Advanced Encryption Standard (AES)
What is the Advanced Encryption Standard (AES)?
The Advanced Encryption Standard (AES) is a symmetric block cipher chosen by the U.S. government to protect classified information.
AES is implemented in software and hardware throughout the world to encrypt sensitive data. It is essential for government computer security, cybersecurity and electronic data protection. Since AES puts data through multiple encryption rounds and splits a message into smaller blocks of 128 bits, it is more secure and reliable than older symmetric encryption methods.
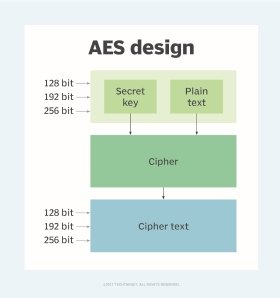
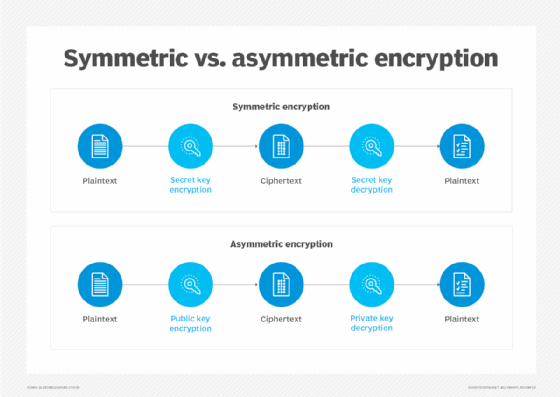
AES is a symmetric encryption algorithm and a block cipher. The former means that it uses the same key to encrypt and decrypt data. The sender and the receiver must both know -- and use -- the same secret encryption key. This makes AES different from asymmetric algorithms, where different keys are used for data encryption and decryption. Block cipher means that AES splits a message into smaller blocks and encrypts those blocks to convert the plaintext message to an unintelligible form called ciphertext.
AES uses multiple cryptographic keys, each of which undergoes multiple rounds of encryption to better protect the data and ensure its confidentiality and integrity. All key lengths can be used to protect Confidential and Secret level information. In general, AES-128 provides adequate security and protection from brute-force attacks for most consumer applications. Information that's classified as Top Secret -- e.g., government or military information -- requires the stronger security provided by either 192- or 256-bit key lengths, which also require more processing power and can take longer to execute.
Where is AES encryption used?
The National Institute of Standards and Technology, or NIST, started development of AES in 1997. In June 2003, AES became the default encryption algorithm for protecting classified information, including government information. It also became the first publicly accessible and open cipher approved by the National Security Agency to protect Top Secret information and national security systems.
AES is also included in the International Organization for Standardization's ISO/IEC 18033-3 standard, which specifies block ciphers for boosting data confidentiality.
Today, AES is one of the most popular symmetric key cryptography algorithms for a wide range of encryption applications for both government and commercial use. Some examples include the following:
- Data on storage media, including hard drives and USB drives.
- Electronic communication apps.
- Programming libraries.
- Internet browsers.
- File and disk compression.
- Wireless networks.
- Databases.
- Login credentials including passwords.
- Virtual private networking (VPN).
How AES encryption works
AES includes three block ciphers or cryptographic keys:
- AES-128 uses a 128-bit key length to encrypt and decrypt message blocks.
- AES-192 uses a 192-bit key length to encrypt and decrypt message blocks.
- AES-256 uses a 256-bit key length to encrypt and decrypt message blocks.
Each cipher encrypts and decrypts data in blocks of 128 bits using cryptographic keys of 128, 192 and 256 bits, respectively. The 128-, 192- and 256-bit keys undergo 10, 12 and 14 rounds of encryption, respectively. A round consists of several processing steps including substitution, transposition and mixing of the plaintext input to transform it into the final ciphertext output. The more rounds there are, the harder it becomes to crack the encryption, and the safer the original information.
In AES, numerous transformations are performed on data. First, the data is put into an array, after which the cipher transformations are repeated over multiple encryption rounds. The first transformation is data substitution using a substitution table and a predefined cipher. In the second transformation, all data rows are shifted by one except the first row. The third transformation mixes columns using the Hill cipher. The last transformation is performed on each column, or data block, using a different part or a small portion of the encryption key. Longer keys need more rounds to complete.
During decryption, the message recipient uses a copy of the cipher to remove the various layers of encryption and convert the ciphertext back into plaintext. Post-conversion, they can read the message, knowing that it was not intercepted or read by anyone else.
