
Account lockout policy: Setup and best practices explained
Organizations must carefully balance security and UX when implementing account lockout policies.
After decades of use, account lockout policies continue to be a simple yet effective way of thwarting authentication-based attacks. This best practice of setting parameters for locking users' accounts after too many login attempts helps prevent malicious actors from infiltrating networks.
When setting an account lockout policy, however, security, network and system admins must balance security and UX. It's important to keep attackers out, but also not to frustrate legitimate users -- and overload the help desk with reset requests -- when they type in an incorrect password.
Let's look at the main elements of an account lockout policy and review best practices for creating and implementing effective account lockout policies for your organization.
What is an account lockout policy?
An account lockout policy temporarily blocks access to a user account when there have been too many failed authentication attempts for that account. Most OSes and domain services, such as Active Directory, have settings for configuring automatic account lockouts. Many websites, services and other online resources also support automatic lockouts.
Benefits of an account lockout policy
The primary benefit of account lockout policies is preventing attackers from gaining unauthorized access to user accounts. It prevents brute-force attacks, which are attacks in which malicious actors try hundreds, thousands, millions or even billions of passwords to log into users' accounts. Types of brute-force attacks include credential stuffing, dictionary attacks, password spraying and rainbow table attacks. With an account lockout policy in place, attackers find themselves unable to make another attempt for some period of time after just a few failed logins.
Account lockouts can also indicate a pending cyberattack, providing an early warning sign of a potential incident.
How to define an effective account lockout policy
The main challenge with using account lockout policies is that they can inconvenience or disrupt legitimate users. A user who accidentally enters the wrong password a few times, for example, would trigger an account lockout. Likewise, an attacker could lock out a legitimate user from their account with password guessing, or do password guessing against many of an organization's accounts and lock them all out.
Defining an effective account lockout policy is all about balancing security and availability. Most account lockout policies support the following options:
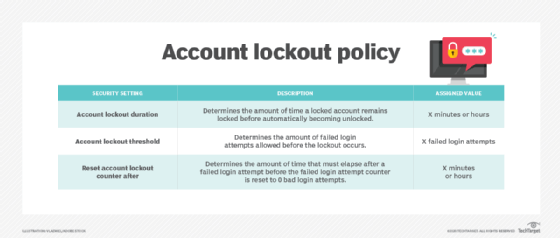
- Account lockout threshold. This is the number of consecutive failed authentication attempts for an account that should trigger a lockout. Common default values for this setting are three, five or 10 failed login attempts.
- Account unlocking options. There are two options after an account lockout:
- Keep the account locked until an authorized admin receives a verified request to unlock it.
- Lock the account for a period of time and then automatically unlock it.
- Account lockout duration. This is the amount of time an account remains locked after exceeding the lockout threshold. Common default values are 15, 20 or 30 minutes.
- Account lockout reset. This is the amount of time after which the number of login attempts resets. Common default times are 15, 30 and 60 minutes.
Some systems also support a variant on account lockout known as authentication backoff. After a few failed authentication attempts for an account occur, the system adds a short delay -- usually in seconds -- before the next attempt can be tried. Every time another failed authentication happens, a longer delay is introduced, with delays eventually reaching minutes long. This can provide strong protection against password-guessing attacks without significantly inconveniencing users who make a few mistakes.
Admins should include the details of the account lockout policy within the organization's password policy and inform users about policy settings during security awareness training.
How to implement an account lockout policy
Implementing an account lockout policy can inadvertently lock out legitimate users and even disrupt operations, so it's best done gradually. Follow these steps for an organized, efficient policy rollout:
- Decide how to balance preventing unauthorized access and enabling account availability. In most situations, setting a failed login attempt threshold of 10 or using authentication backoff is a reasonable approach. However, some highly sensitive systems might require a stricter account lockout policy. Certain situations should not use account lockouts -- for example, operational technology accounts that must always be accessible for human safety reasons.
- Implement a pilot of the policy. Depending on the system's capabilities, admins might want to implement the policy for a subset of users at first. This enables admins to gather users' feedback and monitor the pilot for unexpected issues. If a system cannot support this type of pilot, an alternative is to implement a lighter version of the policy, such as introducing a failed login attempt threshold of 20, and then changing that threshold over time to finally reach the target value.
- Fully implement the policy. Once admins are satisfied that any issues identified during the pilot have been addressed, they can fully implement the account lockout policy. Carefully monitor the system for any unexpected issues and be ready to roll back the settings if they inadvertently disrupt operations.
Karen Scarfone is the principal consultant at Scarfone Cybersecurity in Clifton, Va. She provides cybersecurity publication consulting to organizations and was formerly a senior computer scientist for NIST.







