macrovector - Fotolia
Setting up and using a home VLAN to segment network traffic
Virtual LANs can help homeowners segment their network traffic for enhanced control and security. Network analyst John Fruehe takes you inside his home VLANs.
Enterprises use virtual LANs, or VLANs, to segment traffic, enforce security, improve performance and generally streamline operations. VLANs are virtual overlays enabled by tagging traffic with a VLAN ID. Once tagged, network traffic is then virtually segmented across devices.
Like many other enterprise capabilities, VLAN technology rarely finds its way into home networks due to complexity and lack of necessity. Promoting VLANs can increase support costs for home network equipment providers as they add complexity to most simpler home environments. So, while a home VLAN can be supported, they are rarely encouraged.
But, with that said, VLANs can find a place in some home networks.
Home VLAN switch and router
To start, setting up a home VLAN requires VLAN support in the router. If the router does not provide support, there is no way to add it. My home network is a business-class network that supports VLANs, but most of my earlier consumer-focused routers also supported this capability.
Additionally, all switches on the network must be managed switches because unmanaged switches will not support VLANs.
How VLANs work
The 802.1Q standard defines the traffic tagging, enabling VLANs to operate. Every network has a "default VLAN" which typically carries a VLAN tag of "1." Any traffic that is untagged on the network, meaning there is no associated VLAN tag, will be assigned to the default VLAN. Any traffic that carries an explicit VLAN tag will only be transmitted to ports, devices or clients that are part of that virtual network.
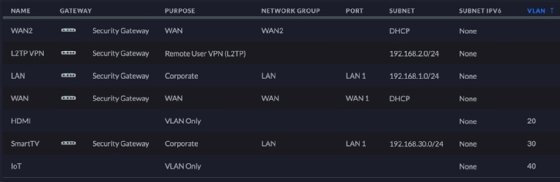
Here is a view of my network showing the VLANs that I have created:
Home VLAN use cases
In several instances and use cases, VLANs make sense in a home environment.
- Segmenting for traffic. Multicast devices, for instance, flood the network with simultaneous communication to multiple clients. If the traffic only needs to be shared with a few clients, putting them on a separate VLAN eliminates the flood of traffic to the other devices that don't need to see that traffic. I use HDMI repeaters to send TV signals across my network, so I use a VLAN (#20 above) to limit that traffic to only the HDMI devices.
- Segmenting for convenience. I have a smart TV connected on my network. Normally, changing the input is trivial because there are only a handful of ports. But because the TV is connected, every single broadcast device on the network -- like Sonos speakers or my network-attached storage -- all show up as input connections, meaning I have more than 15 input choices to scroll through. Putting the smart TV on its own VLAN (#30 above) limits the TV, blocking those devices from appearing as inputs.
- Segmenting for security. I have plenty of IoT devices on my network from smart light switches, thermostats, a sprinkler and even door locks. Because these devices are cloud-based, I don't have great control or visibility over exactly what they send. Putting the IoT devices on their own VLAN (VLAN #40 above) enables me to better control data movement and limit devices from having access and information about other things on the network.
There are other more esoteric reasons to deploy VLANs, including guest network connections, but most of these are automated by the router using firewall rules so a VLAN is not required. This makes sense because the firewall rules will work with unmanaged switches.
Overall, VLANs can help bring more control over how your network operates. So, if your equipment supports VLANs, it's worth looking into whether VLAN capability makes sense for you.







