IP spoofing
What is IP spoofing?
Internet Protocol (IP) spoofing is a type of malicious attack where the threat actor hides the true source of IP packets to make it difficult to know where they came from. The attacker creates packets, changing the source IP address to impersonate a different computer system, disguise the sender's identity or both. The spoofed packet's header field for the source IP address contains an address that is different from the actual source IP address.
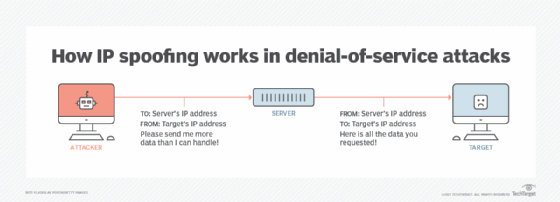
IP spoofing is a technique often used by attackers to launch distributed denial of service (DDoS) attacks and man-in-the-middle attacks against targeted devices or the surrounding infrastructures. The goal of DDoS attacks is to overwhelm a target with traffic while hiding the identity of the malicious source, preventing mitigation efforts.
Using spoofed IP addresses enables attackers to do the following:
- keep authorities from discovering who they are and implicating them in the attack;
- prevent targeted devices from sending alerts about attacks in which they are unwitting participants; and
- bypass security scripts, devices and services that blocklist IP addresses known to be sources of malicious traffic.
How does IP spoofing work?
Internet traffic is sent in units referred to as packets. Packets contain IP headers that have routing information about the packet. This information includes the source IP address and the destination IP address. Think of the packet as a package in the mail and the source IP address as the return address on that package.
In IP address spoofing, the attacker changes the source address in the outgoing packet header. That way, the destination computer sees the packet as coming from a trusted source -- such as a computer on an enterprise network -- and accepts it.
Attackers may generate fraudulent packet headers by falsifying and continuously randomizing the source address using a tool. They may also use the IP address of another existing device so that responses to the spoofed packet go there instead.
To carry out IP spoofing, attackers need the following:
- A trusted IP address that the receiving device would permit to enter the network. There are numerous ways to find device IPs. One way is Shodan, an online database of IP address-to-device mappings.
- The ability to intercept the packet and swap out the real IP header for the fraudulent one. A network sniffing tool or an Address Resolution Protocol (ARP) scan can be used to intercept packets on a network and gather IP addresses to spoof.
How can you detect IP spoofing?
End users have a difficult time detecting IP spoofing. These attacks are carried out at the network layer -- Layer 3 of the Open Systems Interconnection communications model. That way, there aren't external signs of tampering. The spoofed connection requests look like legitimate connection requests externally.
However, there are network monitoring tools that organizations can use to perform traffic analysis at network endpoints. Packet filtering is the main way to do this.
Packet filtering systems are often contained in routers and firewalls. They detect inconsistencies between the packet's IP address and desired IP addresses contained on access control lists (ACLs). They also detect fraudulent packets.
Ingress filtering and Egress filtering are the two types of packet filtering:
- Ingress filtering examines incoming packets to see if the source IP header matches a permitted source address. It rejects any that don't match or that display other suspicious behavior. This filtering establishes an ACL with permitted source IP addresses.
- Egress filtering examines outgoing It scans for source IP addresses that don't match those on the company's network. This approach prevents insiders from launching an IP spoofing attack.
How do you protect against IP spoofing?
IP spoofed packets can't be eliminated. But organizations can take measures to protect their networks and data.
Here are some steps companies can take:
- Use strong verification and authentication methods for all remote access. Do not authenticate devices and users solely based on IP address.
- Make an ACL of IP addresses.
- Use both ingress and egress packet filtering.
- Use antivirus and other security software that watches for suspicious network activity.
- Use IP-level encryption protocols to protect traffic going to and from the enterprise server. This approach keeps attackers from reading potential IP addresses to impersonate.
- Keep network software updated, and practice good patch management.
- Performing ongoing network monitoring.
Firewalls and enterprise router filtering rules should be configured to reject packets that may be spoofed. That would include packets with private IP addresses that come from outside the enterprise perimeter. It also covers traffic that originates inside the enterprise but spoofs an external address as the source IP address. This prevents spoofing attacks from being initiated from the internal network against external networks.
What are other types of network spoofing?
There are several types of spoofing, many of which happen on IP-based networks. But most of these are not IP address spoofing where the IP address of a packet is changed.
