What is PKI (public key infrastructure)?
PKI (public key infrastructure) is the underlying framework that enables the secure exchange of information over the internet using digital certificates and public key encryption. This information may be exchanged between many types of entities, including general internet users, web clients, browsers and company servers. The use of PKI and associated digital certificates can also extend to other virtual machines.
The word infrastructure is deliberate in PKI since it does not refer to one single physical entity. Rather, it refers to all the components used to encrypt data and safely distribute, verify, revoke and use digital certificates. These components include hardware, software, policies, procedures and entities.
Is PKI the same as encryption?
PKI is a two-key asymmetric cryptosystem that supports IT systems as they pursue the confidentiality, encryption and confidence of information. Digital keys are like regular keys, except they are used to lock and unlock digital materials. In the case of PKI, lock describes encryption, while unlock refers to decryption.
Encryption is the process by which digital information is scrambled to protect it from unauthorized viewers. Once the sender encrypts information going to an authorized recipient, the recipient needs a way to unlock it to read it. In the PKI system, the two digital keys -- a public key and private key -- used to lock and unlock digital materials are the main pieces that ensure data security and facilitate secure data management between a sender and recipient. A public key lets any user encrypt information for a specified entity, such as a recipient. The only way to decrypt a public key is by using its respective private key. By using a key, users can lock and unlock data as they please. The unique part about keys is that they can also be shared with others. If someone accessed another person's digital key, they are able to decrypt their encrypted data and messages.
The public keys in PKI are connected to a digital certificate from a trusted source. The trusted source is usually a certificate authority (CA). The certificate authenticates entities -- devices or users -- helping to secure transactions, protect data, and prevent message tampering or eavesdropping.
What is the primary goal of PKI?
The main goal of PKI is to provide a comprehensive, standardized system to create, distribute, store, use, manage and revoke digital certificates and establish public key encryption. By providing a framework for data encryption over the internet, PKI helps to authenticate the identities of entities involved in digital transactions. Simply put, PKI makes it possible to verify that an entity is who it claims to be, ensuring secure digital communications between two or more entities.
PKI also does the following:
- Aids in securing traffic between web browsers and web servers.
- Facilitates secure, controlled access to connected devices and resources.
- Helps protect data from leaks and breaches.
- Ensures that digital messages are only visible to the sender and intended recipient, precluding unauthorized entities from tampering or eavesdropping during transit.
- Brings greater accountability and transparency into digital transactions.
How PKI works
Consider a transaction that involves a sender (A) and recipient (B). A wants to send B an encrypted message over the internet. If A uses PKI, they first need B's public key before they can send B a message. Once B provides their public key, A uses it to encrypt the message, data or digital materials going to B. Once the message is encrypted and sent, B can decrypt the information and then access it in its original form using their private key. This is the simplest form of PKI's two-key asymmetric cryptosystem to authenticate communications and protect information.
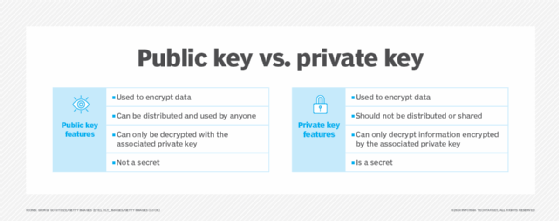
Since PKI uses both a public key and private key, it is a method of asymmetric cryptography or encryption. The public key authenticates the sender who encrypts the message, and the private key -- known only to the recipient -- helps the recipient decrypt the message. Together, these keys provide stronger security of transactions and data compared to much simpler symmetric encryption methods used in the past.
While helpful, even asymmetric encryption is often insufficient for securing modern-day digital conversations between entities. Most of these communications now occur in an expanding cyberthreat landscape, making them vulnerable to tampering, compromise or outright leaks from many different threat actors. Other systems are also needed to verify the identity of the entities or users involved and ensure secure communications.
Without these systems to confirm that the public key being sent to the sender belongs to the intended recipient, entities may inadvertently send sensitive data to unauthorized or malicious users pretending to be people they aren't. Such exchanges may undermine the security, confidentiality and confidence of interactions. Digital certificates powered by asymmetric encryption and PKI help prevent such problems.
PKI governs the issuance and management of digital certificates, also known as PKI certificates, that govern encryption keys. It introduces trusted third parties with the authority to assign identities to digital certificates and issue the tamper-resistant certificates for digital transactions between entities.
Components of PKI
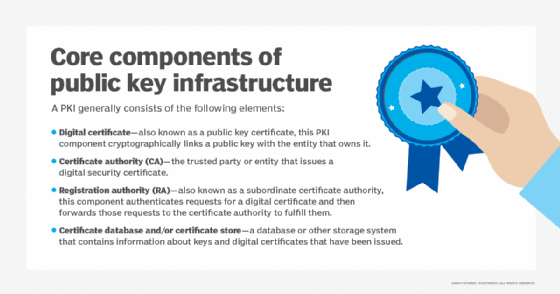
The main components of PKI are the following:
- CA. This trusted party provides the root of trust for all PKI certificates and services useful to authenticate the identity of individuals, computers and other entities. A CA provides assurance about the parties identified in a PKI certificate. Each CA maintains its own root CA for use only by the CA.
