Are 14-character minimum-length passwords secure enough?
When it comes to minimum password length, 14-character passwords are generally considered secure, but they may not be enough to keep your enterprise safe.
The password has long been the most widely used mechanism for user authentication, but it has also long been the bane of security's existence by causing numerous attacks, hacks and breaches. In fact, the 2019 Verizon Data Breach Investigations Report reported 80% of hacking-related breaches can be linked to stolen and reused credentials.
If passwords are so insecure, why are we still using them? Alternatives are available, but organizations must consider not only how much stronger the security is, but also if they are cost-effective and user-friendly -- or, rather, user-accepted.
Fortunately, there are steps organizations can take to increase the effectiveness of passwords, from instituting minimum password lengths to mandating regular password resets.
What is the problem with passwords?
Passwords are fraught with security risks. In brute-force attacks, such as password spraying, hackers try to crack credentials by inputting multiple combinations of usernames and passwords into a program. In keylogger attacks, applications monitor keystrokes and enable hackers to potentially guess password combinations. Phishing and other social engineering attacks also threaten password security.
This article is part of
What is data security? The ultimate guide
Poor password hygiene leads to poor password security. Too often, users write down their passwords and store them in their desks or on their phones. Password reuse is another major concern: The third annual LastPass Global Password Security Report found employees use the same password an average of 13 times. Another threat is users create passwords that are not only easy for them to remember, but also easy for hackers to guess. These passwords are most likely already listed in a hacker's rainbow tables (more on them below) or in publicly available lists of passwords for credential-stuffing attacks. Also, commonly used passwords, such as 123456, password, qwerty and iloveyou, regularly show up in lists of commonly cracked passwords.
The password security challenge can also be linked to the sheer number of passwords users must remember. LastPass research reported the average business employee must remember anywhere from 25 to 85 passwords -- and that's just in the workplace. With so many credentials to remember, it's no surprise password hygiene is terrible. Combine these issues with the fact that so many applications and corporate systems require password updates on a regular cadence, and it's no wonder people forget their passwords, reuse them or create ones that are easy to remember.
What are the technical challenges of password security?
For obvious security reasons, modern applications and OSes don't store user passwords in cleartext. Instead, as a user resets her password, the alphanumeric characters entered are run against an encryption algorithm that creates a unique cryptographic hash value, which represents the password and is stored on the system in a file. When a user returns to access the system, she enters the same sequence of letters and numbers, and the system generates an on-the-fly hash sequence. This value is compared against the original hash file value for that user to determine if the password entered is correct.
In the past, hashing passwords was considered a safe approach because, even if a hacker was able to obtain a system's password hash file, the computational effort it would have taken to randomly type in passwords and match the result to the known hash values found in the system file was an impossible task. However, because of the value of this information and the exponential computational capabilities of today's computers, hackers often map every combination of password character sequences to their hash values -- starting with A, AA, AAA and through the entire alphanumeric sequence. These values are stored in publicly available tables called rainbow tables.
Rainbow tables take many hours of effort, but these types of endeavors are ongoing. Since initial attempts at acquiring hash values of passwords started, the tables have grown in scope and size to the point where it's likely that any password fewer than 12 characters in length likely has its hash value registered in a rainbow table somewhere. This means a nefarious person who acquires a system's hash file can simply attain a rainbow table for that OS or application and look up the hash values to uncover the users' passwords stored within.
As rainbow tables grow, passwords must become longer and more complex, making the effort required to obtain their values too onerous. This ongoing work to assemble rainbow table data may soon make minimum password length debates moot and is the main reason many experts consider passwords a poor choice to authenticate credentials for access to important and valuable data.
How to create stronger passwords
Despite their well-known risks and vulnerabilities, passwords are here to stay -- at least for now. It is up to organizations to boost their security. For example, enforcing a longer minimum password length on enterprise systems can help make passwords less susceptible to brute-force attacks.
1. Password length
What's a "good" or "secure" minimum password length? Many websites -- Facebook, Gmail and Amazon included -- require at least six to eight characters in a mix of symbols, numbers and uppercase and lowercase letters. This is far fewer than the 14-character password, which is often seen as cumbersome by consumers and employees.
2. Password complexity
When it comes down to it, focusing primarily on length won't get the job done. It's password complexity that is important. What can be done to increase password complexity, while making the task of using long passwords more user-friendly? The simple answer is by using passphrases. Instead of creating a long string of meaningless characters and numbers, people should use familiar sentences that create images in their mind, something humans find easier to recall, to remember their password.
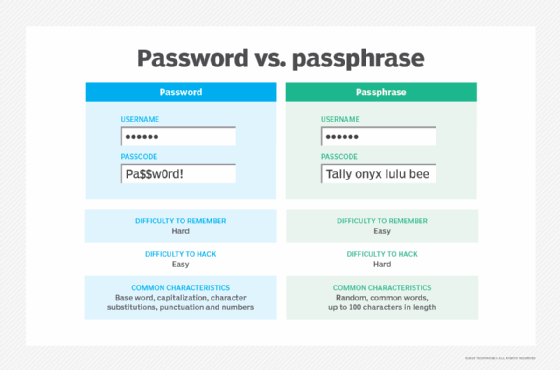
For example, if a user has a child in school, he might think of the phrase, "My child is on the fifth-grade honor roll." This can easily be translated into a password he would remember, such as Bobbys#1OnThe5thGradeHR. Or a person into music may think, "My favorite band when I graduated high school in 1998 was Nine Inch Nails," which can be made into the password N1998ILoved9InchNails. Both examples are complex and well past the 14-character password length. Shorter and unique combinations can be made as well; it just takes some imagination.
Password alternatives abound
If passwords aren't secure enough for your enterprise's needs, there are stronger alternative credentials methods available, including soft or hard tokens, biometrics and knowledge-based authentication. Single sign-on, which enables an employee to use one set of credentials for multiple enterprise applications, can also lessen the password burden. Two-factor or multifactor authentication also boosts password security. Enterprise password managers, available in software or service form from several vendors, can help by storing encrypted passwords to be used across applications or devices.






