be at preventing cyber attacks. Putting roles together piecemeal, without an overarching strategy, will lead to a disjointed response. What CISOs need is a cohesive SecOps team with clear roles and responsibilities that cover the range of cybersecurity threats and attacks.
There are five key roles every SecOps team needs:
- incident responder
- security investigator
- advanced security analyst
- SOC manager
- security engineer/architect
A few new cybersecurity roles have emerged that might give a boost to an organization's SecOps efforts: cloud security specialist, third-party risk specialist and digital ethics professional. These positions address the influence of the cloud and the vulnerabilities of supply chain, as well as partner and privacy concerns.
Organizations that want to migrate employees into SecOps roles can check out these SecOps certifications and training courses.
What does a security operations center do?
A SOC is a command center facility for the SecOps team. While the SecOps team might interact with other teams or departments, it is typically self-contained with highly skilled personnel (internal or outsourced). Most, but not all, SOCs operate 24/7 with SecOps teams working in shifts to log activity and mitigate threats.
Organizations can choose to deploy one of four SOC models:
- a virtual SOC that operates online and is managed by staff or third-party SecOps professionals;
- a multifunction SOC that has a dedicated physical space, but the internal team running the SOC is shared, working on SecOps and other IT tasks;
- a hybrid SOC with a staff, third-party contractors or a mix to perform SecOps tasks full time or part time in a dedicated facility, virtual space or a combination of both; and
- a dedicated SOC with an internally staffed physical space that operates around-the-clock and is solely focused on SecOps functions.
A virtual SOC as a service enables enterprises to outsource some or all SOC responsibilities to a managed service provider -- which has numerous benefits, according to Ashwin Krishnan, chief communicator at SecureDynamics. By outsourcing a SOC, companies with limited budget or in-house skills can better address compliance and regulations, bridge the talent gap and take advantage of a provider's aggregate experiences and resources.
No matter the model an organization selects, the technical capabilities of the SOC should be the same, enabling the SecOps team to perform threat detection and incident response. The SOC also should provide notification and alerting; security orchestration, automation and response (SOAR); and intelligent threat hunting.
Nemertes Research found in its 2019-2020 "Cloud and Cybersecurity Research Study" that successful cybersecurity organizations (those with a mean total time to contain security incidents of 20 minutes or less) were 52% more likely to have a SOC than unsuccessful organizations (those with an MTTC of greater than 20 minutes).
Common SecOps tools
Firewalls and VPNs were once considered strong and adequate defenses against cyber attacks. Not anymore. Kevin Tolly, founder of The Tolly Group, wrote that these technologies "are no longer a shield against more modern and sophisticated security threats."
To combat today's threats, organizations need SecOps software to cover five areas:
- DNS security;
- network detection and response;
- anti-phishing;
- data discovery; and
- packet-level visibility.
Even security information and event management (SIEM) tools are just a start in building a strong SecOps strategy: Organizations would need to add in orchestration, user and entity behavior analytics and more to create a more sophisticated and proactive defense.
Manage security in the cloud
Managing security in cloud environments can be somewhat different than managing security in a traditional enterprise, so SecOps teams need to adapt their tools and strategies accordingly. Dave Shackleford, principal consultant at Voodoo Security, wrote that cloud-enabling a SOC requires SecOps teams to do the following:
- Establish a separate cloud account or subscription entirely under their control.
- Create least privilege accounts to perform specific actions in the cloud when needed.
- Implement multifactor authentication for all accounts.
- Enable write-once storage for logs and evidence.
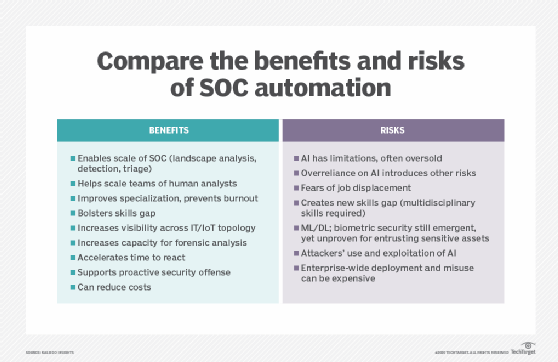
Automation and AI tools
Automation and AI have made their way into SecOps tools, and organizations should try to automate as many functions as possible.
