Digital Signature Standard (DSS)
What is the Digital Signature Standard (DSS)?
The Digital Signature Standard (DSS) is a digital signature algorithm developed by the U.S. National Security Agency as a means of authentication for electronic documents.
A digital signature is equivalent to a written signature used to sign documents and provide physical authentication.
After its creation, DSS was published by the National Institute of Standards and Technology in 1994. It has since become the United States government standard for authentication of electronic documents.
DSS is also specified as a verified means for authentication in Federal Information Processing Standards (FIPS) 186.
There have been four revisions to the FIPS 186 DSS specification since 1994:
- FIPS 186-1 in 1996
- FIPS 186-2 in 2000
- FIPS 186-3 in 2009
- FIPS 186-4 in 2013
How does the Digital Signature Standard work?
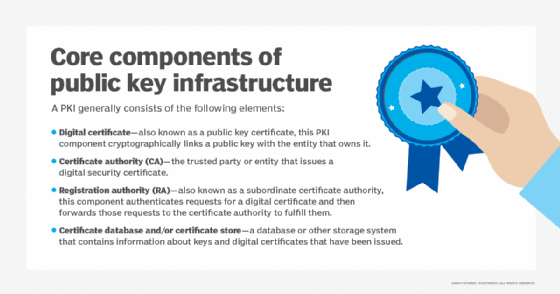
DSA is a pair of large numbers that are computed according to the specified algorithm within parameters that enable the authentication of the signatory and, as a consequence, the integrity of the data attached.
It contains Elliptic Curve Digital Signature Algorithm (DSA), as well as a definition of Rivest-Shamir-Adleman signatures based on Public-Key Cryptography Standards #1 version 2.1 and American National Standards Institute X9.31.
Digital signatures are generated through DSA, as well as verified. Signatures are generated in conjunction with the use of a private key. Verifying the private key takes place in reference to a corresponding public key.
Each signatory has its own paired public and private keys. Because a signature can only be generated by an authorized person using a private key, the corresponding public key can be used by anyone to verify the signature.
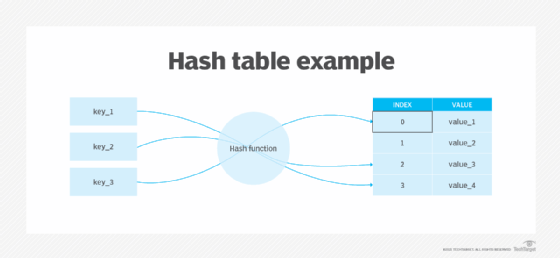
A data summary of the information, called a message digest, is created through the use of a hash function, called Secure Hash Standard, or SHS, and specified in FIPS 180.
The data summary is used in conjunction with DSA to create the digital signature that is sent with the message. Signature verification involves the use of the same secure hash algorithm.
What is the Digital Signature Standard format?
The format or signature scheme for a digital signature, according to DSS, is slightly different on the sender and receiver sides.
On the sender side, the message generates a hash code that requires the following inputs to initiate the signature function:
- the hash code;
- a random number k created specifically for that electronic signature;
- the private key belonging to the sender; and
- the public key.
These inputs create the signer's output signature, which contains two components s and r that are sent to the receiver.
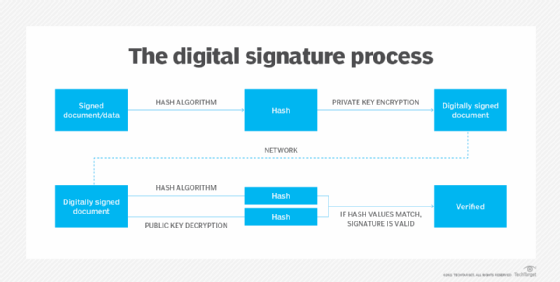
On the receiver side, the sender is already authenticated because its private key acts as the digital certificate. A new hash code is generated, which requires the following inputs to complete the signature verification:
- the new hash code;
- the s and r signature components;
- the sender's public key;
- a global public key; and
- some additional requirements.








