RAT (remote access Trojan)
What is a RAT (remote access Trojan)?
A RAT (remote access Trojan) is malware an attacker uses to gain full administrative privileges and remote control of a target computer. RATs are often downloaded along with seemingly legitimate user-requested programs -- such as video games -- or are sent to their target as an email attachment via a phishing email.
Once the host system is compromised, intruders use a backdoor to control the host, or they may distribute RATs to other vulnerable computers and establish a botnet.
Belonging to the family of Trojan horse viruses, RATs are specifically designed to disguise themselves as legitimate content.
How does a remote access Trojan work?
A RAT is typically deployed as a malicious payload using exploit kits, such as Metasploit. Once installed, the RAT gets connected to the command-and-control server, which the hackers control. The hackers achieve this connection by compromising an open TCP port on the target device.
A RAT can also be installed through phishing emails, download packages, web links or torrent files. Users are duped into downloading malicious files through social engineering tactics, or the RAT is installed by threat actors after they gain physical access to a victim's machine, such as through an evil maid attack.
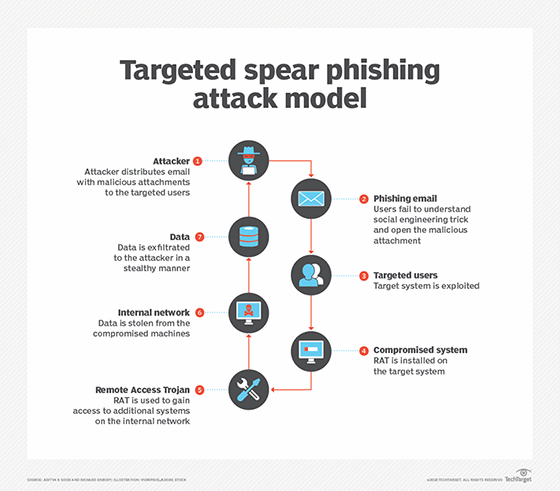
Because a RAT provides a backdoor and enables administrative control, it empowers the intruder to do almost anything on the targeted computer, including the following:
- Monitor user behavior, such as keystrokes, through keyloggers and spyware.
- Access confidential information, such as credit card and Social Security numbers.
- Activate a system's webcam and record video.
- Take screenshots.
- Distribute viruses and malware, as well as launch ransomware
- Format drives.
- Delete, download or alter files and file systems.
Why are remote access Trojans a threat?
RATs can be difficult to detect because they usually don't show up in lists of running programs or tasks. The actions they perform can be similar to those of legitimate applications. In addition, an intruder often manages the level of resource use so that a drop in performance doesn't alert the user that something is amiss.
Unlike other cybersecurity threat vectors, RATs are dangerous even after they've been removed from a system. They can modify files and hard drives, change data, and record user passwords and codes through keylogging and screen captures, all of which can have long-lasting effects.
The following are some ways a RAT can endanger users, systems and organizations:
- Spying and blackmail attempts. By deploying a RAT, threat actors can gain access to the victim's smartphone camera and microphone and compromise their privacy. They can take pictures of users and their surroundings to carry out further attacks or blackmail users into some type of agreement, such as providing ransom money or top-secret data.
- Cryptomining. It's common for threat actors to use RATs to mine Bitcoin and other cryptocurrencies on victims' computers. Attackers can generate significant earnings by spreading RATs across numerous devices.
- Distributed denial-of-service (DDoS) attacks. RATs deployed on a large number of devices can be used to carry out a DDoS attack by flooding a target server with forged traffic. Although a DDoS attack may cause performance degradation, users are typically unaware that their devices are being used to carry out such attacks.
- Remote file storage. To ensure their accounts and operations aren't shut down by the authorities, cybercriminals may use a RAT to store illegitimate content on a victim's device rather than on their storage servers.
- Industrial system compromise. Threat actors often deploy a RAT to take control of large-scale industrial systems, such as water and electricity. The goal of these cyber attacks is to cause widespread damage to industrial machinery and to disrupt critical services to certain geographical areas.
