Identity Security and zero trust are inextricably linked. A zero trust framework relies on the organization’s ability to continuously and accurately authenticate each identity—whether person or device—and know what privileges are authorized, reducing the risk of compromise, lateral movement and data exfiltration.
Exclusive research by Enterprise Strategy Group found that 92% of cybersecurity professionals surveyed believe identity device trust and identity management are important to building a successful zero trust framework, and 46% said identity management is “critical.”1
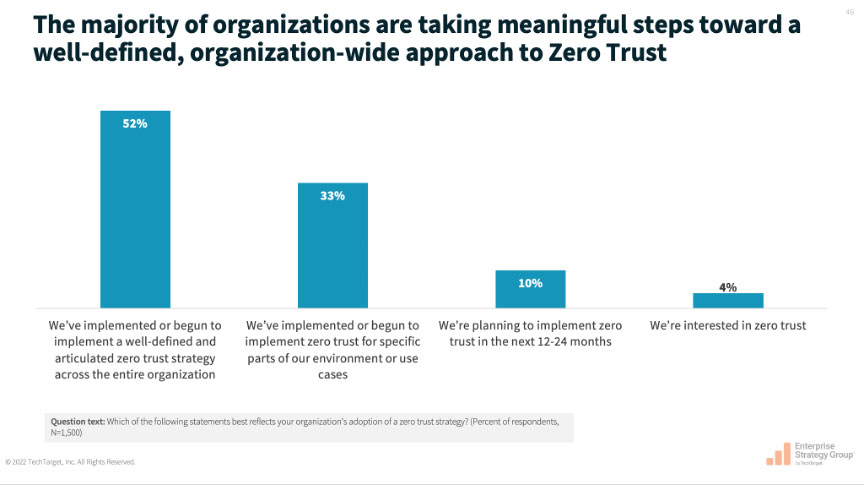
Because Identity Security is a foundational element of zero trust, organizations have an opportunity to accelerate their broader use of zero trust frameworks by leveraging an Identity Security platform. This is becoming more important at a time when most organizations are moving toward an organization-wide approach to zero trust, as shown in Figure 1.2
What to look for in a solution
A modern, cloud-based Identity Security platform can set the foundation for an organization-wide approach to zero trust. However, not all Identity Security platforms are created equal. When evaluating potential platforms to facilitate zero trust, here are some of the key features and functions to look for.
Intelligent privilege controls. With a platform centered on intelligent privilege controls, organizations can enable zero trust by securing credentials wherever they exist and enforcing least privilege. Key capabilities to look for include standing and just-in-time access, session isolation and monitoring, elevation and delegation, and credentials and secrets management. The platform should be able to authenticate users with adaptive access based on context.
Seamless and secure access for all identities. The platform should offer all identities just-in-time secure access to services, applications and resources when needed, at any location and on any device. It should be able to discover all human and machine identities that have access to resources, with centralized, end-to-end visibility to discover unknown threats, such as those with overprivileged identities or risky permissions. Dynamic authorization can be used to enforce just-in-time access.
Flexible identity automation and orchestration. With Identity Security, IT can centrally secure and manage access, leveraging DevOps and automation tools throughout the lifecycle of every identity. Capabilities should include permissions and entitlements, directory and federation services, and central securing of application credentials. Identities should be given the right level of permission to perform their roles, with the flexibility to remove those permissions when they are no longer necessary.
Real-time threat detection and prevention. The platform should incorporate ongoing and automatic monitoring, detection and threat mitigation. Cyber teams should be able to easily and automatically detect identity threats and apply the appropriate security controls based on the risk profile. This not only enables zero trust but also empowers the team to be faster and more agile in stopping harmful threats from compromised identities.
Empowerment of workforce identity. IT must be able to deliver a seamless, trusted and frictionless user experience. With the right Identity Security platform, users can take advantage of simple and secure access to business resources using single-sign-on, authentication and passwordless capabilities, as well as adaptive multifactor authentication.
When it comes to delivering an Identity Security platform to facilitate and accelerate zero trust, CyberArk offers advantages other solutions are hard-pressed to match. These include seamless access for all identities, intelligent privileged controls, flexible identity automation and orchestration, and real-time threat detection and prevention—all in a unified, holistic platform.
For more information on how your organization can leverage Identity Security to facilitate zero trust, please review the resources on this site and visit CyberArk.
1 “Identity Security Maturity Model Survey,” CyberArk and Enterprise Strategy Group, September 2022
2 Ibid.

