Open System Authentication (OSA)
What is Open System Authentication (OSA)?
Open System Authentication (OSA) is a process by which a computer can gain access to a wireless network that uses the Wired Equivalent Privacy (WEP) protocol. With OSA, a computer equipped with a wireless modem can access any WEP network and receive files that are not encrypted.
OSA is one of two authentication architectures specified in the IEEE 802.11 wireless standard. Dating from 1997, IEEE 802.11 addresses many different wireless access control arrangements for connecting mobile devices or local area networks (LANs) to wireless access points.
The WEP protocol uses a static encryption key that doesn't change as each packet is sent, leaving networks vulnerable to attacks. Today, both WEP and OSA are considered obsolete authentication processes. IEEE declared the WEP protocol deprecated in 2004. Wi-Fi Alliance's Wi-Fi Protected Access (WPA) was released in 2003 and is now the favored wireless network security protocol. WPA3 is the current version of the wireless security protocol.
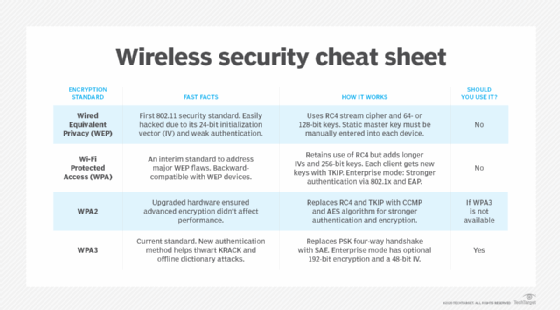
How does OSA work?
Authentication is necessary to establish a secure connection between wireless devices and access points. IEEE 802.11 specifies two authentication methods: OSA and Shared Key Authentication (SKA), which supports access to encrypted data, as opposed to unencrypted clear text. SKA is also considered obsolete.
For OSA to work, the service set identifier of the wireless device should match the SSID of the wireless access point. The SSID is a sequence of characters that uniquely names a wireless LAN (WLAN).
The OSA process follows these three steps:
- The wireless device's radio network interface card (NIC) transmits an authentication request frame to the access point.
- The access point examines the status code field in the frame body and decides whether to approve or deny the request based on the frame data. It returns an authentication response frame indicating approval or rejection of the request. And it provides a random authentication code for use only during that session.
- The computer accepts the authentication code and becomes part of the network as long as the session continues and the computer remains within range of the original access point.
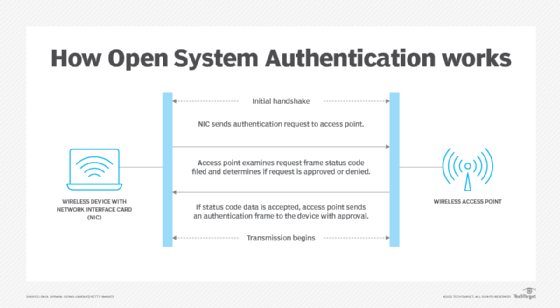
How does Shared Key Authentication work?
SKA, 802.11's alternate security authentication method, uses a four-step process. The difference is that SKA uses challenge-response authentication, in which it examines and validates a WEP key before access is granted.
SKA's four step process is as follows:
- The wireless device's NIC transmits an authentication request frame to the wireless access point.
- The access point inserts a challenge text into a response frame that is sent back to the NIC.
- Using its WEP encryption key, the initiating NIC encrypts the challenge message and returns it to the access point in another authentication frame.
- The access point decrypts the challenge message and checks if it is the same as the original challenge message. If the texts match, the access point assumes the sending device has the correct key and returns an authentication data frame with its approval. If the texts do not match, the access point sends a rejection message.
Which is more secure, OSA or SKA?
With OSA's open authentication method, any device can communicate with the access point, whereas SKA devices must use a WEP key for authentication. However, SKA uses a simple challenge-response protocol. As such, it is vulnerable to dictionary attacks and potential damage to WEP keys.
As previously mentioned, WEP, OSA and SKA are all obsolete technologies. WPA3 is the preferred wireless network protocol. Given the vulnerabilities of wireless technologies, it's important to evaluate an organization's security requirements before investing in a particular one.
Learn what you need to know about wireless networks and the differences between WEP, WPA, WPA2 and WPA3.








