
SOAR (security orchestration, automation and response)
What is SOAR (security orchestration, automation and response)?
SOAR (security orchestration, automation and response) is a stack of compatible software programs that enables an organization to collect data about cybersecurity threats and respond to security events with little or no human assistance. The goal of using a SOAR platform is to improve the efficiency of physical and digital security operations.
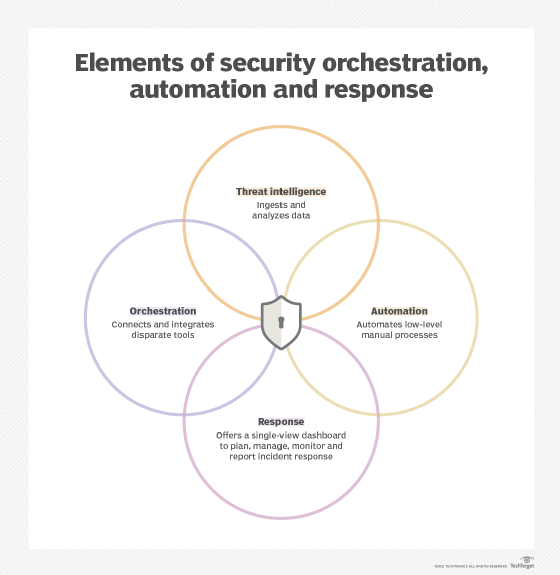
SOAR platforms have three main components: security orchestration, security automation and security response.
Security orchestration
Security orchestration connects and integrates disparate internal and external tools via built-in or custom integrations and application programming interfaces. Connected systems can include vulnerability scanners, endpoint protection products, user and entity behavior analytics, firewalls, intrusion detection and intrusion prevention systems (IDSes/IPSes), security information and event management (SIEM) platforms, endpoint security software, external threat intelligence feeds and other third-party sources.
The more data gathered through these sources, the better the chance of detecting threats, along with assembling more complete context and improving collaboration. The tradeoffs, however, are more alerts and more data to ingest and analyze. Where security orchestration collects and consolidates data to initiate response functions, security automation takes action.
Security automation
Security automation, fed by the data and alerts collected from security orchestration, ingests and analyzes data and creates repeated, automated processes to replace manual processes. Tasks previously performed by analysts, such as vulnerability scanning, log analysis, ticket checking and auditing capabilities, can be standardized and automatically executed by SOAR platforms. Using artificial intelligence (AI) and machine learning to decipher and adapt insights from analysts, SOAR automation can prioritize threats, make recommendations and automate future responses. Alternately, automation can elevate threats if human intervention is needed.
Playbooks are essential to SOAR success. Pre-built or customized playbooks are predefined automated actions. Multiple SOAR playbooks can be connected to complete complex actions. For example, if a malicious URL is found in an employee email and identified during a scan, a playbook can be instituted that blocks the email, alerts the employee of the potential phishing attempt and blocklists the IP address of the sender. SOAR tools can also trigger follow-up investigative actions by security teams, if necessary. In terms of the phishing example, follow-up could include searching other employee inboxes for similar emails and blocking them and their IP addresses, if found.
Security response
Security response offers a single view for analysts into the planning, managing, monitoring and reporting of actions carried out after a threat is detected. This single view enables collaboration and threat intelligence sharing across security, network and systems teams. It also includes post-incident response activities, such as case management and reporting.
What are the benefits of SOAR?
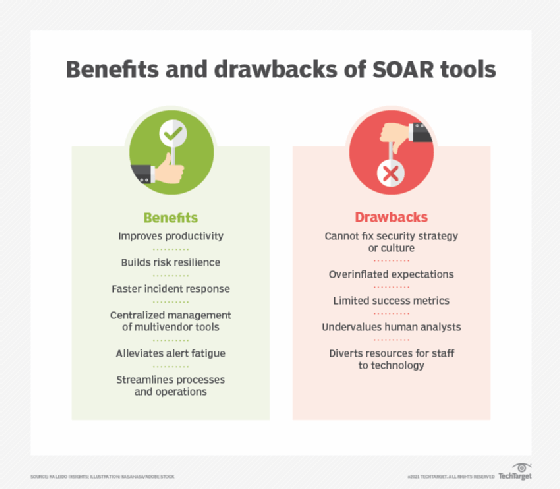
SOAR platforms offer many benefits for enterprise security operations (SecOps) teams, including the following:
- Faster incident detection and reaction times. The volume and velocity of security threats and events are constantly increasing. SOAR's improved data context, combined with automation, can lower mean time to detect, or MTTD, and speed up mean time to respond, or MTTR. By detecting and responding to threats more quickly -- through automated playbooks, when available -- their effects can be lessened.
- Better threat context. By integrating more data from a wider array of tools and systems, SOAR platforms can offer more context, better analysis and up-to-date threat information.
- Simplified management. SOAR platforms consolidate various security systems' dashboards into a single interface. This helps SecOps and other teams by centralizing information and data handling, simplifying management and saving time.
- Scalability. Scaling time-consuming manual tasks can be a drain on employees and even impossible to keep up with as security event volume grows. The orchestration, automation and workflows can meet scalability demands more easily.
