BYOI (bring your own identity)
What is BYOI (bring your own identity)?
BYOI (bring your own identity) is an approach to digital authentication in which an end user's username and password are managed by a third party.
BYOI is increasingly being used for website authentication. Instead of requiring visitors to create new usernames and passwords during the registration process, the website enables them to log in with their credentials from services such as Facebook, Apple, Microsoft, Google or Amazon. Figure 1 shows the TikTok login screen, which lets users log in with a variety of accounts.
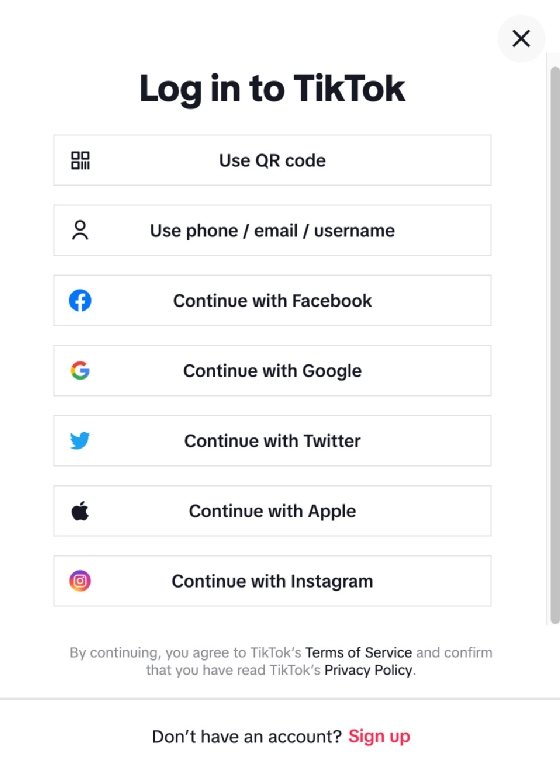
After a user creates an account with a service provider such as Google or Apple, the user can then log in to any other service that accepts the provider's login credentials. In effect, the service provider acts as an identity provider (IdP) that enables third-party service providers to accept the IdP's credentials on behalf of their users. To accept the credentials, the service providers must update their web applications to interface with the IdP and accept the logins.
An IdP does not have to be a social media platform or a vendor like Apple or Microsoft. It might be a government, bank, mobile network operator or standalone service that specializes in identity management. For example, a number of European governments have set up their own identity services. The U.S. government has not, but it has established Login.gov, which provides a secure sign-in service for participating government agencies.
The login process itself is fairly straightforward, although it might vary from one IdP to the next. For example, if a user tries to log in to TikTok and clicks the Continue with Apple option, a small window opens that links directly to Apple.com. Here, the user is walked through the process of entering an Apple ID, password and any other information required to verify the account or prepare for connecting to TikTok. After the user has completed this process, Apple sends an access token to TikTok that confirms the user's identity. The user can then access the TikTok service.
What are the advantages and disadvantages of BYOI?
Many service providers now offer BYOI sign-in capabilities, and the numbers continue to grow. This trend is driven in large part by the advantages that BYOI offers to both the providers and their users, including the following:
- BYOI makes the process easier for users. They don't have to track their credentials for each online service they use, reducing password fatigue and reuse. BYOI also simplifies password management for users and makes it easier for them to log in to a site from different devices.
- A site's registration process becomes much easier for users. As a result, they're less likely to abandon the registration process because it seems too cumbersome. Users might also be inclined to trust a lesser-known service because the login process invokes well-known entities, such as Apple or Microsoft.
- Users share their personal information with fewer providers. This helps to protect their privacy and reduce their online risks. The IdP does not share the user's credential data with the service provider; it sends only an access token that confirms the user's identity.
- BYOI can potentially lead to better security. This is because service providers use the IdP's identity structure rather than using their own. An IdP such as Microsoft or Apple can typically implement much more extensive security than what other service providers might be able to achieve or afford. This can be especially true for startups or smaller organizations with limited budgets.
- In some cases, BYOI can help a service provider address compliance and privacy issues. This is because the IdP is managing and storing the user's credentials, not the service provider. However, this is an advantage only in certain circumstances, which are dictated by the applicable regulations. It is also possible for BYOI to make privacy compliance more difficult.
- BYOI lowers the administrative overhead that comes with identity management. This helps to reduce the service provider's operating costs, while freeing up more time to focus on mission-critical objectives. Additionally, the service provider does not have to invest in the software and hardware needed to support in-house identity management.
Despite the benefits that BYOI offers users and service providers, the strategy also comes with its own concerns. To begin with, users might not want to cede more of their private information to behemoth IdPs that make a point of collecting whatever details they can about their users. For example, if Google is used to register with TikTok, Google knows that the user has created a TikTok account, what account information was provided when registering for that account, and when and how often the user visits TikTok.
Another issue is that the service provider has no control over the identity and access management (IAM) process, outside of handling the IdPs access tokens. This could be problematic if the service provider is governed by data privacy laws that require an organization to maintain strict control over sensitive data. In addition, a service provider might run into support issues if BYOI login attempts fail. The IT team might be able to track down the problem, but if it rests with the IdP, resolving the issue could be difficult and time-consuming.
Perhaps the biggest concern with BYOI is that it represents a single point of failure and a potentially significant security risk. If the IdP's systems go down, users are not able to use their credentials to log on to other registered sites. Worse still, if the IdP's systems and data are compromised as a result of a cyber attack, user data could be exposed, providing cybercriminals with access to multiple accounts rather than just one. The criminals might also be able to access other sensitive data that they can use themselves or sell to the highest bidder.
BYOI might also be called federated authentication or sometimes abbreviated as BYOID.
Explore five IAM trends shaping the future of security, and see how to navigate the new social media landscape. Learn the differences between identity management vs. authentication. Check out four essential IAM best practices.







