
Getty Images/iStockphoto
Is VPN split tunneling worth the security risks?
Enabling VPN split tunneling may increase speed and decrease bandwidth use and costs, but it also increases the number of security vulnerabilities faced.
As employees continue to work both from home and outside the confines of the main office, more enterprises are relying on VPNs to ensure secure remote access connections. And, when it comes to VPNs, the decision to use split tunneling depends on an organization's specific business and security needs.
What is VPN split tunneling?
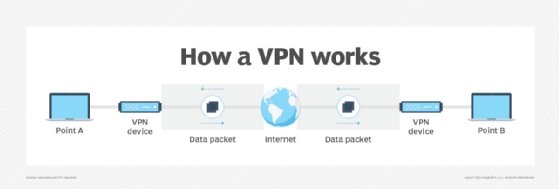
Many companies use a corporate VPN to provide secure network access for remote employees. A VPN is designed to maintain the security and privacy of an organization's network -- and the employees connecting to it -- by using tunneling protocols to encrypt and send data from one system to another. A VPN's tunnel enfolds the data passing between an employee's computer and the remote VPN server.
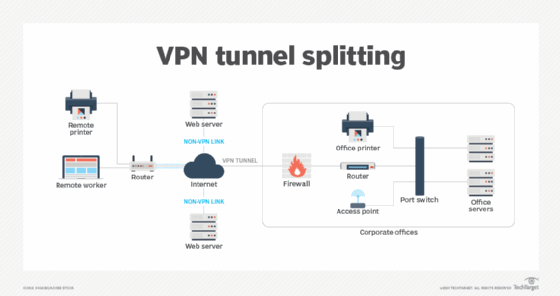
Split tunneling, a feature on some VPNs, enables VPN users to direct one portion of traffic through the VPN tunnel, while sending another portion of traffic through the local network's router and internet service provider (ISP).
For example, a remote employee working from home can establish a VPN connection that sends all corporate and personal system traffic through a secure VPN tunnel to the corporate network.
With split tunneling enabled, it can be configured so corporate data is sent through the secure VPN tunnel and all personal traffic is sent through the local router and ISP. Which traffic is pushed through the VPN and which is handled by the ISP depends on the VPN service and the organization. Administrators configure the VPN tunnel to be network-aware, and the user's VPN client then makes intelligent routing decisions based on each packet's destination IP address. If a packet is headed to a system on the workplace network, it gets routed through the VPN tunnel. If it's destined for an external site, it goes through the user's router directly to the destination host.
Split-tunneling security risks
Split tunneling introduces some security challenges. Any data that does not traverse a secure VPN is not protected by the corporate firewall, endpoint detection and response system, antimalware and other security mechanisms, so it may be accessible and/or intercepted by ISPs and malicious hackers. Employees surfing the web are also not protected by the VPN's encryption capabilities, exposing them to phishing, malware, and drive-by and man-in-the-middle attacks.
In addition, if an employee downloads malware, there is a chance an intruder may be able to access the corporate network using the employee's credentials.
VPN split tunneling also limits a company's ability to control file sharing. This is especially concerning if malicious insiders exfiltrate corporate data. Any controls preventing the copying of data through the VPN would be ineffective if conducted on the public tunnel. Also, companies may encounter compliance challenges because traffic on the public tunnel cannot be monitored.
Split tunneling is even more risky when employees connect through public or insecure networks, such as coffee shop Wi-Fi, instead of home networks.
Benefits of split tunneling
With potentially serious security risks, shouldn't split tunneling be avoided? Not always -- there are some uses for it.
If a VPN does not support split tunneling or the feature is disabled, employees may not be able to access local and international internet services simultaneously. Split tunneling's separation enables this.
Plus, transmitting all user data and traffic through a VPN uses a lot of bandwidth, creating a potential bottleneck. Sending traffic through the VPN to on-premises infrastructure and back to the internet again can slow down internet connections, hinder employee productivity and become quite costly -- especially if hundreds or thousands of users connect to the VPN. With split tunneling enabled, only the data that needs the security and privacy provided by the VPN will be transmitted. Smaller workloads equate to less bandwidth use and fewer backups.
Another common challenge is employees connected to a VPN without split tunneling may not be able to access devices and systems on their LAN -- for example, a local network printer or privately addressed file server. Split tunneling provides access to these devices and systems.
To split tunnel or not to split tunnel
Again, the decision to use split tunneling depends on an organization's specific business and security needs. If a company must monitor all traffic from all devices -- for example, a healthcare organization -- split tunneling is not advised. Likewise, if all remote device traffic must be monitored for auditing and compliance reasons, split tunneling should not be used.
If the goal is to secure only corporate traffic between remote users and the workplace, it's fine to use split tunneling. However, be sure to educate employees about which traffic passes through the protection of the VPN and which doesn't. Create a corporate policy for employees and third parties connecting to the network that offers a list of approved equipment and spells out the security mechanisms required to secure the equipment, such as personal firewalls and antimalware. Conduct regular security awareness training to educate users about the risks of VPN split tunneling and how to mitigate them.
It is important to note that not all VPNs offer split-tunneling features. Also, some VPNs have default split-tunneling configurations. Administrators should explicitly configure VPNs to send corporate data and application traffic through the VPN tunnel and other traffic through the employee's home router and ISP.
If split tunneling is used, make sure any devices connecting to the VPN are compliant with the corporate policy, patches are installed and up to date, and antimalware is running. Admins may also consider using network segmentation on VPN users and limiting access based on the principle of least privilege. Egress protections and web filtering should also be used. In addition, check to see if any security software currently in use works with VPN split tunneling and can help mitigate its risks.
Expert Mike Chapple contributed to this article.








