Dridex malware
What is Dridex malware?
Dridex is a form of malware that targets its victims' banking information, with the main goal of stealing online account credentials to gain access to their financial assets.
Malware, or malicious software, is a type of software intended to cause harm to a user. Specifically, Dridex malware is classified as a Trojan, which hides malicious code within seemingly harmless data.
Dridex malware operators often target Windows users with phishing email campaigns, hoping to fool individuals into opening attached Word or Excel files. Hidden within these files is the Dridex malware, which -- if opened -- infects users' computers and helps the cybercriminals steal their personal information, mainly banking credentials.
Operators of Dridex typically target financial institutions and their customers, mostly from English-speaking countries. In 2020, Dridex affected 3%-4% of organizations worldwide.
The Dridex malware has undergone numerous updates over the past 10 years. The Russia-based group Evil Corp is allegedly responsible for Dridex.
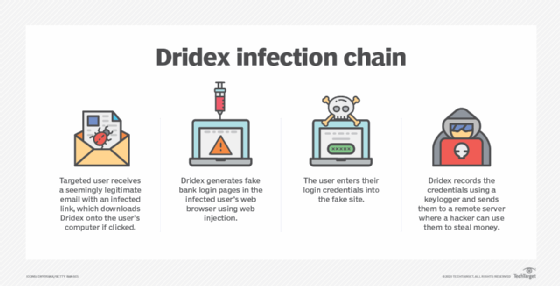
How does Dridex work?
Cybercriminals often spread Dridex through phishing campaigns. The fraudulent emails, which may appear to come from an official and reputable source, prompt victims to click on embedded links or to open attached Microsoft Word or Excel files. Opening one of these files triggers an embedded, malicious macro, which initiates a download of Dridex.
From there, the malware installs a keylogger, which monitors and records each keystroke typed on a computer's keyboard. This enables the attackers to see and steal login and password information, including online banking credentials.
The malware then packages and encrypts stolen data before transmitting it through peer-to-peer networks in XML or binary, depending on the version.
Dridex has a range of other capabilities as well. It can also enable injection attacks, initiating additional malware downloads that let operators execute remote commands or inject code into specific programs. And recently, Dridex has started delivering ransomware.
Dridex is hard to detect, as it can often bypass antivirus detection controls.
How do you detect a Dridex malware infection?
Signature-based threat detection software may not be able to detect Dridex. The threat is constantly evolving, using previously unknown signatures, which makes it difficult to detect.
Tools that do not rely primarily on signature-based threat detection may offer better results. For example, user behavior analytics software uses machine learning to understand patterns of normal activity of users. It then flags unusual traffic for closer inspection.
Malware detection software that is able to identify uncommon behavior or executable files may also catch Dridex infections.
How do you protect against Dridex?
Luckily, it's easier to protect against Dridex than to detect it. Some defensive options for organizations and individuals include the following:
- Practice good cyber hygiene.
- Disable macros by default.
- Be careful when opening emails from unknown senders.
- Don't open files sent from unfamiliar or suspicious email addresses, or from known senders who are behaving unusually.
- Download files only from trusted sources.
- Install software patches as soon as they become available.
- Use malware detection software that uses methods other than signature-based threat detection.
- Use security awareness training to educate users on how to avoid phishing attacks.
How do you remove Dridex malware?
Manual removal of Dridex is possible but difficult. Experts recommend relying on reputable antimalware programs to get rid of the malware.
Once antimalware software has found Dridex, it should quarantine and remove the malicious files. The program may then ask the user to reboot the system, once it's completed the removal process.
Upon becoming aware of a possible Dridex infection, immediately do the following:
- use a separate computer system to change any online banking passwords;
- alert financial institutions to the possible exposure; and
- use a separate computer system to change the passwords to other online accounts accessed on the infected system, such as social media.
History and evolution of Dridex malware
Dridex first made its appearance around 2011-2012. Initially, it was capable of receiving dynamic configuration files and using web injections in order to steal money. At this time, the malware was under the name Cridex -- Cridex malware itself was based off of the original Zeus Trojan horse malware.
Since then, what would eventually become the Dridex malware has been continually been changing and evolving. It's been able to avoid detection by hiding its main servers behind proxy layers. As new versions appear, old ones stop working, hinting that it is one group of people behind Dridex attacks.
A significant variant of Cridex was released in 2012. Notably, this version infected USB media and replaced the binary format of the configuration file and packets with XML. After the 0.8 variant, Cridex remained largely unchanged until version 3.4.
In 2014, the banking malware spread in a spam campaign that sent up to 15,000 emails a day. The attacks focused on systems located in the United Kingdom. One year later, the U.K. was at an estimated £20 million of theft, and $10 million in the United States due to the malware.
On Aug. 28, 2015, one of the administrators of the Dridex network was arrested. After this, in September, three of Dridex's networks went down. Later in October, however, the same networks came back online with six additional networks added. By 2016, the loader used became more complicated, and methods of encryption changed.
The fourth version was first detected in 2017. The big change to this version was that the XML format used was switched back to binary. The packet structure was similar to the ones used in the third version.
From its creation to now, Dridex has had many iterations that added features such as P2P encryption and hashing algorithms.
In December 2019, however, the FBI had charged two suspects who they believed created the Dridex Trojan. Two Russian nationals, Maksim V. Yakubets and Igor Turashev, were suspected for its creation.
Both Yakubets and Turashev were indicted on conspiracy to commit bank fraud, among a host of other charges. Additionally, Yakubets was charged with another charge of conspiracy to commit bank fraud, issued by a different U.S. state for involvement in the malware variant Zeus.
Because Yakubets and Turashev live in Russia, however, the U.S. has been unable to make arrests.







