
Andrea Danti - Fotolia
What to know about VPN termination
Network teams make several decisions when designing a secure VPN. One of those is where in the network, logically, they will terminate the VPN tunnels.
Multiple choices are available for VPN termination, but which ones make sense for your network?
VPNs are encrypted network tunnels that secure communications channels between sites. A site can be a branch that contains hundreds of people, or it can be a home office or mobile user with a laptop or mobile device, like a phone or tablet.
A branch site will typically use a permanent IPsec VPN that's up all the time. A mobile user will typically use a dynamic VPN based on Secure Sockets Layer or Transport Layer Security that's up only when connectivity is required. Remote sites typically connect to one or more central sites, usually the organization's corporate headquarters or regional offices.
Central site VPN termination
Network teams have several choices regarding where to terminate the central end of VPN tunnels.
Inside the site's firewall. This places remote devices inside the organization's secure perimeter. If the firewall can't decrypt the remote site's traffic, it can allow malware into the central site. This termination point is best suited for a remote branch that's using IPsec and device security scanning technology to prevent a remote computer from attacking corporate resources.
Outside the site's firewall. With this type of VPN termination, VPN traffic is decrypted outside the firewall, which enables the firewall to monitor and act upon traffic from the remote site. However, internet-destined traffic may not traverse the firewall, leaving the remote systems vulnerable to attack.
In a demilitarized zone (DMZ) network between two firewalls at a site. Terminating a VPN tunnel in a DMZ between firewalls is more secure than the above approaches because the external firewall protects the remote site systems, while the internal firewall protects the corporate systems.
On a site's firewall. Many firewalls include VPN termination, enabling the firewall to see the unencrypted traffic, while protecting the endpoints at both the remote and central site.
Remote site VPN termination
A remote site can use a single tunnel or a split tunnel configuration for VPN termination.
Single tunnel. In this configuration, a single tunnel sends all traffic via the tunnel to the central site, even if the remote site has good internet connectivity. This means all traffic to and from the remote site can go through corporate firewalls and security monitoring systems.
Split tunnel. A split tunnel configuration sends corporate traffic via the VPN and sends internet-destined traffic directly.
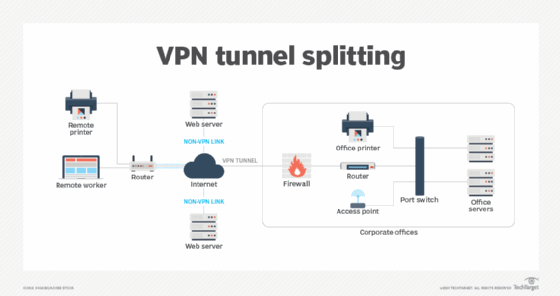
This method opens a potential security hole but is attractive for remote worker access to SaaS offerings, like Office 365 and Salesforce. Some DNS providers, such as Cisco Umbrella, enable direct access only to authorized internet services and require that all other connections, like browsing, go via the corporate site, where security services can protect the organization.
Look to the experts
VPN requirements depend on a number of factors, including the devices that are being deployed, the underlying network infrastructure and security requirements. It pays to consult with network security and VPN experts to make an informed decision on the specific technology to employ. Don't be surprised if multiple technologies are recommended to provide defense in depth.







