
Getty Images
The steps and benefits of DNS service audits
Network administrators should perform DNS audits periodically and after major network changes. Routine checks can help teams to plan for future upgrades.
Name resolution is an essential component of network deployment. Name resolution management is one of the most important responsibilities for a network administrator. Regular audits of DNS servers -- usually implemented through DNS servers -- help maximize its capabilities.
Name resolution relates easy-to-remember names with difficult-to-remember IP addresses in resource records. Many standard functions rely on this service, but modern DNS servers can do more than that. They relate services, email information and more. It's critical for network administrators to optimize the performance, security and functionality of DNS.
Network administrators should perform periodic reviews of their DNS service, but they should also perform additional audits after any significant network change. Network administrators will benefit from knowing when to conduct DNS audits and what to review.
When to audit DNS services
How frequently network administrators should audit their DNS settings depends on their organization's specific circumstances. As a general guideline, however, it's best practice to plan quarterly DNS audits. It's critical for network administrators to have a scheduled review time. DNS is an essential service in most network environments and requires regular attention.
Quarterly reviews are a good start, but various factors or events should facilitate more frequent name resolution audits. These considerations include the following:
- Major network changes. Network updates, like expansions and consolidations, cloud migrations or deployments of new services.
- Security incidents. Security incidents related to name resolution or other aspects of the network.
- Availability events. Issues such as WAN or LAN connectivity problems, server downtime or interoffice routing.
- Business structure changes. Organizational shifts, such as company renaming, rebranding or acquisitions.
Network administrators might want to consider implementing a DNS checklist after any of the above occurrences. Thorough documentation can help with the DNS auditing process. Confirm everything, from administrative access to network performance to logs and alerting. This ensures name resolution is available to client devices and network services.
Network administrators should also regularly check log files. DNS logging might also prompt further investigation into certain events or justify a complete DNS review. Automated monitoring and logging tools can provide alerts on incidents.
How to audit DNS services
Specific settings vary depending on whether the network hosts DNS on Windows, Linux or a mix of the two. Regardless, the main tools in use are administrative consoles, command-line commands and log file analysis utilities, such as Event Viewer and rsyslog.
As network administrators carefully review their DNS settings, they might want to divide the service into different aspects, such as administrative access, client settings and security.
1. Review the name resolution service software
The first step in a DNS audit is to review the name resolution service software. First, network administrators should confirm the service starts with the server and runs without issue. They should also check which version of the DNS service software their organization uses. Organizations should have minimum version standards.

Administrators should also review server-specific log files. They should carefully configure log services' monitoring and alerting features for accurate and up-to-date service status as part of this process.

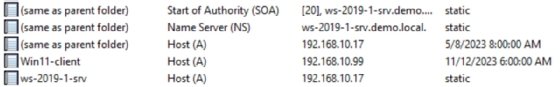
2. Examine maintenance resource records
As network administrators perform an audit, they should review several different maintenance records for accuracy. These include both client resource records -- especially any static records -- and DNS service records, such as start of authority and name server records. Look for and remove any artifacts, such as unneeded static records for devices no longer present on the network.
3. Confirm who has the appropriate administrative access
It's crucial to cybersecurity to know which users have administrative access to the network. Network administrators should review access controls for user accounts that can log on to the DNS servers. Only authorized administrators should have access to the DNS management console.
In addition to individual accounts, network administrators should also check group memberships for DNS privileges and consider limiting administrative group membership. For example, Windows systems give several administrative groups access to DNS, including the following:
- Local administrators.
- Domain administrators.
- Enterprise administrators.
- DNS administrators.
Network administrators might want to consider restricting access to necessary users only.

4. Check client settings and network performance
Dynamic Host Configuration Protocol (DHCP) leases and assigns IP addresses to client devices. Client devices should receive at least two DNS servers as part of the IP configuration. Network administrators should review DHCP settings to confirm this is true and ensure DHCP directs those client devices to nearby DNS servers to retain performance.
Administrators should also confirm firewall settings are appropriate for both client name resolution and interserver DNS zone transfers, including firewall ports 53/TCP and 53/UDP.

5. Review network functionality for DNS connectivity
DNS usually integrates into Active Directory in Microsoft-centric environments. This means the AD replication engine can replicate DNS information and store it on AD domain controllers. The two services are closely intertwined, so network administrations should check AD Event Viewer entries when they audit and troubleshoot DNS in these environments.
Network administrators should also check log files and administrative consoles to ensure DNS zone transfers and AD replication work correctly. In addition, they should review AD sites to ensure client devices find the nearest domain controller or DNS server.
Finally, administrators must examine network performance to ensure DNS performs well. Network teams should check traffic, firewall filtering and routing information. DNS is a heavily used service, so best practices are essential to optimize network traffic.

6. Confirm advanced settings are correct
Finally, network administrators should confirm their advanced settings are correct and optimized for DNS. It's important to review certificates and certificate authorities associated with DNS security configurations. Expired, expiring or misconfigured certificates can bring name resolution to a halt. Administrators should update these as needed to prevent issues.
In addition, network administrators should check the configurations for DNS over HTTPS or DNS over Transport Layer Security if they're in use on the network. Both services protect name resolution privacy and manipulation. Misconfigurations could prevent services from working as expected, so it's important to confirm they're configured properly.
Using network tools for audits
Network administrators might want to consider using various tools to examine DNS settings. Applications such as Nmap can expose service misconfigurations, firewall port settings and rogue devices on the network. Tools like Wireshark capture network traffic, which makes it useful for viewing DNS replication information or client-server DNS communications. Other network performance tools, such as Linux's iPerf3, are also helpful.
Benefits of DNS audits
Audits are time-consuming, but they can also be overwhelmingly beneficial to organizations. DNS audits help maintain a reliable and performant service layer that enables client systems to quickly find resources. Benefits of DNS audits include the following:
- Misconfiguration identification.
- Vulnerability identification.
- Version control assurance.
- Compliance reviews.
- Guaranteed service performance.
- Administrative access control.
DNS audits are also a good time to check for new service features that an organization hasn't implemented yet. Network administrators can use the audit process to begin planning how to update DNS' functionality.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to TechTarget Editorial, The New Stack and CompTIA Blogs.