SecOps and SOC automation use cases are plentiful, including incident detection, response and analysis, landscape analysis, emergent threat mitigation, human SOC analyst augmentation and the gamification of security training.
Automated functions enable teams to mine data on security incidents, assign risk scores, cluster for commonalities, differentiate and prioritize different classes of threats, recommend response or remediation steps and more.
With automation, SecOps teams gain awareness of the current state, insight into what could happen and a plan for action. Increased threat vectors such as IoT devices demand SecOps teams have the perspective that AI can provide -- insight that helps improve detection and prevention. Automation also frees up humans from tedious, manual tasks to focus more on SecOps strategy.
Implementation best practices
The concept of pairing security and IT operations is growing in popularity among companies of all sizes, and best practices for structuring SecOps teams and SOCs are emerging.
A sampling of best practices follows:
Define the scope of SecOps
Organizations should determine what functions are within the scope of the SecOps team, taking into consideration the organization's use cases, security requirements and security gaps. Just because a task is out of the team's scope doesn't mean it can't be tackled -- just not by internal teams. Some tasks could be outsourced immediately or earmarked to be outsourced later.
Build or buy
Carefully consider whether to build a SOC or buy SOC services. Outsourcing might not get companies the dedicated attention they need based on their cybersecurity risk tolerance. They might need internal staff intimately familiar with the business to help make key decisions.
Smaller companies should not be afraid to outsource their SOCs, especially if they follow this SOC selection criteria to evaluate potential providers.
Invest in SecOps talent
People can be one of the biggest challenges for SOC implementation, especially due to staffing and skills shortages, according to John Burke, CIO and principal research analyst at Nemertes Research. Organizations should create a strategy aimed at recruiting and retaining SecOps talent.
Conduct red team vs. blue team exercises
SecOps teams need to keep their threat intelligence skills sharp, including the ability to detect and prevent attacks. One way to do this is by conducting red team vs. blue team exercises, where the red team is the aggressor and the blue team is the defender. The red team uses tactics such as penetration testing, phishing, social engineering or other credential theft mechanisms, port scanning and vulnerability scanning to infiltrate the network. The red team also often creates custom tools to test the blue team's ability to detect security issues. Once on the network, the red team will attempt to escalate privileges, and access or steal identities or assets.
The blue team, meanwhile, conducts normal SecOps activities, including analyzing enterprise systems, identifying vulnerabilities, and evaluating the effectiveness of security tools and policies.
Each team generates reports on their activities, and more advanced SecOps teams also will have a purple team to review those reports and improve their security posture, as oftentimes red teams and blue teams don't want to share secrets with one another.
The future of SecOps
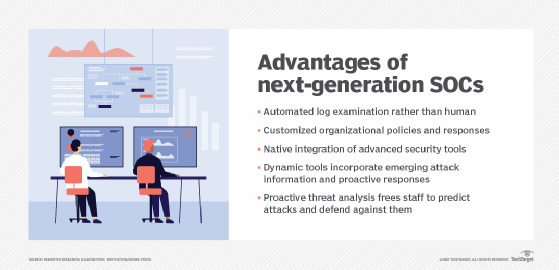
The future of SecOps will see AI and machine learning become a more central part of SecOps strategy. SOCs will be more automated, customized, intelligent, dynamic and proactive. In the future, organizations also will dedicate more time to developing success metrics for their SOCs to evaluate performance and improve response times.
Further, SecOps teams will need to put a greater emphasis on threat hunting to stay ahead of attackers, according to Johna Till Johnson, president and senior founding partner of Nemertes Research. SecOps teams also will likely need to spend more time monitoring and assessing threats in the outside environment by reviewing threat intelligence services going forward.
Organizations should begin now to launch or expand SecOps efforts, as cyber attacks inevitably will continue to threaten enterprise operations.