
12_tribes - Fotolia
How to prevent network eavesdropping attacks
One of the biggest challenges of network eavesdropping attacks is they are difficult to detect. Read about prevention measures to help keep your network safe from snoopers and sniffers.
Network eavesdropping attacks, also known as network sniffing or network snooping attacks, occur when malicious actors take advantage of insecure network connections to exfiltrate data as it is being communicated.
Just as someone eavesdrops on a conversation between two people, network eavesdropping involves listening in on conversations across network components, including servers, computers, smartphones or other connected devices.
How network eavesdropping attacks work
In network eavesdropping attacks, hackers look for weak connections between clients and servers: those that are not encrypted, use devices or software that are not up to date or have malware installed via social engineering. By exploiting these weak connections, hackers intercept data packets traversing the network. Any network, web or email traffic, if not encrypted, can be read by the hacker.
Many times, hackers install sniffer programs. These legitimate applications, such as Wireshark, Snort or tcpdump, are often used by security teams to monitor and analyze network traffic to detect issues and vulnerabilities. However, these applications also can be used by bad actors to spot the same vulnerabilities and exploit them.
Types of network eavesdropping attacks
Network eavesdropping attacks can be passive or active. In a passive eavesdropping attack, the hacker or sniffer program only gathers intel on its target -- the data is never altered. Voice over IP (VoIP) eavesdropping is an example of a passive eavesdropping attack. During VoIP eavesdropping, a hacker or sniffer will infiltrate the network through a compromised VoIP device or via part of the VoIP infrastructure, such as a switch, cable or internet, and listen in on unencrypted VoIP calls.
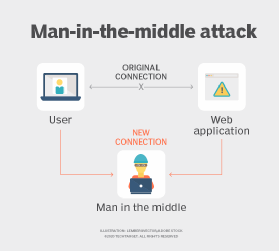
In active eavesdropping attacks, hackers insert themselves into the network and masquerade themselves as legitimate connections. In active attacks, hackers can inject, modify or block packets. The most common active eavesdropping attack is a man-in-the-middle (MitM) attack. MitM attacks usually infiltrate systems through malware or spoofing attacks, including Address Resolution Protocol, DNS, Dynamic Host Configuration Protocol, IP or MAC address spoofing. Once attackers get into the system via MitM attacks, they can not only capture data, but also manipulate and send it to other devices and users by purporting to be a legitimate party.
Network eavesdropping attack prevention
Unfortunately, detecting and preventing passive network eavesdropping attacks are extremely difficult, if not impossible, as there are no disruptions or changes to the network. Active attacks are easier to detect, but often, data is already intercepted by the time network changes are noticed.
As with most things security, an ounce of prevention is worth a pound of cure. Here's a rundown of the best ways to prevent network eavesdropping attacks:
- Encryption. First and foremost, encrypt email, networks and communications, as well as data at rest, in use and in motion. That way, even if data is intercepted, the hacker will not be able to decrypt it without the encryption key. For wireless encryption, Wi-Fi Protected Access 2 or WPA3 is recommended. All web-based communication should use HTTPS. Note, however, that while most data can be encrypted, network traffic metadata, such as endpoints and IP addresses, can still be gathered via a sniffer.
- Authentication. Authenticating incoming packets is key to preventing spoofed packets that are used to perpetrate IP spoofing or MAC address spoofing attacks. Use standards and protocols that provide authentication. Most cryptographic protocols, such as TLS, Secure/Multipurpose Internet Mail Extensions, OpenPGP and IPsec, include some form of authentication.
- Network monitoring. Security teams should constantly monitor networks for abnormal activity by using intrusion detection systems or endpoint detection and response software. Security teams should also use the same sniffer programs that nefarious actors use to detect vulnerabilities on the network.
- Awareness and security best practices. Educate employees about the risks of eavesdropping attacks and best practices to protect against them. Because many eavesdropping attacks involve malware, advise employees to never click links or download files they are unfamiliar with. Strong passwords that are changed frequently can prevent attackers from gaining entry via compromised credentials. Also, tell employees to avoid public Wi-Fi networks. These networks with readily available passwords -- if any at all -- are highly prone to eavesdropping attacks.
- Network segmentation. Segmenting the network can put certain data out of reach of a hacker. For example, separate critical infrastructure from financial and HR applications, and separate all of them from the guest network. Should one segment be compromised, the hacker would not be able to access the other segments.
- Security technologies. Firewalls, VPNs and antimalware are essential to thwart eavesdropping attacks. Using packet filtering, configure routers and firewalls to reject any packets with spoofed addresses.







