
Getty Images
How to set up a VLAN for enterprise networks
Network administrators configure VLANs to enhance network security and performance. Learn how to set up a VLAN, from configuration steps and best practices to troubleshooting tips.
A virtual LAN is a logical division of a network that enables devices to communicate as if they are connected to a single switch. These divisions are critical to network security, performance and organization.
This article explains the problems VLANs address and outlines VLAN configuration steps.
Why use VLANs?
Most administrators divide the network into smaller, more manageable pieces early in the network configuration process. Network administrators partition networks for a variety of performance and design reasons, such as the following:
- Security. Traffic isolated to a particular network segment can mitigate eavesdropping attacks.
- Performance. Traffic isolated to a particular network segment can alleviate network congestion concerns.
- Manageability. A more manageable network provides a more flexible physical network infrastructure, easier delegation of administrative authority on a per-segment basis and easier integration of remote physical locations, such as branch offices.
Traditional network segmentation uses routers to isolate subnets, with each segment having its own address, such as 192.168.2.0/24. Clients within the same subnet communicate through switches, while intersubnet communication requires a router or Layer 3 switch.
This segmentation creates logical separation between subnets. But, depending on how the network is segmented -- based on physical cabling, floor level or department -- segmentation can cause a problem with physical connectivity. Consider, for example, if a company vice president of sales wants to move to a corner office while the rest of the team works in the basement. In network terms, the subnet design operates at OSI Layer 3, where IP addressing and routing occur.
So, how do VLANs help fix these issues, and what do their configuration steps look like? Unlike typical subnetting, VLANs operate at OSI Layer 2. VLANs work with data based on physical MAC addresses assigned to network interface cards (NICs) instead of identifying traffic by logical IP addresses.
In simple terms, VLANs group systems by MAC address instead of IP address.
How VLANs work
Network administrators must understand the general use and structure of an environment using VLANs before they can configure switches to support them.
Network packets leave a computer containing four addresses:
- Source MAC address. The NIC's MAC address.
- Source IP address. The NIC's IP address.
- Destination MAC address. The MAC address of the next device to handle the packet, usually a switch or router.
- Destination IP address. The destination system's IP address.
Typically, only one device connects to each physical switch port.
Network administrators must define two or more VLANs on the switches, assign each VLAN a network ID and join the appropriate physical ports to one of the VLANs.
For example, an administrator might decide to create VLANs for the departments in a business network:
- Developer team. Network administrators typically isolate this department for security reasons.
- VLAN 10: Network ID 192.168.10.0/24, name dev-vlan.
- Finance department. Network administrators typically isolate this department for security reasons.
- VLAN 20: Network ID 192.168.20.0/24, name fin-vlan.
- Marketing team. Network administrators typically isolate this department for capacity planning because it often generates large multimedia files that degrade network performance.
- VLAN 30: Network ID 192.168.30.0/24, name mar-vlan.
- All remaining staff computers. Network administrators isolate the remaining computers into a general group.
- VLAN 40: Network ID 192.168.40.0/24, name prod-vlan.
Next, network administrators decide which computers connect to which physical ports on each switch. If computer Dev1 connects to port 9 on SwitchA, join that port to VLAN 10. If computer Fin3 connects to port 8 on SwitchA, join that port to VLAN 20. If computer Mar7 connects to port 10 on SwitchA, add it to VLAN 30.
Network administrators must do this for each switch. They also configure truck connections between switches, which enables cross-switch communications within a VLAN.
One of the benefits of using a VLAN is the level of devices within the VLAN can only communicate with other devices in the same segment. For example, clients connected to switch ports assigned to VLAN 10 only communicate with other devices on VLAN 10, regardless of which switch the host uses. Network administrators can also connect a router configured for all subnets to enable and control traffic between them, if necessary.
Get started with VLANs
The initial VLAN configuration steps help network administrators plan and diagram the network configuration. These steps are critical to VLAN configuration success.
1. Plan the VLAN configuration
Begin by understanding the network segmentation goals. Why does the organization want to isolate the developer team? Why should the organization restrict network transfers from the marketing department to certain machines?
The answers probably relate to network security and performance, but administrators must understand their goals before they begin the segmentation process. Consider the environment's unique network traffic control needs.
2. Map the network and fix any misconfigurations or unexpected devices
An accurate network map is critical to network administration. Network maps are useful for planning, security incident response and troubleshooting. Use tools like Nmap to gain a complete picture of the network.
From there, network administrators should create a network diagram that shows every router, switch and IP subnet. They must include relevant network services, such as DNS name resolution and Dynamic Host Configuration Protocol IP address allocation.

