
Getty Images
The pros and cons of VPNs for enterprises
VPNs use different protocols and encryption to protect data and prevent unauthorized users from accessing company resources. But those protocols come with their own benefits and challenges.
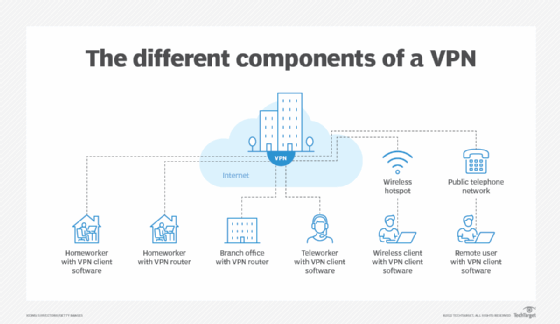
Enterprise network designs often include virtual private networks, due to their ability to connect users and networks to each other securely. While newer technologies offer network teams alternatives for network security, the advantages of VPNs continue to make them an integral part of enterprise networking.
Benefits of VPNs
Network teams can choose from a range of technologies to provide secure access and encrypt data. But the ease and uniqueness of VPNs make them a staple for secure remote access strategies. Below are some common advantages of VPN technology.
Prevent unauthorized users and enable secure access
The primary benefit of installing a VPN -- an encrypted online connection -- is to prevent outsiders from gaining access to data transmitted across the internet. In the past, enterprises needed to lease private communication lines to exchange data with geographically distributed offices. Internet use has proven to be much less expensive, but it isn't secure because outsiders can gain access to data.
As a result, many enterprise network teams use VPNs to provide secure access across the internet. VPNs can connect one network to another, such as a branch office network to a central office network. A VPN can also connect someone working from home or a mobile location to the central office network.
Encrypt data and anonymize IP addresses
Connecting from a public hotspot exposes a user's data. Using VPN software installed on a laptop, phone or tablet means data is encrypted from the device to the destination site.
Another benefit of a VPN is it can anonymize the connecting internet address to the accessed website, so the connection appears to come from a different IP address for each connection. Changing an address makes it more difficult to track the use of a site.
Availability
Network teams can install VPN software on nearly any type of device, such as physical or virtual servers that run Windows, Linux, Android and iOS for desktops, laptops, phones and tablets. A variety of vendor packages are available for each type of device and OS.
Commercial VPN packages are also available, which can connect to endpoints in other countries. By connecting to an overseas server, users can then connect to content available only in that country.
Ability to offload VPN maintenance
Many enterprises buy and install VPNs on purchased and owned equipment. But, as an alternative, enterprises can contract for VPN services as part of the internet access services a network service provider offers.
The advantage of renting a VPN service is it offloads maintenance of the VPN from the enterprise network staff. Alternatively, the benefit of implementing in-house VPNs is the ability to configure the service specifically to meet enterprise requirements.
Pros and cons of VPN encryption technologies
A VPN can use several different encryption technologies, each with its advantages and disadvantages.
L2TP/IPsec
Layer 2 Tunneling Protocol/IPsec (L2TP/IPsec) uses a Layer 2 tunneling protocol plus IPsec to provide encryption. It is available on nearly every type of OS and device.
Advantages of L2TP/IPsec include the following:
- Extremely secure and stable with easy setup.
- Higher efficiency than OpenVPN.
Disadvantages include the following:
- Slowed down due to the need to encapsulate data in a Layer 2 tunnel and encrypt data using IPsec.
- Firewalls can block L2TP/IPsec.
OpenVPN
OpenVPN is widely used and available in a free, open source version. It is also available in commercial versions for Windows, Linux, desktops, laptops, phones and tablets. It uses Secure Sockets Layer/Transport Security Layer, Blowfish or Advanced Encryption Standard (AES) to encrypt data.
Advantages of OpenVPN include the following:
- Strong security and excellent support.
- Ability to pass through firewalls.
- Support for both Layer 2 and Layer 3 connections.
Disadvantages include the following:
- High overhead due to protocol complexity.
- Its complexity makes it more difficult to install and configure than other VPN technologies, requiring third-party software L2TP/IPsec to set up.
PPTP
The Point-to-Point Tunneling Protocol (PPTP) specification was first issued in 1999 when attackers didn't have processors as powerful as those currently in use. PPTP is now considered obsolete. As such, it should be used only for data that has low security requirements but benefits from PPTP's speed, such as video.
The advantages of PPTP include the following:
- Easy to install and fast.
- Supported in current Windows versions.
Disadvantages include the following:
- Considered obsolete.
- Security vulnerabilities.
SoftEther
A Japanese university developed SoftEther as an open source academic project in 2014. SoftEther uses AES-256 to provide high security and penetrate firewalls. It is supported on Windows, Android, iOS, macOS, Linux and Unix versions.
Advantages of SoftEther include the following:
- Designed to offer high data rates and quick connections.
- Penetrates firewalls.
Disadvantages include the following:
- Network pros might hesitate to manage an open source project, preferring commercial products with VPN protocols that are easier to install and maintain.
WireGuard
WireGuard is designed for Windows, Android, iOS, Linux and various Unix versions. The protocol was initially released in 2015 and is still in development. WireGuard aims to provide a secure protocol that is faster than OpenVPN and easier to install.
Advantages of WireGuard include the following:
- Uses public key encryption.
- Offers faster connection setup than other protocols.
- Downloads faster because it uses less code than OpenVPN.
Disadvantages include the following:
- It stores IP addresses statically, which means the same address is used for each connection, making tracking possible.
Maintain VPNs carefully
VPNs based on a strong encryption standard are difficult to attack. But network teams should exercise caution because networks can still be breached, such as when an employee clicks on the wrong website or opens the wrong email.
In any case, it's important for teams to install and maintain VPNs carefully wherever enterprise data flows between internal networks and remote authorized users. Bad actors are frequently creating new attack types, and processor power increases constantly. Monitor these developments, and upgrade VPNs when necessary to continue to maintain tight security.







