Structured Threat Information eXpression (STIX)
What is Structured Threat Information eXpression (STIX)?
Structured Threat Information eXpression (STIX) is a standardized Extensible Markup Language (XML) programming language for conveying data about cybersecurity threats in a way that can be easily understood by both humans and security technologies.
STIX is a structured, open source and free language to share cyberthreat intelligence (CTI). The language aims to represent CTI in a structured form to ensure that it is human- and machine-readable, as well as expressive, flexible and extensible. Representing CTI in STIX ensures that it can be shared and analyzed easily and consistently to understand threats and act proactively or defensively.
STIX development and maintenance are primarily community-driven efforts, which means that anyone who is interested in or working in cybersecurity can help develop the language via the STIX website, online forums and other collaborative media. The STIX community also welcomes input from industry and academia to further refine the language and its capabilities.
Purpose of Structured Threat Information eXpression
Comprehensive and up-to-date CTI is essential for organizations to understand the threats posed by various cyber-adversaries and take appropriate action to minimize the negative impact of these adversaries. However, it's not easy to capture CTI since most organizations do not have access to adequate or relevant information. A lack of information affects their ability to build accurate situational awareness of their threat landscape. STIX was developed to address this challenge.
STIX enables security professionals and communities to capture and share CTI in a standardized, understandable way. Consequently, they can all get better insights into the cyberthreat landscape and implement strategies to effectively anticipate and respond to cyber attacks. With STIX, they can improve their cybersecurity-related capabilities, particularly around the following:
- Threat analysis.
- Threat information exchange.
- Automated threat detection and response.
- Analysis of threat indicator patterns.
- Threat prevention.
The open and collaborative nature of STIX enables the sharing of high-fidelity CTI across organizational boundaries. Also, this CTI is not tied to specific security products, services or solutions, which provides a more comprehensive set of CTI for analysis and improves security-related decision-making.
Further, since STIX represents CTI in a structured and standardized form, it supports the application of automation tools and technologies to cybersecurity processes and workflows. Automation can aid human analysis of cyberthreats and help security teams execute defensive or offensive action in response to those threats.
Structured Threat Information eXpression use cases
Designed for broad use in cybersecurity, there are several core use cases for STIX. One, it is used by threat analysts to review cyberthreats and threat-related activity. They can also use STIX to identify patterns that could indicate cyberthreats and to understand the tactics, techniques and procedures (TTPs) used by adversaries to initiate cyber attacks.
Any cybersecurity decision-maker or operations personnel may also use STIX data to facilitate and manage cyberthreat activities, including prevention, detection and response. Another core use for STIX is the sharing of CTI within an organization and with outside partners or communities that can benefit from the information. Sharing and collaboration enable security teams to collaborate with other internal and external parties to learn from each other and improve their own and others' situational awareness of the threat landscape.
STIX architecture and core constructs
The STIX language provides a unifying architecture that combines many types of CTI. There is a total of eight core concepts, all of which are independent, reusable and interrelated:
- Observables describe what has observed or might be observed from a cybersecurity perspective, such as the creation of a new registry key, traffic going to a specific IP address, emails coming from a particular email address, etc.
- Indicators describe potential observables with meaning and context.
- Incidents describe events where adversaries took specific actions.
- Adversary TTPs describe attack patterns, exploits, kill chains, tools used, target victims, etc. used by the adversary.
- Exploit targets describe vulnerabilities, weaknesses or configurations that an adversary might exploit.
- Courses of action describe recommended incident response actions or remedies for an identified vulnerability that may be exploited by an adversary.
- Campaigns describe sets of incidents and/or TTPs -- all with a shared intent.
- Threat actors describe adversaries and their characteristics.
The relationships between the various constructs are indicated on the architecture diagram with arrows. Each arrow label includes a bracketed asterisk ([*]) to imply that each relationship may exist from zero to many times. The language is implemented in the form or an XML schema, which fleshes out the structured content of each construct.
Evolution and future direction of STIX
In 2010, members of the U.S. Computer Emergency Readiness Team and CERT.org -- all experts in security operations and CTI -- established an email list to discuss the need for a standardized representation of CTI indicators. STIX emerged out of those discussions, and in 2012, it was publicly defined with Version 0.3.
When the language was first developed, a rough architecture diagram was created to define the information that should be included in a structured cyberthreat indicator. Over time, the structured CTI architecture was refined, resulting in its XML schema implementation. The schema is still used to develop and refine STIX by its community.
STIX is sponsored by the Office of Cybersecurity and Communications within the United States Department of Homeland Security (DHS). It is also copyrighted by Mitre Corp., which ensures that it remains an open source, free and extensible standard. This standard can be used by anyone concerned with or interested in cybersecurity, including organizations, academics, government agencies and security product/service vendors.
STIX can be used manually or programmatically. Manual use requires an XML editor but no additional tools. Programmatic use requires Python and Java bindings, Python application programming interfaces and utilities. Bindings and related tools to help security analysts process and work with STIX are open source on GitHub.
As of 2023, STIX is in version 2.1. Compared to v2.0, v2.1 includes several new objects and concepts. Some objects, including malware, have undergone significant change. Also, some conflicting properties have been renamed, descriptions and names have been added to some objects, and some STIX Cyber-observable Object relationships have been made external.
STIX and TAXII
Trusted Automated eXchange of Indicator Information (TAXII) is a method for exchanging CTI that is represented in STIX. In other words, TAXII is the transport mechanism for STIX. It enables organizations and security professionals to share structured CTI in an open, standardized, secure and automated manner.
Like STIX, TAXII is a community-driven project sponsored by the U.S. DHS. DHS uses STIX and TAXII so its partners -- private and public -- can exchange CTI using secure automated mechanisms to detect, prevent and mitigate cyberthreats. Many organizations in the private sector also use STIX and TAXII to share threat information with others. Examples include Microsoft, Hewlett Packard Enterprise and numerous cybersecurity vendors.
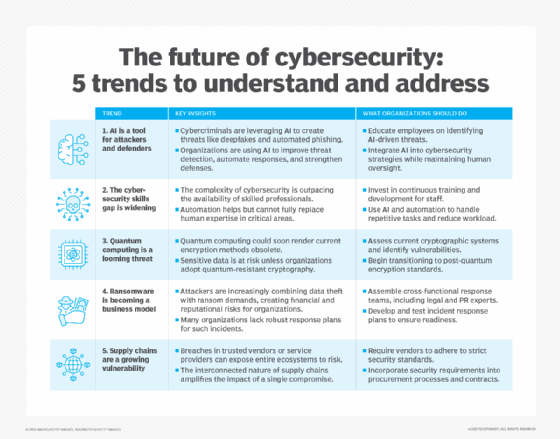
Learn all about the future of cybersecurity, and explore 10 cybersecurity best practices and tips for businesses. See how to fix the top five cybersecurity vulnerabilities, and read about cyber hygiene and why is it important.







