Evil Corp
What is Evil Corp?
Evil Corp is an international cybercrime network that uses malicious software to steal money from victims' bank accounts and to mount ransomware attacks. In the past decade, Evil Corp has stolen more than $100 million from hundreds of banks worldwide. Many consider Evil Corp to be the world's largest, most harmful hacking group.
Law enforcement has been pursuing Evil Corp for years with limited success. Although the U.S. government sanctioned 17 members of the group and indicted its leaders in December 2019, no arrests followed, and the group remains active as of this writing. The Department of Justice has reported that attacks related to Evil Corp are still occurring.
Evil Corp is named after a fictional multinational corporation from the hacker-themed television show Mr. Robot. The group is allegedly based out of Moscow.
Evil Corp malware and cyber attacks
Evil Corp has developed multiple types of malware, including Dridex, which uses a combination of techniques to automate the theft of users' banking credentials. Dridex sometimes goes by the name Cridex or Bugat, and the terms are used interchangeably.
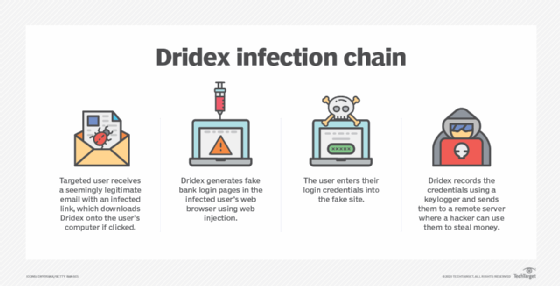
Dridex is distributed using massive phishing email campaigns that send millions of messages per day. Targets receive seemingly legitimate emails with an infected link in the body of the message. If the user clicks the link, Dridex is installed on the machine.
From there, the malware infiltrates the web browser, where it can generate fake bank login pages. Users enter their confidential information into the fake website, and Dridex records what they type using a keylogger. It then sends the credentials to a remote Evil Corp server, giving hackers account access and enabling them to steal money.
The money is sent to Evil Corp indirectly through a network of money mules -- people who receive stolen money and transfer it to the attacker. This makes it harder for law enforcement to follow the money back to Evil Corp.
More recent modifications to Dridex also allow it to deliver ransomware, which renders a target system unusable until the user sends ransom money to the attacker -- a cybercrime model that has exploded in popularity in recent years. Later versions of Dridex also include features for handling cryptocurrency.
In addition, according to the U.S. government, Evil Corp has developed and operated ransomware variants such as DoppelPaymer, Phoenix Locker, Hades and WastedLocker.
Recently, according to cybersecurity firm Mandiant, Evil Corp seems to have embraced the use of third-party ransomware-as-a-service software such as LockBit, possibly to hide its involvement in various attacks and evade U.S. sanctions.
Evil Corp leadership
High scalability and adaptability distinguish Evil Corp as a uniquely influential threat to global cybersecurity. This is partially thanks to the organization's alleged leader, Moscow native Maksim Yakubets.
Yakubets has been involved with Evil Corp since it started using the Zeus banking Trojan in the early 2000s; Zeus is considered the predecessor to Dridex. During this time, Yakubets was responsible for managing the network of money mules used to launder the stolen funds from Zeus attacks.
As a leader, Yakubets reportedly cultivates a global network to ensure Evil Corp's far-reaching influence. Some have speculated that he approaches organized crime like a franchise.
For example, according to court documents, Yakubets offered one U.K. resident access to Dridex in exchange for $100,000 upfront, plus 50% of revenue or a minimum of $50,000 per week. The resident would perform exploits on Evil Corp's behalf, and Yakubets would provide the malware and technical support.
The U.S. and U.K. also alleged that under Yakubets, Evil Corp was working closely with and providing information to the Russian government.
Under Yakubets' leadership, Evil Corp has netted well over $100 million in stolen funds through its bank fraud scheme. Notable victims include the following:
- Penneco Oil Company, which lost $3.5 million to Evil Corp in two transactions;
- Franciscan Sisters of Chicago, an order of nuns that was robbed of more than $24,000; and
- Arizona Beverages, which lost millions of dollars in sales due to a breakdown of infrastructure caused by ransomware introduced by Dridex.
Evil Corp mainly targets banks in English-speaking countries.
U.S. Justice Department indictments
In December 2019, Yakubets and co-conspirator Igor Turashev were indicted by the U.S. government on 10 separate counts, including the following:
- computer hacking
- conspiracy
- wire fraud
- bank fraud
Because Yakubets and Turashev are Russian citizens, however, the U.S. has not been able to arrest them as of this writing. Instead, the U.S. government has offered a $5 million reward for information leading to Yakubets' arrest. The hope is that the money will sway someone -- maybe even the Russian government -- to turn him in.
Indicting the alleged cybercriminals is arguably useful even if there is a slim chance of their arrests. The indictment exposes them and makes anonymity and international travel much more difficult. It also raises awareness about the potential for future attacks.
The U.S. has successfully arrested Evil Corp associates in the past. In 2015, two Ukrainian nationals and one Moldovan national pleaded guilty to charges related to Dridex attacks.
Evil Corp in other contexts
As previously mentioned, the Russian Evil Corp group takes its name from the television show Mr. Robot. In the show, a multinational corporation known as Evil Corp owns most of the world's industry. The show's protagonist is a hacker who aims to breach the company and wrest some power from it.
A Google search for Evil Corp will return a mixture of results referring to the real group and the fictional show. It is possible that the real-life hacking group chose the name in part because it would be more difficult to find information on it, helping minimize its online presence.
It's also worth noting that Google, at one point, adopted the motto "Don't be evil" to demonstrate an interest in corporate social responsibility and acknowledge the general public consensus that large corporations are inherently evil. Various news sources have cited companies such as Walmart and Monsanto as the quintessential "evil corporations." And a Japanese committee of journalists issues an annual award to what it deems the "most evil corporation" of the year.





