What is Common Vulnerabilities and Exposures (CVE)?
Common Vulnerabilities and Exposures (CVE) is a publicly listed catalog of known security threats. The catalog is sponsored by the U.S. Department of Homeland Security (DHS), and threats are divided into two categories: vulnerabilities and exposures.
Its cumbersome name notwithstanding, the CVE is simply a list of known cybersecurity vulnerabilities. To qualify for addition to the CVE, a vulnerability or flaw must be fixable independently of other flaws, must be acknowledged by a vendor to have a negative impact on security either currently or sometime in the future, and must affect only one codebase, such as one product.
The list, which is maintained by the Mitre Corporation and supported by DHS' Cybersecurity and Infrastructure Security Agency, or CISA, identifies, defines and publicly discloses cybersecurity vulnerabilities. This information can help enterprise security teams to better understand their organization's threat landscape and implement appropriate controls to mitigate known threats.
How does the CVE work?
The Common Vulnerabilities and Exposures system assigns unique identifiers, known as CVE identifiers, to publicly disclosed security flaws. This lets organizations track and address vulnerabilities in software, hardware and other computer systems. When a vulnerability is identified, it's entered into the CVE database, where it's publicly available for reference by security professionals, software vendors and other stakeholders.
All publicly known cybersecurity vulnerabilities in the CVE contain an identification number (CVE ID), a description, and one or more public references. Hundreds or thousands of CVE IDs are issued every year to account for the many new vulnerabilities that are discovered annually.
The ID and description are part of the CVE record. Each vulnerability in the CVE catalog has one CVE record. CVE records are provided in multiple human- and machine-readable formats.
When an organization reports a vulnerability to the CVE, it requests a CVE ID. The responsible CVE Numbering Authority (CNA) reserves the CVE ID. But before publicly disclosing the vulnerability, the CNA identifies the minimum required data elements for a CVE record and then confirms the reported vulnerability. It's only after the CNA's confirmation that the record is published in the CVE list.
Security advisories and security tools use the CVE system to automate vulnerability detection and risk management to improve security issue and incident response and practices. Standardized CVE identifiers let organizations integrate threat intelligence more efficiently. Microsoft, IBM and Oracle often reference CVE entries to inform users about patches or updates that address these vulnerabilities.
What is a vulnerability in the CVE?
In the context of the CVE system, a vulnerability refers to any flaw in a software, firmware, hardware or service component that a cybercriminal or other threat actor can exploit. Such exploitation can happen if an organization knows about a vulnerability, but fails to eliminate it through appropriate information security measures. If the vulnerability is exploited, it could compromise the confidentiality, integrity or availability of the vulnerable component, as well as an organization's operations or data.
However, not every security flaw qualifies for a CVE record. Typically, hardware or software vulnerabilities are considered for addition to the CVE when they lead to unauthorized access, sensitive data exposure or other malicious activity. Common types of vulnerabilities and cyberattacks include malware infections, security flaws in software code and unauthorized access that can result in data breaches. To be included in the CVE database, the vulnerability must be verified by a reliable source, such as a Computer Emergency Response Team (CERT).
What is the goal of Common Vulnerabilities and Exposures?
The catalog's main purpose is to standardize the way each known vulnerability or exposure is identified. Standard IDs let security administrators quickly access technical information about a specific threat across multiple CVE-compatible information sources.
IT and cybersecurity specialists use the CVE and its records to understand, prioritize and address the vulnerabilities that exist in their organizations. They also use it to engage in discussions with colleagues and to coordinate their mitigation efforts.
What is the Common Vulnerability Scoring System?
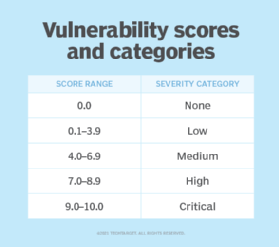
The CVSS is one of many efforts related to but separate from the CVE. It provides a systematic method to understand a known vulnerability and quantify its severity as measured by a numerical score. The U.S. National Vulnerability Database provides a CVSS calculator that enables security teams to create severity rating scores and prioritize CVE records.
Security teams can use the CVSS and CVSS calculator to score the severity of software vulnerabilities that CVE records identify. They can then rate the quantitative severity with a qualitative expression -- such as low, medium, high or critical -- to prioritize vulnerability remediation activities, and to assess and improve vulnerability management capabilities.
What is the difference between CVE and Common Weakness Enumeration?
Common Vulnerabilities and Exposures is the catalog of known vulnerabilities, whereas Common Weakness Enumeration (CWE) is a list of various types of software and hardware weaknesses. Simply put, the CWE lists weaknesses that might lead to a vulnerability.
CWE acts as a dictionary that enumerates the types of flaws found in software and hardware architecture, design, code and implementation. These flaws might result in exploitable security vulnerabilities. Once known, they can make their way into the CVE.
Examples of software weaknesses that might lead to the introduction of vulnerabilities include the following:
- Buffer overflows.
- Manipulations of common special elements.
- Channel and path errors.
- Handler errors.
- User interface errors.
- Authentication errors.
- Code evaluation and injection.
Examples of hardware weaknesses that could lead to the introduction of vulnerabilities include the following:
- Core and compute issues in central processing units and graphics processing units.
- Privilege separation and access control issues.
- Shared resources.
- Power and clock concerns.
CVE Numbering Authority and Root
CVE Numbering Authorities, or CNAs, are entities such as vendors, researchers, bug bounty providers and CERTs. They are given a coverage scope and the authority to both assign CVE IDs to vulnerabilities and publish CVE records. Scope refers to the CNA's specific responsibility for vulnerability identification, descriptions, referencing and publishing on the CVE website for the blocks of CVEs assigned to it.
The CVE program must authorize a CNA for it to be able to assign IDs and publish records. To be authorized, the CNA must have a public vulnerability disclosure policy and a public source for new vulnerability disclosures to the CVE list.
In the CVE program, a Root refers to an organization authorized to recruit, train and govern one or more CNAs or other Roots. A Top-Level Root, also called a TL-Root, is a Root that doesn't report to another Root and is responsible only to the CVE Board.
What is the CVE Board?
The CVE Board is the governing body responsible for overseeing the CVE system. Its members include government agencies like the DHS; academic institutions; and IT companies, such as Microsoft, Oracle and IBM. The CVE Board manages the policies, processes and operations that underpin the CVE program. It plays an important role in making sure the CVE database remains accurate and up to date, and that it includes all relevant security flaws.
The board works closely with organizations that report vulnerabilities, security researchers and vendors to maintain the integrity of the CVE system. It's responsible for evaluating CVE requests and ensuring that each entry is valid. The CVE Board often collaborates with organizations like the National Institute of Standards and Technology to align metrics and standards, making the CVE system an essential part of global cybersecurity efforts.
Explore top online cybersecurity courses and certifications to boost your career.






