
Getty Images/iStockphoto
Defining policy vs. standard vs. procedure vs. control
Infosec pros may have -- incorrectly -- heard the terms 'standard' and 'policy' used interchangeably. Examine the differences among a policy, standard, procedure and technical control.
At first glance, policies, standards, procedures and technical controls may appear more similar than they are. But these terms are not interchangeable -- each refers to separate and distinct aspects of IT operations. It is critical security practitioners understand their differences and how they are interrelated.
Here, uncover the differences among a policy, standard, procedure and technical control, as well as how they may show up in the infosec space. While it may seem trivial to dwell on how to craft formal definitions for each term, it is in everyone's interest -- and in the interest of the organization's security -- to understand the language of IT operations.
What is a policy?
Policies are long-term, high-level management instructions on how an organization is to be run and are generally driven by legal concerns, such as due diligence and regulations. This is one of the main differences between a policy and standard: Policies act as a statement of intent, while standards function as rules to achieve that intent.
Policies reflect an organization's goals, objectives and culture and are intended for broad audiences. They are mandatory and apply to everyone, from employees to contractors to temporary workers. Any exception to a policy requires special approval and should be documented. In fact, the stipulation that each policy exception must be documented is a policy in itself.
Policies drive standards, procedures and technical controls. For example, consider an organization with a policy that passwords must be used to log in to corporate devices. This instruction may necessitate subsequent standards for passwords, procedures for changing passwords and technical security controls that execute the policy and procedures.
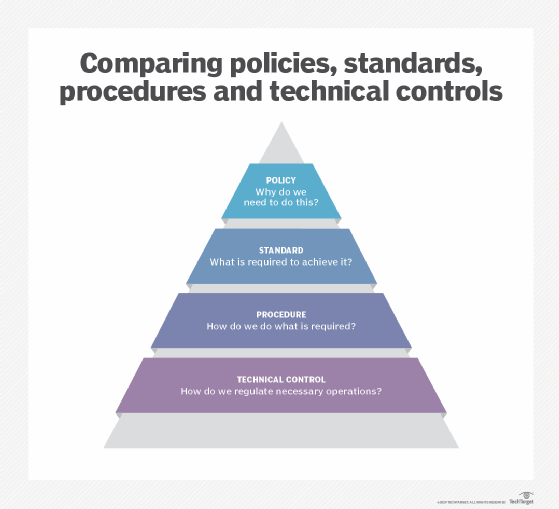
What is a standard?
As mentioned, standards define the processes and rules used to support a policy, such as system design models or specific software or methodologies. Standards can be directed to a broad audience or limited to specific groups or individuals. For example, software developers may use coding standards in their work. Coding standards provide solid programming practices and can enable easier error detection.
Standards may be of limited duration and reflect organizational or environmental changes. Like policies, standards are mandatory and require special approval if a standard is not to be followed.
Continuing the password policy example above that requires passwords on all corporate devices, many organizations enact password standards that require passwords be constructed of eight or more alphanumeric characters and symbols or that a passphrase contains fewer than 100 characters.
What is a procedure?
Procedures are specific instructions or ordered tasks for performing some function or action. Procedures are often of short duration, are mandatory and reflect organizational or environmental change. If an organization recently experienced a data breach or other security incident, for example, it should implement a new password procedure that may, for instance, force a password reset, where employees must type their current password in one field and then enter a new, unique password in a separate field.
Various departments have their own internal procedures related to their employees' responsibilities and workflows. HR staff members may have a procedure for interviewing a job candidate, for example, while security professionals follow procedures for performing system backups or setting up user accounts.
What is a technical control?
Technical controls are mechanisms used to regulate operations to meet policy requirements. For example, an organization with a BYOD policy may incur additional risks due to potentially insecure messaging applications and user error. Security teams may implement technical controls to mitigate risk, including mobile device management or mobile application management software. Additional technical controls may include firewalls, authentication mechanisms or antimalware.
Technical controls can be volatile, particularly in distributed environments where a hacker -- or even a determined user -- may find and exploit security gaps in technology. Managing and updating technical controls are crucial tasks for infosec professionals.