How to set up a VLAN
Connect to switches using Secure Shell (SSH) or HTTPS. Network administrators can use a web-based GUI or commands at the command prompt, depending on the switch interface.
Authenticate each switch, and create the VLANs according to the network map. The commands resemble the following steps.
To create a new VLAN and select its configuration interface, type the following.
switch(config)# vlan 10
switch(config-vlan)# name dev-vlan
To confirm the VLAN settings, type the following.
switch# show vlan
Repeat these steps for each switch.
Create VLAN connections between switches by designating trunks. Enter the interface's configuration mode and designate it as a trunk.
switch(config)# interface gigabitethernet 1/0/1
switch(config-if)# switchport mode trunk
To specify which VLANs can use the trunk, type the following.
switch(config-if)# switchport trunk allowed vlan 10,20,30,40
This example enables all VLANs.
Confirm the trunk configuration.
switch# show interfaces trunk
Next, use the GUI or CLI to join each physical switch port to a VLAN. The commands vary by switch OS, but it should resemble the following example. To enable the access mode and add interface GigabitEthernet 0/1 to VLAN 10, type the following.
switch(config)# interface gigabitethernet 0/1
switch(config-if)# switchport mode access
switch(config-if)# switchport access vlan 10
Save the changes with the appropriate command for the switch. For example, type the following.
switch# copy running-config startup-config
Don't forget to test the configuration with tools such as Wireshark and tcpdump to intercept traffic and ensure addressing and VLAN tagging work as expected.
Web-based administration
Most switches permit web-based administration for tasks like creating VLANs. These interfaces are typically easier to use.

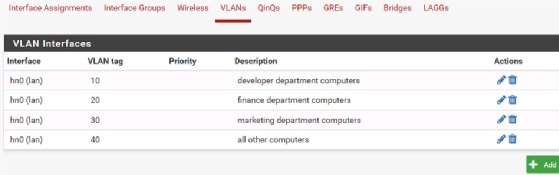
Network administrators should remember to manage their switches using an HTTPS connection for security rather than a plain HTTP session. The interfaces vary for VLAN configuration, but the general steps remain the same.
VLAN monitoring
Network administrators should establish a routine for VLAN configuration monitoring to ensure switch port assignments remain accurate and trunking works properly. They must also add new switches, subnets or hosts to the overall VLAN structure as part of the change management processes. Failure to do so could risk isolated hosts or subnets, which might invoke a help desk ticket and troubleshooting incident.
VLAN and switch security options
Many security options exist to help manage VLANs and switches. VLAN security options to research and consider include the following:
- Implement port security. Assign MAC addresses to specific switch ports to avoid unknown and unauthorized devices.
- Secure administrative connections. Control admin connections and privileges to the VLAN infrastructure.
- Use SSH and HTTPS for administrative connections. Don't use unencrypted admin connections to switches, and change the default account name and password.
- Manage VLAN trunk assignments. Assign VLANs only to the specific trunks they need to avoid passing traffic unnecessarily across every interface.
- Configure an admin VLAN. Isolate administrative and configuration traffic from production traffic.
- Configure a guest VLAN. Manage and isolate guest devices on the network.
- Disable unused ports. Disable unused ports to avoid unexpected and unauthorized devices on empty ports. Most switches enable this feature.
VLAN troubleshooting
Most VLAN troubleshooting involves confirming the configuration. Begin at the host level, and work toward the overall VLAN architecture. Network administrators can follow these general steps:
- Confirm the client's NIC is functioning correctly and has a stable connection to the switch.
- Check that ports are assigned to the correct VLAN. This is especially important after certain troubleshooting situations. For example, suppose a network administrator moved a client's network connection from one switch port to another -- they might have inadvertently moved it to another VLAN.
- Confirm VLAN trunking settings to ensure the switches can communicate effectively.
- Verify accurate VLAN names on all switches.
- Check for routing issues, especially accurate packet filters and routing tables.
Network administrators should be particularly careful if they use MAC address filters to assign specific NICs to particular switch ports. If a desktop support technician swaps out a NIC for troubleshooting, the network team could run into VLAN port assignment issues.
Wrap-up
VLANs are an essential part of today's network infrastructure. They greatly enhance a network administrator's ability to manage traffic, improve security and optimize performance. Most switches provide a relatively easy interface to help create VLANs, assign ports to VLANs and establish VLAN trunks between switches, enabling a flexible configuration.
Network administrators must examine their networks to see how VLANs can improve their current configuration. If an organization already uses VLANs to manage network traffic, network teams should audit the configuration to ensure it operates at peak performance.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to Informa TechTarget Editorial, The New Stack and CompTIA Blogs.