Some other spoofing types that deal with IP addresses include the following:
Address Resolution Protocol. An ARP spoofing attack occurs when an attacker sends false ARP messages over a local area network (LAN). This links the attacker's media access control address with the IP address of a legitimate computer or server on the network. This occurs at the data link layer in the Ethernet frames carrying that protocol.
Domain name system (DNS). With a DNS spoofing attack, the DNS records and diverts internet traffic away from legitimate servers and toward fake ones. DNS maps IP addresses to websites, and users access DNS servers to get to websites. Hackers can inject fake DNS entries into DNS servers so that, when users access the server, they are sent to the location that the hacker injected, rather than to their intended destination.
Other spoofing methods address different information types and may not affect IP addresses directly or at all. Some examples include the following:
Caller ID. Caller ID spoofing changes a caller ID to make a phone call appear to be coming from a different location. This commonly happens when telemarketers call targets using the target's area code.
Email. Attackers alter email header fields to falsely indicate that the message originated from a different sender. Spoofed email is often part of a phishing attack that contains a link to a duplicate version of a website that appears to be the original. The spoofed website attempts to trick target victims into handing over login credentials or other confidential information.
Global positioning system (GPS). GPS spoofing is when a user of a mobile device tricks the device into displaying a location that is different from its true geographic location. This can be done using a third-party application that produces different position and navigation information.
Short Message Service (SMS). SMS or text message spoofing is when the sender's phone number is changed to another to obscure the real phone number. Attackers may include links to phishing sites or malware downloads in their texts. Legitimate organizations may also use this method to replace a difficult-to-remember phone number with an easy-to-remember alphanumeric ID.
URL. With this type of spoofing, malicious actors use an almost identical URL that mimics a real one with a few changed characters. The intention is to get the target to go to a webpage that mimics the appearance of a legitimate one and then have them enter sensitive information.
What are examples of IP spoofing?
When attackers launch a DDoS attack, they use spoofed IP addresses to overwhelm computer servers with packet volumes too large for the destination computers to handle. Botnets are often used to send geographically dispersed packets. Large botnets may contain tens of thousands of computers, each of which can spoof multiple source IP addresses at the same time. These automated attacks are hard to trace.
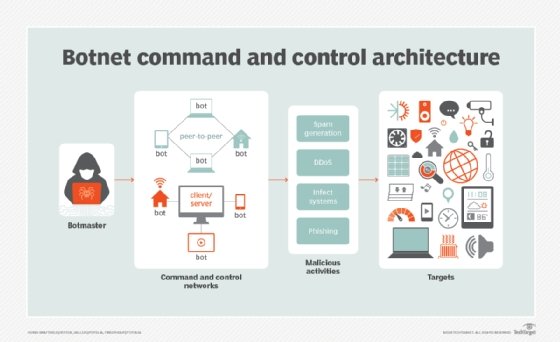
Examples of how spoofing has been used in DDoS attacks include the following:
- GitHub. On Feb. 28, 2018, the GitHub code hosting platform was hit by what at the time was believed to be the largest DDoS attack ever. Attackers spoofed GitHub's IP address and sent queries to memcached servers that are often used to speed up database-driven sites. The servers amplified the returned data from those requests to GitHub by a factor of about 50. As a result, for each byte sent by the attacker, up to 51 kilobytes were sent to the target. GitHub was hit with 1.35 terabits per second of traffic, causing the site to go down for 10 minutes.
- Tsutomu Shimomura. On Dec. 25, 1994, hacker Kevin Mitnick launched an attack against the computers of rival hacker Tsutomu Shimomura using IP spoofing. Mitnick exploited the trust relationship between Shimomura's X terminal computer and the server by learning the pattern of TCP sequence numbers that the computer generates. He flooded the computer with SYN requests from spoofed IP addresses that were routable but inactive. The computer could not respond to the requests, and its memory filled with SYN requests. This technique is known as SYN scanning.
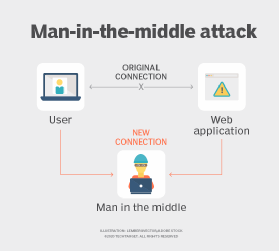
Man-in-the-middle attacks also use IP spoofing to impersonate a target recipient, receive that recipient's internet traffic and respond with their own packets, which may contain malware.
Spoofing has legitimate uses, too. For example, companies may use IP spoofing to test websites when they go live, simulating external traffic to the site. Security personnel also use spoofing see how their systems respond to different types of attacks.
Learn about other common types of cyber attacks and ways to prevent them.