- Registration authority (RA). Also called a subordinate CA, the RA issues PKI certificates. Certified by a root CA, it is authorized to issue certificates for specific uses the root permits.
- Certificate store. This is usually permanently stored on a computer but can be maintained in memory for applications that do not require certificates be stored permanently. The certificate store enables programs running on the system to access stored certificates, certificate revocation lists and certificate trust lists.
- Certificate database. This database stores issued certificates and information about those certificates, such as the validity period and status. Certificate revocation occurs by updating this database, which must be queried to authenticate any data digitally signed or encrypted with the certificate holder's secret key.
PKI also includes a central directory where cryptographic keys are stored, a certificate management system that manages the delivery and access of digital certificates, and a certificate policy that determines the certificate's procedures and trustworthiness.
Applications of PKI
The Secure Sockets Layer (SSL) protocol is among the most common applications of the PKI framework . SSL and its successor, Transport Layer Security (TLS), help establish the authenticated and encrypted links between different networked computers used in PKI.
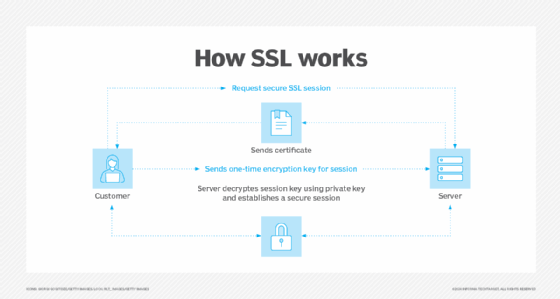
Digital certificates are another important application of PKI, helping to establish trust between website clients and servers. These certificates are also used to sign documents and software.
Other applications of PKI include the following:
- Digital signature software and applications.
- Email encryption.
- Internet of things security.
- Network security.
- Server-hosted communication protection.
- Password recovery.
- File description.
- Smart card authentication.
- Web communications security.
Problems with PKI
PKI provides a chain of trust so identities on a network can be verified. However, PKI also has its drawbacks. It can be hard for a sender to confirm that the public key they received from a recipient belongs to the recipient. Also, it's not impossible for an unauthorized entity to make its own private key and use it to decrypt messages meant for another recipient without the knowledge of the original sender or intended recipient.
Also, even though a CA is often referred to as a trusted third party, shortcomings in the security procedures of various CAs have jeopardized trust. If one CA is compromised, the security of the entire PKI is at risk.
What is a PKI certificate?
It helps to think of PKI like an airport: It is the infrastructure that enables individuals to safely travel from one place to another. Here, the traveler is the data or message that is supposed to be sent, and the two parties are the arrival and departure terminals. For data to board the plane, it needs to first go through customs. The PKI equivalent of customs involves servers and clients validating each other's passports or digital certificates prior to the exchange.
A PKI certificate, digital certificate or X.509 certificate is a data package that authenticates the identity of the server associated with the public key. This package includes digital files, documents and cryptographic data used to validate an entity's identity. A PKI certificate is like a digital passport. To send information using PKI, users must be able to verify who they are and who their recipient is. Here's where the digital certificate comes in. Like passports, digital certificates need to be issued by credible institutions to confirm their legitimacy. To prevent manipulation or corruption of digital certificates and to further secure digital transactions, PKI-based security systems often require additional verification.
Certain standards, such as the Internet X.509 PKI Certificate Policy and Certification Practices Framework, or Request for Comments 2527, cover aspects of PKI. The CA/Browser Forum also publishes digital certificate usage guidelines and best practices for CAs, browsers and other parties involved in PKI. This industry consortium emerged in 2005; its members include CAs, browser software publishers and other system providers that use X.509 digital certificates for encryption and authentication.
In addition to digital certificates, PKI also powers other systems widely used for digital security, including the following:
- Secure Shell algorithms.
- SSL/TLS.
- Code signing.
- Secure/Multipurpose Internet Mail Extensions email encryption.
How to obtain a digital certificate
The easiest way to obtain a digital certificate is to get one made and signed by a publicly trusted CA. CAs issue, distribute and revoke digital certificates to entities based on country- or company-specific legislation. Individual companies can use their in-house CA system if they require additional security and have the necessary infrastructure to support it.
After a digital certificate is issued, it can be distributed by anyone to anyone, not unlike a public key. A digital certificate can be individually validated; it contains no private information. Most digital certificates are implicitly trusted by client software, such as web browsers, and don't require additional validation.
PKI helps authenticate senders via cryptography and digital certificates. Learn about types of PKI certificates and their use cases.






