The 4 different types of wireless networks
The four types of wireless networks -- wireless LAN, wireless MAN, wireless PAN and wireless WAN -- differ in size, range and connectivity requirements.
Wireless technologies have grown in popularity and require the right type of wireless network to support them. It's important for organizations to choose the right type of wireless network, as each has its own functions and use cases.
The different types of wireless networks are the following:
- Wireless LAN (WLAN).
- Wireless metropolitan area network (WMAN).
- Wireless personal area network (WPAN).
- Wireless WAN (WWAN).
Each wireless network requires different equipment and connections, and covers a range of areas -- from short-range personal device connections to large areas that accommodate multiple connections.
1. Wireless LAN
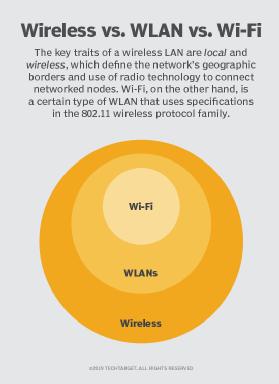
WLANs provide internet access within a building or a limited outdoor area. WLANs support a variety of devices that use radio waves, including laptops, smartphones, tablets and IoT devices. Homes and offices first used WLANs, but its use has since expanded to include stores and restaurants. Since WLANs rely on radio transmissions instead of wired connections, their range is limited to a single business or campus.
WLANs operate using radio frequency (RF) waves and various wireless protocols. The most common protocol is the 802.11 standard, also known as Wi-Fi. While the two terms are often used interchangeably, Wi-Fi is only one type of WLAN.
WLAN configurations are either ad hoc or infrastructure. Endpoint devices on an ad hoc WLAN communicate directly without needing an access point (AP).
Infrastructure WLANs operate with APs, which broadcast a wireless protocol, such as Wi-Fi. For example, a simple home network design connects a modem to a local service provider's cable or fiber. A wireless router connects to the modem and receives its signal, which it then broadcasts to devices. In this case, the router serves as the wireless AP.
Office networks also use the infrastructure model but in a more complex manner. Large offices require multiple APs, which are usually mounted on the ceiling. Each AP connects to the office backbone network with a wired connection to a switch and broadcasts a wireless signal to the surrounding area.
APs coordinate support for users around the office to maintain open, connected sessions between APs. For example, as users move around, APs will reestablish connections to the nearest point to maintain continuous and seamless connectivity.
2. Wireless MAN
Wireless metropolitan area networks provide broadband internet access to people across larger areas compared to WLANs. These networks cover up to 50 kilometers -- approximately the size of a city. However, despite its name, a WMAN can also provide coverage to rural areas. WMAN connections are either point-to-point or multipoint.
WMANs operate on RFs and primarily use the 802.16 wireless standard, also known by the IEEE as WirelessMAN and generally as WiMAX. WiMAX uses both licensed and unlicensed bands and supports a larger range of frequency bands.
WMAN principles are the same as those of WLANs. APs connect to the internet and broadcast wireless signals throughout the coverage area from the sides of buildings or on telephone poles. Users connect to their desired destination via the nearest AP, which forwards the connection to the internet.

3. Wireless PAN
Wireless personal area networks cover a limited area -- typically up to 10 meters. It connects individual user devices to each other. WPANs require little infrastructure and often include smaller personal devices. Examples of devices in a WPAN include the following:
- Mobile phones.
- Laptops and computers.
- Wireless computer devices, such as a keyboard or mouse.
- Wireless headphones.
- Wearable smart devices.
Common WPAN protocols include Bluetooth and Zigbee. Bluetooth enables hands-free phone calls, connects a phone to earpieces and transmits signals between smart devices. Zigbee connects stations along an IoT network. Infrared technology remains limited to line of sight, such as TV remotes connected to televisions.
4. Wireless WAN
WWANs use cellular technology to provide wireless access outside the range of other wireless networks. This type of network has an unlimited range and connects networks across large geographical areas. The largest WWANs have a worldwide range and enable user mobility.
WWANs are particularly adept at reaching areas wired networks can't. Since WWANs use cellular technologies such as 4G LTE and 5G, they operate using cell towers, which are available nearly everywhere within the U.S. and most other countries.
However, users aren't limited to making phone calls; WWANs also use cellular technology to enable speech or data transfer. Users can also connect to the internet to access websites or server-based applications. This works by routing user connections to the nearest cell tower, which then connects to either another tower or the wired internet.
Editor's Note: This article was originally written by David Jacobs and expanded by Nicole Viera to reflect industry changes and improve reader experience.
David Jacobs has more than 30 years of networking industry experience. He has managed leading-edge hardware and software development projects as well as consulted Fortune 500 companies and software startups.
Nicole Viera is assistant site editor for Informa TechTarget's SearchNetworking site. She joined Informa TechTarget as an editor and writer in 2024.