Advantages of AES
The AES algorithm provides several advantages over older algorithms such as the Data Encryption Standard (DES):
- Security. AES offers stronger security since it incorporates multiple rounds of encryption, making it harder to break, and harder for threat actors to intercept or steal the encrypted information using brute-force attacks.
- Cost. AES is an open source and ubiquitously available solution, making it cost-effective to adopt and implement.
- Implementation. AES is a flexible and simple algorithm, making it suitable for both hardware and software implementation.
Attacks on AES encryption
Research into attacks on AES encryption has continued since the standard was finalized in 2000. Various researchers have published attacks against reduced-round versions of AES.
Researchers have found a few potential ways to attack AES encryption:
- In 2009, they discovered a possible related-key attack. This cryptanalysis attempted to crack a cipher by studying how it operates using different keys. The related-key attack proved to be a threat only to AES systems that are incorrectly configured.
- Also in 2009, there was a known-key attack against AES-128. A known key was used to discern the structure of the encryption. However, the hack only targeted an eight-round version of AES-128, rather than the standard 10-round version, making the threat relatively minor.
A major risk to AES encryption comes from side-channel attacks where attackers try to collect data about the system's cryptographic functions and then use the information to reverse-engineer the cryptography. These attacks can use timing information, such as how long it takes the computer to perform computations; electromagnetic leaks; audio clues; and optical information -- for example, from a high-resolution camera -- to discover extra information about how the system is processing the AES encryption. In one case, a side-channel attack was used successfully to deduce AES-128 encryption keys by carefully monitoring the cipher's shared use of the processors' cache tables.
Such attacks can be mitigated by plugging the gaps that can lead to data leaks and by using randomization techniques that eliminate the relationship between cipher-protected data and leaked data.
Improperly configured AES systems are also vulnerable to related-key attacks and known-key attacks. The former involves experimenting with the AES cipher using different keys to find a key that works, and the latter involves a hacker who already knows the cipher keys.
How to prevent attacks on AES encryption
To prevent attacks on AES encryption and ensure the security of AES keys, it's important to take the following steps:
- Use strong passwords.
- Use password managers.
- Implement and require multifactor authentication.
- Deploy firewalls and antimalware software.
- Conduct security awareness training to prevent employees from falling victim to social engineering and phishing attacks.
AES vs. RSA
Unlike AES, the RSA (Rivest-Shamir-Adleman) algorithm uses asymmetric cryptography, meaning that two related keys are used for encryption: a public key and a private key.
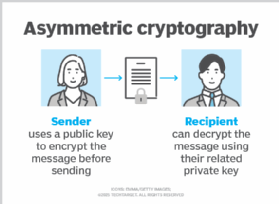
RSA works well for protecting data transfers across geographic boundaries, in web browsers and over VPN connections. However, its biggest drawback is poor performance -- a problem that can be mitigated by combining RSA encryption with AES encryption. This can be accomplished by generating a temporary AES key and protecting it with RSA encryption to combine the security of RSA with the performance of AES.
AES vs. DES
The U.S. government developed DES algorithms more than 40 years ago to ensure government systems all used the same, secure standard to facilitate interconnectivity.
DES served as the linchpin of government cryptography for years until 1999, when researchers broke the algorithm's 56-bit key using a distributed computer system. In 2000, the U.S. government chose to use AES to protect classified information. DES is still used in some instances for backward compatibility.
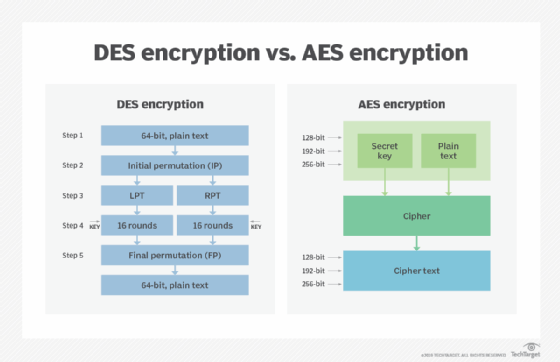
The two standards are both symmetric block ciphers, but AES is more mathematically efficient. The main benefit of AES lies in its key length options. The time required to crack an encryption algorithm is directly related to the length of the key used to secure the communication -- 128, 192 or 256 bits for AES. Therefore, AES is exponentially stronger than the 56-bit key of DES. AES encryption is also significantly faster, so it is ideal for applications, firmware and hardware that require low latency or high throughput.
Further explore the differences between AES vs. DES encryption and symmetric vs. asymmetric encryption. See how to use a public key and private key in digital signatures and how to use centralized encryption methods in large-scale IT environments. Check out our comprehensive guide to data security.





