Melissa virus
What is the Melissa virus?
Melissa was a type of email virus that initially became an issue in early 1999. It was a mass-mailing macro virus that targeted Microsoft Word- and Outlook-based systems.
The Melissa virus became one of the fastest-spreading known viruses, leading toward an awareness of the risk and potential damage involved in opening unsolicited email attachments. The virus brought about improvements in online security, while also acting as further inspiration for more potent future viruses. The Melissa virus had such an effect that, a few months after its creator was arrested and sentenced to prison, the Federal Bureau of Investigation (FBI) launched a new national Cyber Division focused on online crimes.
A programmer by the name of David Lee Smith started the mass-mailing macro virus after taking over an AOL account and used it to send the fast-spreading virus through emails.
What did the Melissa virus do?
The Melissa virus was distributed as an email attachment that, when opened, disabled a number of safeguards in Word 97 and Word 2000. In addition, if the user had the Microsoft Outlook email program, the virus sent itself to the first 50 people in the infected user's address book. The virus did not destroy files or other resources but had the potential to disable corporate and other large mail servers -- as email distribution became a much larger problem. The virus crippled hundreds of networks, including those of the United States Marine Corps and Microsoft.
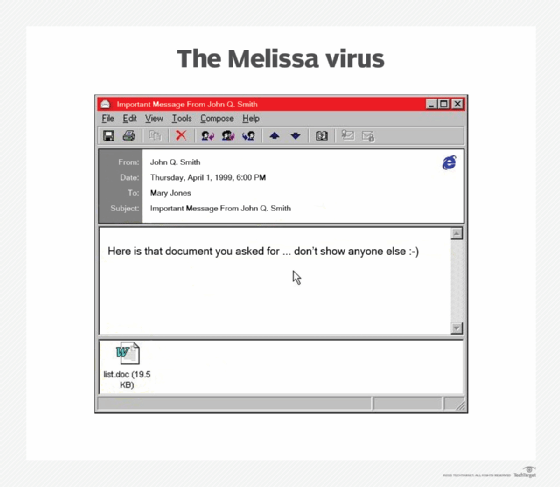
The Melissa virus arrived as an attachment to an email with the subject line, "Important Message from [the sender's username]," and body text that read: "Here is that document you asked for ... don't show anyone else ;-)." The attachment was often named List.Doc. The attached file itself was supposed to contain a list of passwords for various websites that required memberships, but instead, it contained a Visual Basic script. That script copied the infected file into a template file used by Word for custom settings and default macros.
If the recipient opened the attachment, the infecting file was read to computer storage. The virus then created an Outlook object using the Visual Basic code, read the first 50 names in each Outlook Global Address Book, and sent out the same infected document and email.
The virus was released by Smith on March 26, 1999. Even though it overloaded large networks, it was not intended to steal money or data. The U.S. Department of Defense-funded Computer Emergency Response Team issued a warning about the virus and later developed a fix.
The impacts of the Melissa virus
The Melissa virus was one of the early viruses to gain a lot of attention because it caused an estimated $80 million of damage that required cleanup and repair of the affected computer systems. According to the FBI website, the virus overloaded email servers at more than 300 corporations and government agencies, shutting down some entirely. The virus itself reached thousands of computers by sending itself through the mailing lists of infected devices.
Though it took some time to completely remove the infections, cybersecurity experts were able to mostly contain the spread of the virus, ultimately restoring their network functionality. After the virus's spread, the FBI sent out warnings about Melissa and information about its effects, helping to reduce the impact of the virus.
A collaborative effort among the FBI, New Jersey law enforcement and a representative of AOL was able to track down Smith. Smith was arrested on April 1, 1999. He agreed to cooperate with federal and state authorities on the matter, claiming it was intended as a joke and that he had no idea the virus would cause that much damage. Smith pled guilty to state and federal charges in December 1999 and was sentenced to 20 months in federal prison and fined $5,000. Because of this event, more people became aware of how rapidly a computer virus could spread and there were no effective government processes yet to report or analyze similar attacks.

How to avoid email viruses and other security threats
To avoid viruses similar to the Melissa virus, computer users should follow best practices regarding avoiding mail and phishing viruses. These include the following:
- Do not open attachments from unknown email addresses.
- Avoid opening executable files included as attachments.
- Use antivirus and antispyware software to scan devices.
- Scan an email message's attachments for malware.
- Use desktop and network firewalls.
- Use a gateway email filter and web security gateway.
- Double-check the email address to confirm the email is from a legitimate source.
- Update and patch mail clients, web browsers and operating systems regularly.
- Watch for other potential warning signs, such as obvious grammatical errors, suspicious attachments and strange domain names.
Learn more about email security best practices for employees and which six areas your organization should cover.







