
James Thew - Fotolia
Tips to provide network support for remote workers
Enterprises must modernize their networks to support remote work, while IT teams ensure networks have proper bandwidth and security, as well as dedicated help for remote workers.
Remote workers need reliable network support from their organization's management teams.
Remote work, also called telecommuting, rose in popularity with the onset of the COVID-19 pandemic. Enterprises suddenly had to support hundreds or thousands of remote workers, and network management teams needed to adapt. Remote work continues to be a popular option among employees, so it's important for companies to recognize that remote workers require different support compared with in-office employees.
A continuing goal for network teams is ensuring optimal support, security, reliability and performance for both in-person and remote employees. As part of those efforts, management teams have enacted modernization strategies and improved network configurations and security management.
IT administrators are responsible for facilitating and managing remote work. To provide the best possible outcomes for remote workers, it's essential for organizations to have a dedicated and proactive approach to remote work. This article provides guidance on how to monitor and manage network performance and security for remote workers. Also provided is a checklist of activities network teams can follow to provide network support for those employees.
Remote work policies and procedures
A formal policy for remote work technology is an essential program component. This policy differs from an overall corporate remote work policy. It focuses primarily on the technologies remote workers need to perform their duties in a secure environment. IT teams should document, regularly update and circulate remote work procedures. This way, remote workers can securely connect with necessary resources.
End-user devices
In the early days of remote working, employees typically used their personal laptops or computers. Ideally, however, organizations issue remote workers company-owned and configured laptops. In this arrangement, employees might still use personal devices, such as smartphones, tablets and other similar devices.
Enterprises must configure each device with the correct software for secure access to a company VPN or other corporate network. In lieu of such arrangements, IT departments must ensure remote workers' personal devices are configured for access to company resources. It might be necessary for remote users to have a company account on their devices in addition to a personal one.
Network resources for remote working
While VPNs are a secure method for remote connection to corporate resources, it can be challenging for organizations to obtain sufficient VPN licenses to support each employee. Add to that the cost for access arrangements, such as two-factor (2FA), multifactor authentication (MFA) or password management, to ensure secure login to company resources. In this case, the company's corporate network infrastructure might be the better vehicle for remote workers.
Managing bandwidth to accommodate remote workers continues to be an important activity. Remote users might connect to their company VPN via the internet, so the necessary bandwidth at the company's data center might need a substantial increase to handle the demand. This might mean negotiating with LAN and WAN carriers for additional bandwidth. Software-defined WANs can also optimize bandwidth.
Security for remote working
Remote work always increases security concerns. While VPNs have native security attributes, it's important to extend security in additional directions. For example, 2FA and MFA are key access methods. Data encryption -- at rest and in motion -- is another important activity. Some technologies add security to almost any data transaction. Zero-trust security models further increase security attributes.
Beyond the front-line activities, regularly examine security risks, threats and vulnerabilities. Doing so can help identify potential threat actors that could disrupt remote networks with the following:
- Damaging or stealing data during transit.
- Introducing phishing scams.
- DDoS attacks.
- Ransomware attacks.
Teams can help keep the network secure by deploying security systems that monitor remote connection health. These security systems can run penetration tests as well as breach and attack simulations to ensure stable and healthy remote connections.
Remote workers should have antivirus, ransomware, access control and encryption tools in their systems to ensure security at the network edge. Company-prepared laptops and other workstations can help achieve this.
Remote work administration
Companies with remote worker populations should have IT networking and security teams dedicated to their operation. Optimize internal help desk departments to support remote workers. This could mean making remote help a separate unit from in-house support activities. If this isn't possible, ensure support teams have the necessary tools to diagnose problems remotely and provide solutions.
On-site equipment replacement is not possible with remote workers. As such, workers might need to obtain replacement items on their own or wait on shipping.
Continuous monitoring of all remote workers and their network connections is essential to quickly identify potential problems. Numerous network diagnostic tools are available. The key is to select tools that provide both remote monitoring and diagnostics. The table below provides a short list of such programs.
The following remote monitoring and management (RMM) tools are listed in alphabetical order.
| RMM tool | Characteristics |
| Atera | Automated network monitoring, patch management, remote access and diagnostics using a ticketing system |
| Barracuda RMM | An on-premises or cloud platform that addresses security management, network monitoring and provides Help Desk features |
| Dameware Remote Everywhere by SolarWinds | A cloud-based support platform that examines unattended or in-use computers and mobile devices |
| GoTo Resolve | Remote administration, patching and automated monitoring |
| ManageEngine Endpoint Central | Designed for endpoint management and includes remote monitoring functions |
| ManageEngine RMM Central | Tool optimized for Windows Server or cloud (AWS, Azure) platforms |
| N-able N-sight RMM | Platform with broad range of network monitoring, analysis and management resources |
| NinjaOne | SaaS tool that examines and analyzes Windows, macOS, Linux, Hyper-V and VMware virtualized environments |
| Paessler PRTG | Server-based on-site monitoring tools, available as SaaS or for Windows Server |
| Site24x7 MSP Edition | Designed for managed service providers to monitor cloud-based IT networks, servers and applications |
| SuperOps | Integrated professional services automation (PSA)/RMM platform that provides intelligent endpoint management |
| Syncro | Cloud platform that combines PSA and RMM tools for MSPs |
| TeamViewer Remote Management | Cloud-based option with a broad selection of RMM tools |
Additional administrative activities include the following:
- Patch devices when needed.
- Review and update firewall and intrusion detection system/intrusion prevention system rules.
- Evaluate VPN usage and trends.
- Manage network segmentation if used.
- Monitor and respond to WAN traffic changes.
- Test remote access connections.
- Analyze risks, threats and vulnerabilities.
- Monitor use of cloud-based technologies that support remote work.
- Review and update disaster recovery plans associated with remote working.
- Establish backup arrangements in case of network disruption.
- Provide tips and guidance to remote workers, including best practices training and awareness for remote work.
- Ensure collaboration resources like Microsoft Teams and Zoom are available and operational.
Remote versus in-office workers
In-office employees have access to all relevant networking and security resources. In-office employees can handle arising issues quickly and involve IT technicians if necessary.
By contrast, remote workers have greater risks to their ability to perform their duties. They rely on remote networks, such as Wi-Fi and local carrier internet access, which might not be 100% dependable. Remote employees need security and networking arrangements such as 2FA/MFA and VPNs.
Remote problem diagnostics and troubleshooting might be more challenging. Desktop tools must be able to synchronize with data center systems. Collaboration tools are necessary for meetings and for keeping people in touch. Emergency procedures must be in place to address unplanned disruptions.
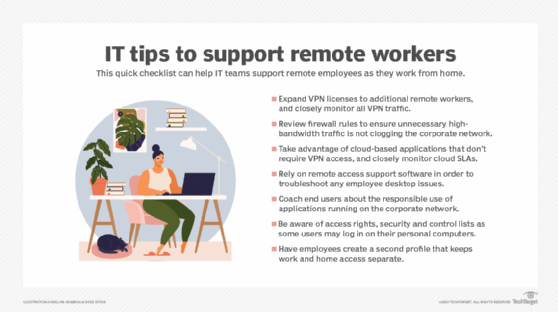
Network support for remote workers checklist
Included here is a checklist of the activities discussed in this article. This approach reduces the likelihood of security breaches disrupting remote worker productivity.
Paul Kirvan is an independent consultant, IT auditor, technical writer, editor and educator. He has more than 25 years of experience in business continuity, disaster recovery, security, enterprise risk management, telecom and IT auditing.







