AAA server (authentication, authorization and accounting)
What is an AAA server?
An AAA server is a server program that handles user requests for access to computer resources and, for an enterprise, provides authentication, authorization and accounting (AAA) services.
The AAA server typically interacts with network access and gateway servers and with databases and directories containing user information. The current standard by which devices or applications communicate with an AAA server is Remote Authentication Dial-In User Service (RADIUS).
Key features of AAA server
The key features of AAA are divided into the following three distinct phases:
- Authentication. When a user wants access to a system or resource that is configured with AAA, the first step in the process is authentication. Here, the user is required to enter valid credentials -- a username and password -- to prove they are who they claim to be. The device that is attempting to be accessed forwards the authentication credentials to a back-end database. If the credentials are valid, the user is granted access to the system. If the username and password are not valid, the authentication process fails, and the user is blocked from accessing the system.
- Authorization. Just because a user successfully authenticates and gains access to a networked system, it does not mean that all authenticated users are authorized to do whatever they like with said system. For example, some users should only be allowed read-only access to a system, while others should be allowed to make changes to configuration settings in a read/write manner. This is the purpose of the Authorization phase of AAA. Administrators can set up various groups and assign access policies around those groups. Thus, some authenticated users may have limited abilities to access certain resources or make changes, while others are authorized to have far greater freedom.
- Accounting. From a security perspective, it would be nice to be able to collect information on who is attempting to authenticate into networks or systems, whether authentication was successful or not, and other information, such as the following:
- the amount of time an authenticated session lasted;
- the amount of data transmitted and received during an authenticated session;
- if and when a user attempts to access a higher level of system access; and
- system commands performed within the authenticated session.
This is precisely what the accounting phase of AAA accomplishes. It acts as a logging mechanism when authenticating to AAA-configured systems.
How does AAA work?
The architecture for AAA requires the following three components:
- Supplicant. This is the user or device that is attempting to gain access to a network or system.
- Authenticator. This is the device the supplicant is trying to access. The authenticator is configured to work with an AAA server for authentication, authorization and accounting purposes.
- Authentication server. This server controls all AAA functions. As noted previously, the AAA server uses the RADIUS protocol for communication and either accesses a local database or is connected to a back-end user authentication database, such as Microsoft Active Directory (AD).
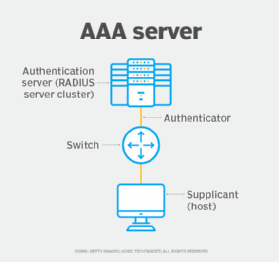
This image shows a typical AAA architecture consisting of the three aforementioned components.
The authenticator sends an authentication request -- usually, in the form of requesting that a username and password be submitted by the supplicant. Once the supplicant sends the username and password, the authenticator forwards the authentication credentials to the authentication server to verify that they match what is contained within the user database. If successful, the authentication server responds back to the authenticator that the authentication attempt was successful and the access level that user is allowed to have based on group policy settings. During this time, authentication, access and session logs are being collected by the authenticator and are either stored locally on the authenticator or are sent to a remote logging server for storage and retrieval purposes.
What are the advantages of AAA servers?
There are several advantages of using AAA. This is especially true if an organization's infrastructure and user base are large. For example, if AAA is not used, it is common for authentication to be handled locally on each individual device, typically using shared usernames and passwords. This method often ends up being a management nightmare and potential security risk. Thus, the benefits of AAA include the following:
- central management and control of individual credentials;
- easy to organize users into groups based on the level of access to systems that is required;
- a logging mechanism that is useful for troubleshooting and cybersecurity purposes; and
- a highly scalable, flexible and redundant architecture.
Does AAA use Active Directory?
For authentication and access permission purposes, an AAA server must reference a database of usernames, passwords and access levels. The protocol used to accomplish this is RADIUS. However, in many cases, the back-end database the AAA server uses to verify credentials and access levels is Microsoft AD. This is accomplished by using Microsoft's Network Policy Server, which acts as a RADIUS server, to tap into the AD username or password and authorization database.
Network security ensures the usability and integrity of network resources. Learn what nine elements are essential for creating a solid approach to network security.








