
peshkov - stock.adobe.com
How to use a public key and private key in digital signatures
Ensuring authenticity of online communications is critical to conduct business. Learn how to use a public key and private key in digital signatures to manage electronic documents.
A person's handwritten signature is relatively unique, so when someone signs a paper document, the signature verifies the signer. But how do you sign an electronic document? This is where a digital signature comes in.
Like a John Hancock on a contractual agreement or a notary seal on a legal document, a digital signature marks the authenticity of a digital message, document or software. Like its physical counterpart, the purpose of a digital signature is to verify the document and that the sender is who they claim to be.
In many countries -- the United States included -- digital signatures are considered legally binding, in the same way that handwritten signatures indicate a conscious agreement was made. Committing the crime of signature forgery may result in penalties ranging from restitution, fines, community service or probationary periods -- even jail time in some extreme cases.
Public and private keys
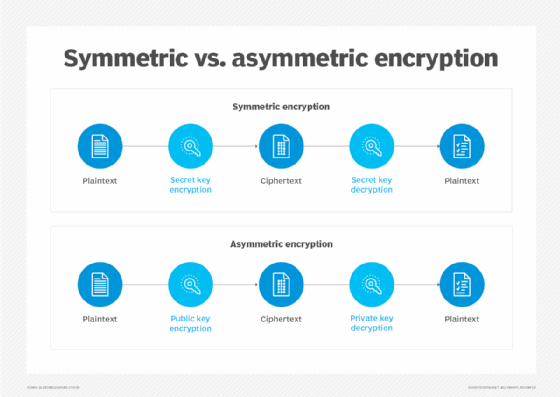
In cryptography, a key is a value used with an algorithm to encrypt and/or decrypt data. A private key, also known as a secret key, is kept on its owner's system and never transmitted publicly. A public key, as the name implies, is openly available to anyone who wants it. It can be posted to a public key server, as in a public key infrastructure system.
Two main types of encryption use keys: symmetric encryption and asymmetric encryption. In symmetric encryption, information is converted from plaintext to ciphertext using the same private key to encrypt and decrypt. In asymmetric encryption, a public key and a private key are used. The sender's private key encrypts the data -- this is the digital signature -- and the receiver uses the public key to decrypt it and verify it matches the attachment. The public key and private key in digital signatures are mathematically related but cannot be generated from each other. Because private keys are specifically assigned and unique to each user, they provide verified authenticity to the sender's message.
The process of signing digital documents requires each party to trust that the individual creating the digital signature has not shared their private key with anyone. If other people were to obtain access to the private key, they could create a fraudulent digital signature in the private key holder's name.
Creating digital signatures
A digital signature is created by signing software -- for example, an email program, DocuSign or Dropbox Sign. Because they provide evidence that an online document or message was not intentionally or unintentionally altered, digital signatures help build trust between parties, including vendors, customers, business partners and employees. Digital signatures also create transparency of various online exchanges. They are a fixture in online business transactions today for convenience and security reasons.
Public key encryption is quite slow. To address this, messages are hashed and then encrypted with the private key, as opposed to encrypting the entire message to create the digital signature. For example, the signing software first creates a one-way hash of the digital document that must be signed. In this way, a digital signature is created by applying a hash function to an online document. Any potential tampering of the online document would result in a different hash value than the original document's hash value. If the two values match, the integrity of the document is assured.
Digital signatures vs. digital certificates
A digital signature and a digital certificate are not the same thing. Whereas a digital signature validates the authenticity of a message, software or digital document, a digital certificate, also known as a public key certificate, verifies the public key belongs to the issuer.
Digital certificates contain the public key, information about its owner, expiration dates and the digital signature of the certificate issuer. A digital certificate is issued by a trusted third party called a certificate authority, such as GlobalSign or DigiCert. When choosing a digital certificate, be aware of the expiration date, as well as how to renew expired certificates.





