The future of VPNs in the enterprise
VPNs have been the workhorse of online connectivity. Enhancements to software and processing power in end devices will transform how companies use the technology going forward.
Many forecasted the VPN's demise for years before the COVID-19 pandemic. Then, during the early month of the pandemic, the value of VPNs surged. VPN strategies that were just beginning to percolate gushed out within weeks as companies raced to find new ways to connect their remote workforces.
But it's time to ask: What does the future of VPN technology look like now?
The future of VPN connectivity
The migration of office workers to a work-from-home environment created a new dilemma: How should organizations support workers who might use computers and mobile devices from home to access corporate resources?
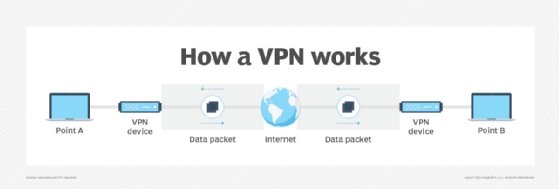
The traditional VPN uses a thick client model to build a secure tunnel from the client device to the corporate network. All network communications use this tunnel. This model comes at a cost, however. Access to public cloud resources must transit the VPN tunnel to the corporate site, which then forwards access back out to the internet-based cloud provider. This is known as hairpinning, and it increases the path packets must take and ushers in a corresponding increase in latency.
Internet-based VPNs don't support quality of service so they can't handle time-sensitive network traffic, such as real-time voice and video. The combination of uncontrolled latency, jitter (changes in latency) and packet loss can make real-time collaboration technologies unusable. So-called private or personal VPNs, while useful for those users who need to hide their actual IP addresses, are also not suitable for corporate access. These services provide a VPN connection from a device to the VPN provider's network, which is beneficial for international travelers but offers no built-in security.
It's clear that VPNs have to evolve to serve users' demands. Future VPN designs will rely much more heavily on the increased processing capabilities now being built into end systems. This opens the door to placing more software-based VPN technology into endpoints. VPNs will take advantage of these local processing capabilities, which will make the technology easier for users and administrator alike. Network admins, for example, will oversee VPNs through central systems.
What about hardware? Some predictions suggest hardware isn't necessary in a software world. Yet, as something must make the physical connections, hardware will still be necessary in the VPN of the future. More likely, x86 compute systems that perform functions previously completed in dedicated hardware will replace some devices -- particularly at the network edge, where distributed computational resources are readily available. The network core will continue to require hardware specifically designed to support the speeds necessary for VPN connectivity for the foreseeable future.
VPNs may also begin to function like software-defined WAN products, where connectivity is independent of the underlying physical network -- wired, wireless or cellular -- and its addressing. These VPN systems should use multiple paths and transparently switch between them.
AI, machine learning and automation will also change how we use and deploy VPNs.
The future of VPN security
Corporate VPNs provide two major functions:
- encrypting data streams and secure communications; and
- protecting the endpoint from unauthorized access as if it were within the corporate boundary.
The straightforward use of encryption technology is to secure communications. Encryption technology is relatively old and is built into modern browsers, which makes the browsers easy to use. Secure Sockets Layer/Transport Layer Security VPNs provide this functionality.
Modern VPN systems protect endpoints from unauthorized access, as these systems require all network communications to flow over a VPN between endpoints and a corporate VPN concentrator. Other corporate resources -- among them firewalls, intrusion detection systems and intrusion prevention systems -- protect endpoints with content filtering, malware detection and safeguards from known bad actors.
AI and machine learning will beef up these protections even further -- and without requiring an increase in network or security administrator support.
VPN paths become less efficient when an endpoint communicates with internet-based resources, such as SaaS systems. The endpoint must first send data to the VPN concentrator, which then forwards the data to the SaaS application and, therefore, adds latency. In addition, because the SaaS app employs its own encryption, network overhead increases within the VPN.
Split tunneling is a potential solution to this inefficiency, but IT teams must select VPN termination points carefully to avoid a security hole. Integration with smart DNS servers, such as Cisco Umbrella, enables split tunneling to specific sites under the control of network or security administrators.
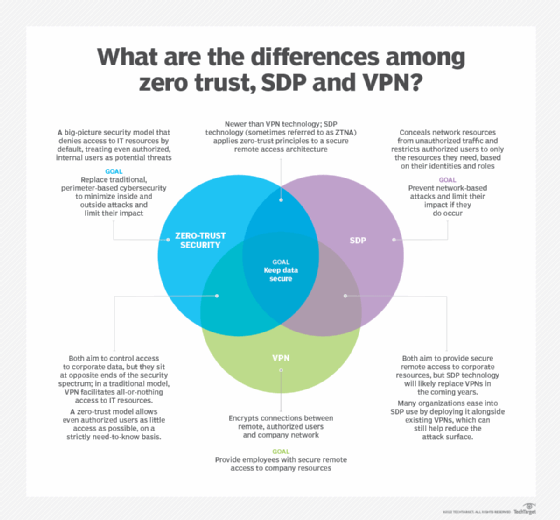
Is zero trust the future of VPN?
An even better security stance relies on the zero-trust model, which assumes endpoints are compromised, regardless of their location. The concept, introduced in 2010 by Forrester Research, has become the new standard to which networks should conform. Zero-trust security components include allowlisting and microsegmentation. The future of VPNs will encompass automated methods used to create and maintain these security functions.
Another recent addition to VPN security is Secure Access Service Edge (SASE). It bundles multiple technologies -- among them secure web gateway, firewall as a service, cloud access security broker, zero-trust network access and DNS reputational security -- to fortify the security of a corporate VPN. With this design, devices make a secure VPN connection to a cloud-based SASE system, which prevents unauthorized access by attackers, bars known malicious websites and locks down web, cloud and corporate access.
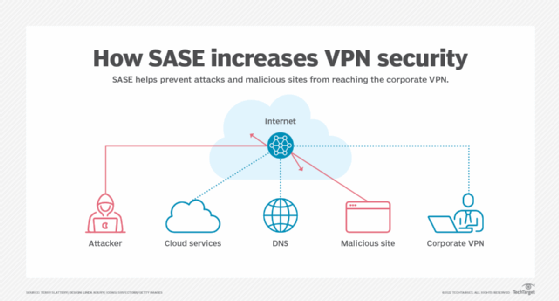
IT professionals can expect the future of VPN technology to provide an increase in security while reducing the effort needed to implement and maintain that protection. Case in point: VPNs will pair with zero-trust frameworks, where VPNs can then be paired with software-defined perimeters to add another level of security.








