
sdecoret - stock.adobe.com
How SD-WAN changes the network security perimeter
The advent of SD-WAN has changed the network security model by pushing more security and control to the edge -- and businesses need to adjust to this new reality.
Networking and security have always been closely linked, and software-defined WAN furthers that reality, while also changing the network security perimeter.
Typically, branch office connectivity is handled through private leased lines. This setup worked well for years as MPLS, which was generally more segmented from the wild west of the internet, was the primary transport. In addition, a VPN created further connections.
But traditional WANs also limit access to cloud applications. Businesses would route branch office traffic through the headquarters before accessing the internet, using a firewall to protect data and systems.
While this arrangement creates a data bottleneck, it was a manageable and preferred system for years because of security control.
Pushing security to the edge
Software-defined WAN (SD-WAN) changes the security paradigm. As businesses start to look at SD-WAN and transition some or all of their branch office traffic to broadband internet offerings, security is becoming a more challenging prospect.
This change is happening because many SD-WAN offerings use broadband connections and send their data and control over the public internet instead of private leased lines, pushing the network security perimeter to the edge and putting security in a different light.
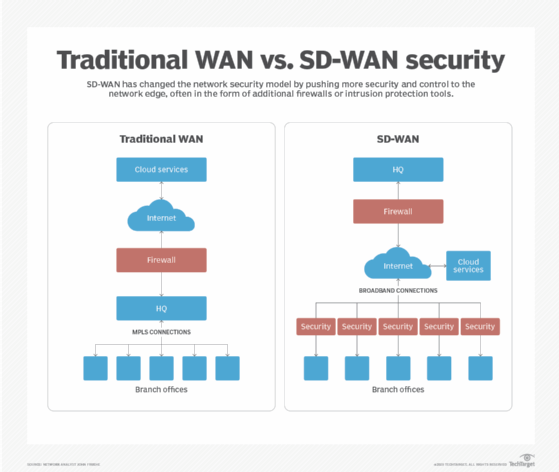
A single strong firewall is no longer the primary protection with an SD-WAN, and businesses now need to think about security at the edge. With more businesses relying on cloud services, any applications running in the cloud are easier to access from a branch location directly through the internet via the SD-WAN connection rather than routing all cloud traffic back through the headquarters first.
By implementing security and control at the edge, where the branch offices connect to the internet via SD-WAN, a business can better manage the traffic. Also, organizations could potentially reduce the cost of data transport by removing much of the redundant traffic. However, to do this effectively, businesses should look to the SD-WAN provisioning process and integrate security directly into that provisioning.
The automation and orchestration of SD-WAN can make this possible because that provisioning process is more automated and controlled. In the past, with each branch needing to be provisioned independently, allowing individual security at the branch level was a daunting challenge.
Software-defined perimeter can also help
SD-WAN can help automate edge security, enable IT to push some validation to the branch office and support a more flexible security profile.
But another strategy -- software-defined perimeter (SDP) -- can also increase security for branch offices. SDP essentially creates a "black cloud" in which different endpoints are not visible to traditional scanning. The original efforts around SDP were done in part by the U.S. Department of Defense, leading to all communications relying on a need-to-know model.
With an SDP, all endpoints require authorization and authentication; all of this operates in a zero-trust environment where traditional static addresses and definitions are replaced by dynamic environments.
But, whether a business relies on VPN or SDP, the advent of SD-WAN has fundamentally changed the security model by pushing more of the security and control to the edge, and businesses need to adjust to that new reality.