- Boosted analyst productivity. Automating lower-level threats augments SecOps and security operations center (SOC) teams' responsibilities, enabling them to prioritize tasks more effectively and respond to threats that require human intervention more quickly.
- Streamlined operations. Standardized procedures and playbooks that automate lower-level tasks enable SecOps teams to respond to more threats in the same time period. These automated workflows also ensure the same standardized remediation efforts are applied organization-wide across all systems.
- Reporting and collaboration. SOAR platforms' reporting and analysis consolidate information quickly, enabling better data management processes and better response efforts to update existing security policies and programs for more effective security. A SOAR platform's centralized dashboard can also improve information sharing across disparate enterprise teams, enhancing communication and collaboration.
- Lowered costs. In many instances, augmenting security analysts with SOAR tools can lower costs, as opposed to manually performing all threat analysis, detection and response workflows.
What are the challenges of SOAR?
SOAR is not a silver-bullet technology, nor is it a standalone system. SOAR platforms should be part of a defense-in-depth security strategy, especially as they require the input of other security systems to successfully detect threats.
SOAR is a complementary technology, not a substitution for other security tools. SOAR platforms are not a replacement for human analysts, but instead can augment their skills and workflows for more effective incident detection and response.
Other potential drawbacks of SOAR include the following:
- Failure to remediate a broader security strategy.
- Conflated expectations.
- Integration complexities.
- Deployment and management complexity.
- Lack of or limited metrics.
SOAR capabilities and use cases
The term SOAR, coined by Gartner in 2015, initially stood for security operations, analytics and reporting. It was updated to its current form in 2017, with Gartner defining SOAR's three main capabilities as the following:
- Threat and vulnerability management technologies that support the remediation of vulnerabilities, providing formalized workflow, reporting and collaboration capabilities.
- Security incident response technologies that support how an organization plans, manages, tracks and coordinates the response to a security incident.
- Security operations automation technologies that support the automation and orchestration of workflows, processes, policy execution and reporting.
Gartner expanded the definition further, refining SOAR's technology convergence to the following:
- Security incident response platforms, which include capabilities such as vulnerability management, case management, incident management, workflows, incident knowledge base, auditing and logging capabilities, reporting and more.
- Security orchestration and automation, which include integrations, workflow automation, playbooks, playbook management, data gathering, log analysis and account lifecycle management.
- Threat intelligence platforms, which include threat intelligence aggregation, analysis and distribution; alert context enrichment; and threat intelligence visualization.
What is SIEM?
Separate from SOAR platforms, SIEM platforms aggregate log and event data from multiple tools, technologies and processes to help organizations detect, analyze and respond to potential security incidents.
SIEM combines security information management, or SIM, and security event management, or SEM, into a single platform. SIEM tools use collection agents to gather information from devices, servers, infrastructure, networks and systems, as well as security tools, such as firewalls, antimalware, domain name system servers, data loss prevention tools, secure web gateways and IDSes/IPSes. Gathered information is used by SIEM platforms to identify potential abnormalities and threats. SIEM systems then alert security teams about any security events.
SIEM features vary, but most include log management, data correlation, analytics, dashboards and alerting.
SOAR vs. SIEM
While SOAR and SIEM platforms both aggregate data from multiple sources, the terms are not interchangeable. SIEM systems collect data, identify deviations, rank threats and generate security alerts. SOAR systems also handle these tasks, but they have additional capabilities. First, SOAR platforms integrate with a wider range of internal and external applications, both security and nonsecurity. Second, whereas SIEM systems only alert security analysts of a potential event, SOAR platforms use automation, AI and machine learning to provide greater context and automated responses to those threats.
Many companies use SOAR to augment in-house SIEM software. In the future, SIEM vendors are expected to add SOAR capabilities to their services, which means the market for these two product lines will merge. Many SIEM vendors offer SOAR capabilities -- namely automation -- in their SIEM products, often calling them next-generation SIEM. Other products, such as email security gateways, endpoint detection and response, network detection and response, and extended detection and response, are also adopting SOAR capabilities.
SOAR vendors and platforms
Gartner's 2023 SOAR market guide provides a list of representative vendors and their products, including the following:
- Anomali ThreatStream.
- Cyware Virtual Cyber Fusion Center.
- D3 Smart SOAR.
- Devo SOAR.
- EclecticIQ Platform.
- Fortinet FortiSOAR.
- Google Cloud Chronicle SOAR.
- IBM Security QRadar SOAR.
- Logsign SOAR.
- Microsoft Sentinel.
- NSFOCUS Intelligent Security Operation Platform.
- CyberRes by OpenText ArcSight SOAR.
- Palo Alto Networks Cortex XSOAR.
- QAX SOAR.
- Rapid7 InsightConnect.
- Revelstoke SOAR.
- ServiceNow Security Operations.
- SIRP SOAR Platform.
- Splunk SOAR.
- Sumo Logic Cloud SOAR.
- Swimlane Turbine.
- ThreatConnect Intelligence-Powered Security Operations.
- ThreatQuotient TDR Orchestrator.
- Tines.
- Torq Hyperautomation.