How to protect against remote access Trojans
The same criteria for threat protection against malware and viruses can also be effective against RATs. The following proactive measures can help mitigate remote access Trojans.
Disconnect devices
The first step to take after detecting suspicious activity or the presence of a RAT is to disconnect the devices from the network. This prevents additional malicious activity by severing the remote connection of the installed RAT from the attacker.
Update antivirus and firewalls
Keep antivirus software and firewalls up to date, and refrain from downloading programs or opening attachments that aren't from a trusted source. At the administrative level, block unused ports, turn off idle services and monitor outgoing traffic.
Deploy multifactor authentication
Multifactor authentication (MFA) offers an extra layer of security, as two or more authenticators are required before a service grants access. Since most RATs attempt to steal usernames and passwords, setting up and enforcing MFA across the entire organization is an important defense mechanism.
Avoid suspicious links and attachments
Phishing emails trick unsuspecting users into opening them. Once a malicious link or attachment is opened, it can secretly distribute malware and RATs onto the compromised system. Security awareness training should be provided to all users inside an organization so they can easily spot phishing emails and avoid downloading malicious files and attachments.
Install the latest upgrades
An operating system (OS) should always be patched with the latest updates, as they contain fixes for recently observed vulnerabilities, exploits, bugs and malware, including RATs.
Use an intrusion detection system
An intrusion detection system (IDS) is used for monitoring network traffic and for detecting anomalies or suspicious activities in the network. Even though many RATs have evolved to avoid detection, certain IDSes and advanced persistent threat (APT) tools can be beneficial, as they can detect abnormal patterns of behavior, such as a keyboard and mouse acting strangely or prompting commands on their own.
Employ the principle of least privilege
The principle of least privilege (POLP) is a computer security concept that promotes minimal access to systems and resources. The least amount of privilege that's required for a job is granted initially and is scaled up as needed. The limited access can serve as a roadblock to threat actors from getting full control of a system.
How to detect remote access Trojans
RATs are good at evading detection, and even strong antivirus software can miss them. While only specific scans may detect the presence of a RAT, the following five signs should be observed when searching for a remote access Trojan:
- Failure of antivirus program. An antivirus program that's constantly crashing or responding slowly may signify an infection.
- Slow system performance. RATs run in the background and eat up a lot of processing power. A computer that's running considerably slower without any apparent reason might be infected by a remote Trojan.
- Website redirects. If the browser requests are constantly redirected or webpages aren't loading, then it can be a sign of a RAT infection.
- Unidentifiable files. Any files or programs that seem unrecognizable or weren't downloaded or installed by the user should be observed keenly, as they could be linked to the Trojan virus.
- Operational webcam. The indicator light on a webcam typically turns on when a program accesses a webcam, such as for video conferencing apps. However, if the webcam indicator light turns on for no apparent reason, it could be a sign of a RAT infection.
Common examples of remote access Trojans
- Back Orifice. This rootkit is one of the best-known examples of a RAT. A hacker group known as the Cult of the Dead Cow created Back Orifice to expose the security deficiencies of Microsoft's Windows OS.
- Beast. This RAT uses a client-server architecture, and even though it was developed in 2002, it's still being used today to target both old and new Windows systems.
- Sakula. Also known as Sakurel and Viper, this RAT first emerged in 2012 and was used throughout 2015 in targeted attacks. Threat actors use Sakula to run interactive commands and download and execute additional components.
- Blackshades. This self-propagating RAT spreads by sending out links to the infected user's social media contacts. The infected machines are then used as botnets to launch a DDoS attack.
- CrossRAT. This RAT is particularly difficult to discover and can target most OSes, including Linux, Windows, macOS and Solaris.
- Saefko. This RAT, which is written in .NET, stays in the background and views the user's browser history, looking to steal cryptocurrency-related transaction data.
- Mirage. A type of malware also known as an APT, Mirage is run by a state-sponsored Chinese hacking group that carries out Data exfiltration activities against military and government targets.
With a plethora of antimalware tools on the market, it can be challenging for organizations to pick the right one for their needs. Read through this antimalware software comparison to find the best option.







