
frenta - Fotolia
How does a security portfolio help an enterprise security program?
A security portfolio shouldn't be used as an alternative to a reporting structure, but it can still be beneficial to enterprises. Expert Mike O. Villegas explains how.
I read recently that security portfolios are a better method than a reporting structure for an enterprise's security program. What is a security portfolio, and what does it look like for enterprises? What are the benefits and drawbacks of using that system over a traditional reporting structure?
A security portfolio is a way to model the state of security based on the investments made by an enterprise. In theory, they can be used to affect change in the organization based on the investments in tools and how they are used for controls.
However, controls do not manage risk. Risk manages what controls you use to mitigate vulnerabilities. This mantra has been the premise for information security professionals for many decades.
If you allow controls to govern how you protect critical assets, the likelihood is you will try to over control assets that may not matter. This can result in poor use of resources, time and effort. That does not mean controls are not important, but risk should drive how and why protection constructs are deployed.
The security portfolio does not have a direct correlation to the reporting structure for information security. Both are clearly critical to the success of the information security program, but there is no bifurcation issue.
Information security needs to be based on proven information security frameworks, such as the NIST cybersecurity framework, ISO 27000, the COBIT Security Framework and many others.
Within these frameworks, the security portfolio -- investments made in tools, protection solutions, managed security services and resources -- is based on risk and compliance. How these investments are used depends on internal skills, empowerment for deployment and positioning (reporting structure).
The following diagram describes the information security program of an enterprise:
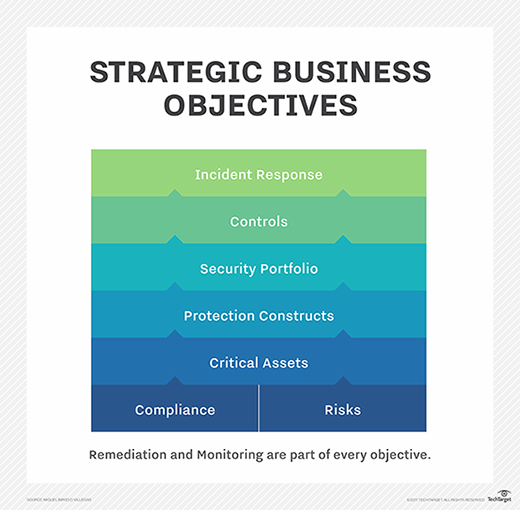
The key point in this diagram is that the foundation of the information security program needs to be based on the enterprise's strategic business objectives. Without this, the information security program will be technology-based, and you may find protection schemes disjointed and not relevant. Risks and compliance drive the enterprise's protection of the critical assets they identify.
The protection constructs are based on the technology (i.e., legacy, cloud, database, web, mobile, etc.) The security portfolio makes up the investments made for security software, appliances, processes and staff. The controls are the protection methods used to mitigate vulnerabilities based on risk and compliance. The incident response tests the controls. Monitoring ensures the controls are working effectively, and remediations correct any control deficiencies. It is an iterative process, but one that is ultimately based on the business.
Lastly, the reporting structure is incidental to the c-level executive. This means that whether information security reports to the CEO or to the CIO doesn't depend on the reporting structure or the security portfolio, but on the c-level executive.
Information security needs to be independent of influence from management to implement, monitor and protect corporate assets. But if the executive does not understand or cannot champion the information security program, it will be difficult to deploy or acquire the tools, resources or to be empowered to implement the right level of protection for the enterprise.
Ask the Expert:
Have questions about enterprise security? Send them via email today. (All questions are anonymous.)





