
Nmedia - Fotolia
How to use traceroute to troubleshoot network problems
Traceroute is a tool that can provide more insight than you might think. Learn how to use traceroute to troubleshoot network issues.
While most every network professional has learned how to use traceroute, many may not understand its true power as one of the most vital network troubleshooting tools. Traceroute is a packet-tracking tool that is available for most operating systems. It's more powerful than many might assume. It can be used by network administrators to detect bogus routes or potential redirects of traffic. Attackers can use traceroute to enumerate a path and for firewall discovery.
Understanding how to use traceroute can help you identify the number of networks, hops, devices and locations between the source and the destination device. Traceroute works by using the time-to-live (TTL) field in the IP header. Each router that handles an IP packet will decrease the TTL value by one. If the TTL reaches a value of zero, the packet is discarded and a "time exceeded" Type 11 Internet Control Message Protocol (ICMP) message is created to inform the source of the failure. Linux traceroute makes use of the User Datagram Protocol. Windows uses ICMP, and the traceroute command is tracert.
How traceroute works
As an example, let's say there are normally seven hops from your office in Houston to the New York office; however, one day, users start complaining of extremely slow traffic. So, when you perform a traceroute, you determine the hop count is now 14 and your packets are going to New York via China, which may indicate some type of issue. Your packets are taking a different route than usual; this may be a legitimate problem, or an attacker may have manipulated the Border Gateway Protocol routing standard and is potentially redirecting your traffic. Let's look at an example of how to use traceroute to resolve this issue. Let's try a simple Windows command prompt traceroute, starting with the third hop that is targeting www.example.com.
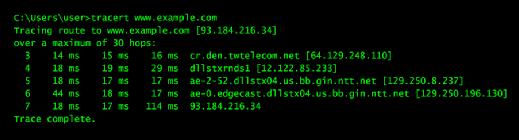
Before we analyze the results, there are a few things to note about how to use traceroute: Each numbered line in the preceding traceroute example represents one hop. By default, traceroute goes up to 30 hops; however, that can be adjusted with the -h option. Traceroute uses a default destination port that starts at 33434. Windows tracert sends a series of three probes per hop.
Upon reaching the first router -- my firewall -- the packet TTL value is decremented to 0, which elicits a time-exceeded Type 11 error message. This message is returned to the sender to indicate that the packet did not reach the remote host. Next, Windows increases the TTL to a value of 2. This process continues until we reach the destination shown in line 7. Because this is the final hop, the destination issue is either a normal ICMP ping response, if Windows is used, or an ICMP Type 3 destination unreachable message, if Linux is used, for traceroute.
How to read a traceroute to determine the physical location of routers
We can also learn the physical location of the routers the packets are passing through from understanding how to use traceroute as a network troubleshooting tool. The two most widely used location identifiers are International Air Transport Association (IATA) codes and Common Language Location Identifier (CLLI) codes, a standardized method that pinpoints the physical locations of significant hardware at telco and carrier switching facilities. You will easily recognize IATA codes if you've ever flown. Line 3 of our example displays DEN, which is the IATA code for Denver. An example of a CLLI code appears in line 4 of the traceroute. It indicates a location of Dallas.
identify
4 18 ms 19 ms 29 ms dllstxrnds1 [12.122.85.233]
This particular hop indicates the following: dlls is Dallas, tx is Texas, rn is an office in Richardson and ds1 is the second digital telephone switch at the Richardson location.
One final piece of information about how to use traceroute effectively: You may be able to determine from a traceroute the type of device and port your connection is passing through. For example, line 5 of the traceroute provides the following information:
ae-2-52.dllstx04.us.bb.gin.ntt.net
The naming format ae-#-# is most likely a Juniper device, Ethernet bundle in slot 2, port 52.
Hopefully, these examples demonstrate some of the useful information that can be gleaned from a simple traceroute. Not everyone follows an exact naming convention, but with a little work, you can start to pick out many pieces of useful information once you know how to use traceroute. But be careful: Such information can be useful to a network defender, as well as attackers attempting to enumerate your infrastructure.







