
kovaleff - Fotolia
How to use Oracle DBSAT to do a database security assessment
The Oracle Database Security Assessment Tool is free software that checks the security of databases. Here are the steps involved in using DBSAT to collect data and create reports.
In January, Oracle released the latest version of the Oracle Database Security Assessment Tool, or DBSAT. All database administrators should be highly concerned with security and should do their best to safeguard corporate data, and Oracle DBSAT can help with that -- without costing you anything extra.
DBSAT will scan your Oracle Database environment and present its findings on the database's configuration and a variety of other aspects -- for example, user accounts and access privileges, database auditing policies, and data encryption. Via a new DBSAT Discoverer module added in release 2.0.1, it will also identify sensitive data stored in the database, including personal, financial and health data.
Database administrators (DBAs) should run DBSAT multiple times during the course of a year to ensure that they're securing their Oracle databases as well as they can, and to get recommendations on how to mitigate potential security risks that the software detects. DBSAT is a command-line tool that can be used with both on-premises and cloud databases, and Oracle says it has a negligible performance impact on databases when it's running.
While Oracle touts DBSAT as a free utility, it does require you to have an Oracle support contract and a user account on the My Oracle Support web portal to use the tool. If you do, you can download DBSAT from the portal via My Oracle Support note 2138254.1. Click on the I AGREE link there, and the will download begin. Copy the ZIP file containing the tool to the intended database server and extract its contents to a DBSAT directory that you've created on the system.
Two steps to check database security
Using Oracle DBSAT to assess a database's security levels is a two-step process: collecting the data and then generating a report. I'm going to walk you through an example of that process.
To start the data collection, enter the connection string and the output file for what the tool collects:
dbsat collect system /home/oracle/dbsat/orcl.zip
In this case, DBSAT is connecting to my local database as the SYSTEM user. You can also connect to remote databases by specifying @tns_alias if desired, but Oracle recommends that you run the DBSAT Collector locally on the database server because it executes operating system commands in addition to running SQL statements against the database. The tool does so to collect process and file system data that the database itself can't provide. As a result, you won't get a complete set of data if you connect the tool to a remote database.
If you don't want to use the SYSTEM user account to collect the data, the DBSAT user guide posted on the Oracle Technology Network site shows you the required privileges for running the collection routine.
Also, if the database password isn't specified in the connection string, as above, you'll be prompted to enter it during execution. You'll also be prompted to create a password for the resulting JSON output file to protect its contents from prying eyes.
Once Oracle DBSAT has finished its collection work, the next step is to unzip the output file using the password you created for it:
[oracle@myhost]$ unzip orcl.zip
Archive: orcl.zip
[orcl.zip] orcl.json password:
inflating: orcl.json
Next comes the reporting part of the process. The DBSAT Reporter is a Python program that requires version 2.6 or higher of the open source programming language in order to run. It can be run on any system, including a desktop or laptop device.
To make sure that Python is installed on the system, enter this command:
[oracle@myhost]$ python -V
Python 2.7.5
In my example, the second line shows that a suitable version of Python is in place. We're now ready to generate the security assessment report.
dbsat report orcl
The report generation routine will prompt you for another password, which will be used to protect the report's contents. Unzip the resulting file, specifying the password you've set up. You can create reports in HTML, Excel, text or JSON formats -- the latter another of the new features in release 2.0.1.
I opted for an HTML file, which can be opened with any browser.
What you get from Oracle DBSAT
The report I received contains a summary of DBSAT's findings, as shown below:
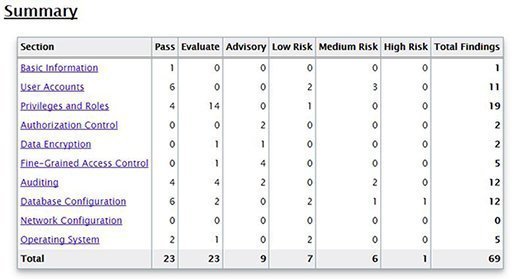
I have one high-risk finding and six medium-risk findings that DBSAT flagged in three categories. The lone high-risk one is in the Database Configuration category; clicking on the hyperlink will take me to that section in the report. The screenshot below shows my high-risk item:
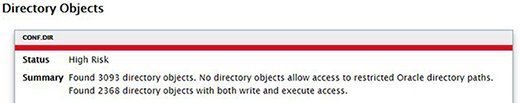
For me, this is an acceptable risk, and removing those directory objects will break application functionality. Leaving things as is in the database is fine so long as we understand the risk, which we now do thanks to DBSAT.
The next screenshot shows another finding that I wasn't aware of until I ran the tool:
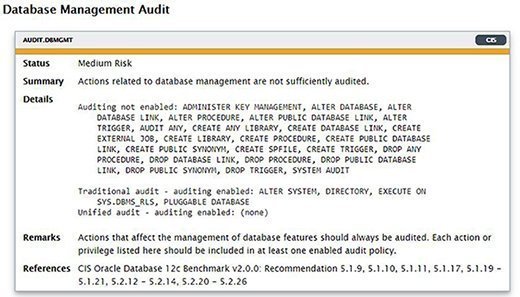
The information presented here gives me an action plan for improving my database security, and that's the whole point of using DBSAT. There often will be cases where it suggests something that you can't implement for any number of reasons, but the tool may also identify security issues that you didn't know about and provide useful recommendations on how to address them.
I've shown you a very simple example of how to use Oracle DBSAT. The tool offers many other options for both the collection and reporting phases, as well as for identifying sensitive data with the Discoverer module.
I plan to run DBSAT at least twice each year and use the results to plan steps I can take to improve the security posture of my databases. You likewise should start improving your Oracle database security before it's too late.








