
Fotolia
What are the differences between active boards and passive boards?
Both active and passive boards of directors have different approaches to handling cybersecurity within their organizations. Here's how to tell which type you have.
In an earlier piece about security reporting to the board of directors, you discussed active boards vs. passive boards. How can security managers determine if their board is active or passive? What are the signs of an active board of directors, and what are the potential negatives of having a passive board when it comes to security?
The primary role of the board of directors does not include cybersecurity unless the organization has experienced a major breach, so it can be either active or passive in dealing with cybersecurity.
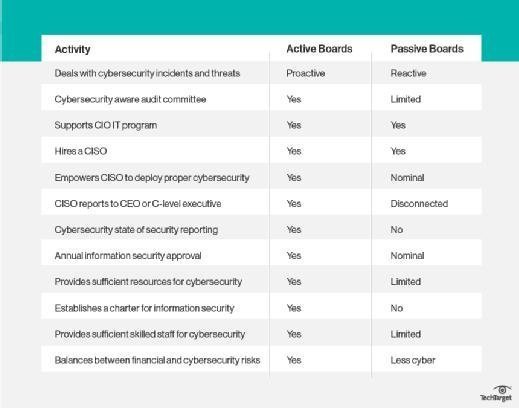
Active boards take on cybersecurity as a significant matter of corporate governance. They consider cybersecurity in SEC risk factor disclosures. They develop, approve and implement a cybersecurity program under the direct supervision of a C-level executive -- either a CISO or an executive. An active board of directors is aware of both internal and external threats and adopts effective mitigants to minimize cybersecurity risks. It requires periodic state of security reports from the information security group or CISO to ensure the program is working effectively. Active boards of directors are strategic and proactive. Many boards look at security breaches and incidents happening to other companies as they would the canary in the coal mine. Active boards make sure their organization is not the canary.
Passive boards of directors, on the other hand, may fully rely on an audit committee to manage and handle cybersecurity threats and reporting. It may not include a state of security report in the agenda unless it has to deal with major threats or handle a major incident. A passive board gives the cybersecurity team five to 10 minutes to delivery their report and will deal with issues only if it's considered material to the well-being of the company. It wants to do just enough to get by and is typically reactive in nature. A passive board will deal with security incidents when they happen, but often at the cost of the CISO's employment and major financial losses due to a desultory information security program.
To figure out if your organization's board is active or passive look for some tell-tale signs:
If this list isn't enough, you can also obtain a list of board members and do an Internet search of each one to get better background on their focus and interests.
If you want to sway passive boards of directors toward taking a more active role in cybersecurity, use the information from the Internet search and identify one or two board members who might be inclined to favor cybersecurity. When you are able to get in front of the board be sure to greet those executives and make eye contact during your state of security report. Offer to be available if any of them have any questions or wish to further discuss details of the report.
If you have an active board of directors, don't oversell cybersecurity threats. The board members already get it. Keep your reports comprehensive, strategic and easy to understand. Don't get into the minutia of security metrics.
If you have a passive board, your job is to get its attention. If a breach occurs and if you are not collateral damage, use it as an advantage to share your message. You can try fear, uncertainty and doubt but that may backfire. Map the cybersecurity threat message with the company's strategic objectives. Focus on those one or two C-level executives. Although supportive of the CIO and IT, cybersecurity is more of a necessary evil and part of doing business. Don't try to sell yourself; sell your message. Your message will inherently speak volumes about the information security program.
Ask the Expert:
Have questions about enterprise security? Send them via email today. (All questions are anonymous.)







