
Getty Images
Types of Nmap scans and best practices
Nmap scanning helps network teams with network reconnaissance and vulnerability discovery. Common types of scans include TCP SYN, OS detection, vulnerability and version detection.
All network infrastructures are at risk, due to sophisticated hackers and cyber threats. Bad actors can discover and exploit vulnerabilities, ruining a company's reputation and causing a loss of ROI. Thwarting attacks takes time, strategy and skilled teams.
Network engineers have many tools at their disposal to combat network threats. One such tool is Nmap, or Network Mapper. Nmap is a free, open source and cross-platform tool used for network discovery and audits. The tool supports scanning options and automated scripts to perform network reconnaissance and discover vulnerabilities.
Nmap provides the following three primary functionalities:
- Host discovery. Shows detailed information about every active network and each IP address.
- OS detection. Displays a list of active hosts and identifies the OS of every connected device.
- Port scanning. Helps identify security vulnerabilities.
By discovering devices, detecting OSes and scanning ports, Nmap identifies potential points of entry for cyber attacks. This information is useful for audits, making Nmap a versatile a tool for network administrators, pen testers, ethical hackers and even malicious hackers.
One of the most powerful features of Nmap is Nmap Scripting Engine (NSE). NSE enables users to write scripts to automate various network tasks. Nmap uses Lua, an embedded programming language, for writing scripts.
Nmap scanning techniques
Lockheed Martin, a well-known defense company, developed the Cyber Kill Chain model to trace the stages of a cyber attack. The first stage is reconnaissance. Network teams conduct network reconnaissance when performing network scans, and bad actors use it to gather information about attack targets. Nmap is a common tool used during the reconnaissance stage.
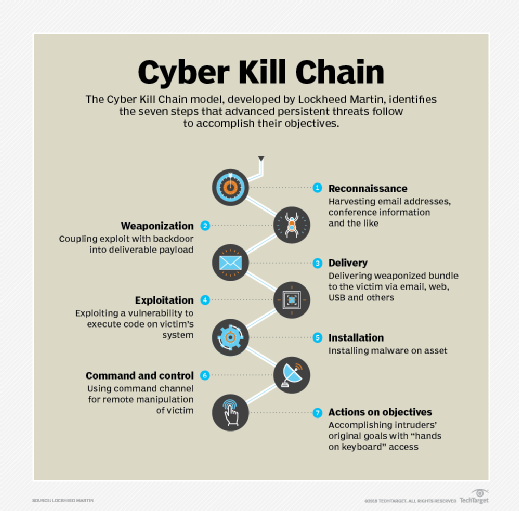
Conducting a scan helps determine what is running on a computer or network, such as opened ports, services and applications. Nmap establishes a TCP connection using Internet Control Message Protocol, TCP or User Datagram Protocol messages to gather information during the scan.
Nmap offers various scanning techniques. Here are four of the most common types of scans. For more advanced scans, network admins can use the Lua programming language within Nmap to write scripts.
1. TCP SYN scan
A TCP SYN scan is a stealth scan used to determine if ports on a target system are open, closed or filtered. Nmap sends a SYN packet to the target and waits for a response. If the target responds with a SYN/ACK packet, the port is considered open and ready to establish a connection. These connection attempts might not appear in logs, depending on network configurations. If the target responds with an RST packet, the port is closed.
Here is the command to perform a TCP SYN scan:
sudo nmap -sS <<Target_computer_ip_address>>
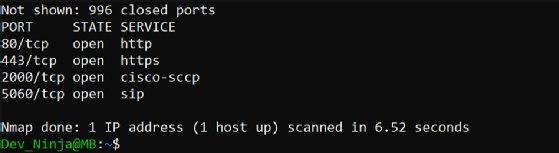
After the scan, the screen displays information about the port, state and services, as seen in Figure 2.
2. Version detection scan
A version detection scan gathers details about the services and applications running on identified open ports. The scan sends probes to open ports and receives responses from the services on those ports, garnering information about the type of services running.
Here is the command to run a version detection scan:
sudo nmap -sV <<Target_computer_ip address>>
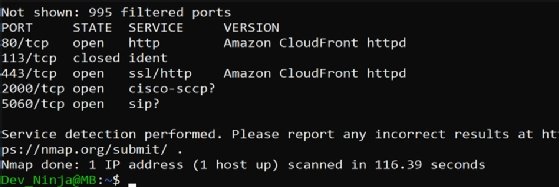
In Figure 3, the version detection scan displays a version of Amazon CloudFront with Apache HTTP Server, a web service that speeds up the distribution of static and dynamic content, running on open ports.
3. OS detection scan
An OS detection scan discovers which OS a target network or computer is running. Nmap sends TCP packets with specific characteristics, probes to the target host and determines the OS based on the host's responses. Advanced options of the scan can also detect the specific OS version and potential security risks. This information is useful during network reconnaissance.
Here is the command to run an OS detection scan:
sudo nmap -O <<Target_computer_ip_address>>
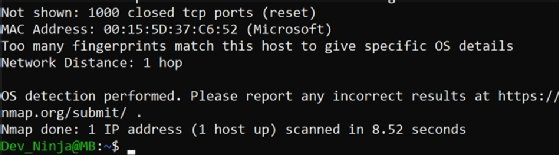
In Figure 4, the scan discovered a Microsoft OS.
4. Vulnerability scan
A vulnerability scan detects Common Vulnerabilities and Exposures (CVEs) to discover if a target is vulnerable to attacks. Use -Pn to skip a ping scan, and add --script vuln to run vulnerability detection scripts against the target host.
Here is the command to run a vulnerability scan:
nmap -Pn --script vuln <<Target_computer_ip_address>>
The scan shows the Samba heap overflow vulnerability, CVE-2012-1182, on a Windows 10 system. This information is helpful for network admins to know what is happening on a network or target computer and avoid data leaks with vulnerable systems.

Best practices for network vulnerability discovery
Some companies might prohibit network scanning unless they have an agreement or defined scope with the team performing the scans. Additionally, each country has its own laws and security frameworks. Network admins should always ensure they have proper authorization before running Nmap scans on a network, as unauthorized scanning can lead to legal consequences.
Here are some best practices for successful network vulnerability discovery:
- Choose the right tool. The first step before conducting a scan is to choose a tool that suits your needs. Nmap is commonly used due to its scan accuracy.
- Plan the scan. Always communicate with stakeholders before conducting a scan. It's possible to receive unexpected results without clear goals, scope and duration.
- Run the scan. After planning, choose the type of scan, the targeted IP address, the IP address range -- if it's for the entire network -- and vulnerabilities to detect.
- Scan frequently. Always refer to company policy to plan how often -- and what -- to scan. Is the scan weekly or monthly?
- Analyze the vulnerabilities. Always review the scan and assess which CVEs pose the most risk of data leaks based on their severity.
- Document the scan. After the scan, it's paramount to document. Each scan contains similarities, and documentation helps teams understand previous and future scans.
Nmap is a well-known tool for detecting network vulnerabilities. Network teams can take advantage of the tool by defining a scope for accurate scans, talking with different stakeholders and measuring results for safer networks.






