3 DDoS mitigation strategies for enterprise networks
Enterprises can choose from three major approaches to mitigate DDoS attacks on their networks: Buy from an ISP, do it themselves or use a CDN service.
Distributed denial-of-service, or DDoS, attacks are becoming more common in enterprise networks and are sometimes even combined with ransomware.
The main types of DDoS attacks are the following:
- Volumetric DDoS. This attack crushes devices or services by ramping up traffic beyond the ISP bandwidth subscribed to by the client. This can involve User Datagram Protocol or SYN flooding and DNS amplification.
- Application layer attack. This attack is designed to use automation to take down or flood specific applications.
- Advanced persistent DoS. This attack uses automation in combination with reconnaissance to sculpt persistent long-term attacks on a specific target, while hiding the intended victim in a larger group.
Enterprises can respond to attacks with the three following DDoS mitigation strategies and approaches:
- Buy a service from your ISP. Many ISPs offer DDoS mitigation services, but when an enterprise gets hit with an attack, it needs to report the incident to the ISP to begin mitigation. This strategy is called clean pipes and is popular with ISPs, which charge for the service. This strategy often results in a 30- to 60-minute delay before mitigation starts.
- Do it yourself. Enterprises can take a DIY approach with intrusion prevention systems (IPSes), firewall technology and even specialized hardware purpose-built to defend against DDoS. Unfortunately, the traffic is already on premises and is eating up valuable bandwidth. This approach is best suited for enterprises that place their equipment at a colocation facility where the ISP is reached through a cross-connect and downstream bandwidth to the rest of the company can be protected.
- Use a CDN. This approach minimizes exposure of corporate infrastructure by putting it behind a content delivery network (CDN). These networks are large and diverse, and if the client subscribes to DNS and DDoS mitigation, they can protect e-commerce sites, as well as the company itself.
As always, the best DDoS mitigation approach depends on a number of factors, including what enterprises are trying to protect and what their perimeter looks like. In large corporations, the demilitarized zone (DMZ) is a complex set of modules that each has separate needs.
Below is a breakdown of the different DMZ modules to consider:
- e-commerce -- clients that connect to your servers;
- B2B -- business partners that connect to your servers;
- internet -- your employees and contractors that connect to the internet; and
- VPN -- employees working remotely that connect to your enterprise.
It's important to note that DDoS can hit all of these, and no one DDoS mitigation strategy is perfect. So, let's work our way through these strategies. We'll also explore how each approach fares in the DMZ use cases above, considering the strategy's effectiveness, attack transparency and whether an outage is likely.
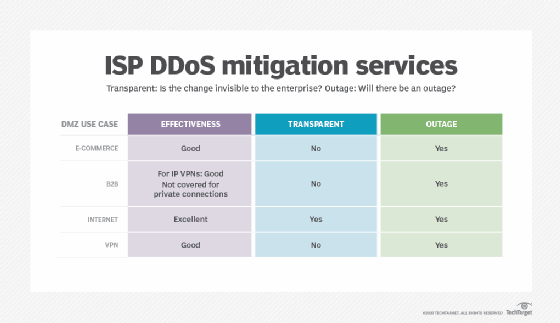
Buy a service from an ISP
In this approach, enterprises negotiate with their ISPs for DDoS protection, which outsources the issues to the provider.
When evaluating this option, enterprises should consider how to initiate and test the service.
How to initiate the service
What does the ISP do automatically? Typically, in this scenario, it's nothing. Although the technology is designed to enable signaling from the client to invoke scrubbing, few carriers will do this, as it can lead to client manipulation of carrier resources.
The ISP usually provides a procedure by which to initiate the service, which is typically triggered by a call from an authorized person. Average time frames for initiation are 15 to 30 minutes from notification.
How to test the service
DDoS services from ISPs involve redirecting traffic to a scrubbing center. This usually involves Border Gateway Protocol (BGP) configuration changes that affect service. However, an outage caused by a DDoS attack is not the best time to reconfigure your BGP peering for the first time.
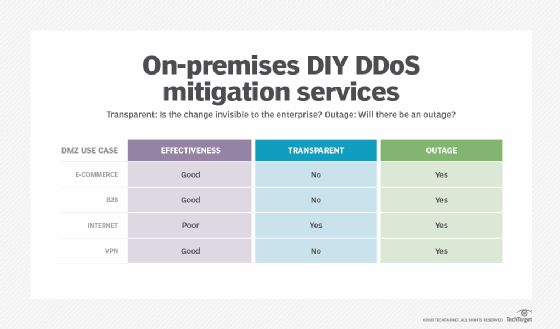
DIY DDoS mitigation
With this strategy, enterprises have registered IP address space and also provide clients with an e-commerce portal. Often, enterprises choose this option if management is uncomfortable with redesigning applications for use on a CDN or the firm simply doesn't like to outsource control.
Enterprises have two primary DIY DDoS mitigation approaches to choose from: on-premises and colocation.
ISP connections that terminate on premises at the data center or headquarters
With this option, enterprises can deploy IPS and next-generation firewalls (NGFWs) at their ISP edge to automatically block well-known DDoS attack vectors. Common choices include equipment from Palo Alto Networks, Cisco, Checkpoint and Fortinet. Many IPSes come with subscription services that deflect known problems.
While many of these systems can do double duty as IPSes and NGFWs, enterprises should consider the overhead of deflecting the DDoS traffic. The best approach is to deploy two pairs: one set as redundant IPSes and the other as redundant NGFWs. This also prevents the need to supersize the devices to cover corner cases.
Enterprises can also deploy specialized hardware systems, but they have limited utility against volumetric DDoS attacks, as the traffic will already have choked out the ISP links.
ISP connections that terminate at a colocation facility
With this approach, the ISP connects through a cross-connect, and enterprises are better able to protect downstream bandwidth to the company. As with the on-premises case, enterprise teams can deploy IPSes and NGFWs. They can also use specialized DDoS systems to protect downstream bandwidth.
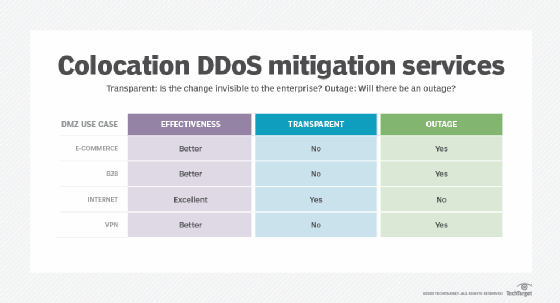
However, enterprises may want to combine a DIY service with additional services, such as those from Cloudflare or OpenDNS. These services are especially important if systems are not forward deployed at a colocation facility. Both sets of products cover DNS, but Cloudflare can also cover a variety of DDoS attacks before they reach the network.
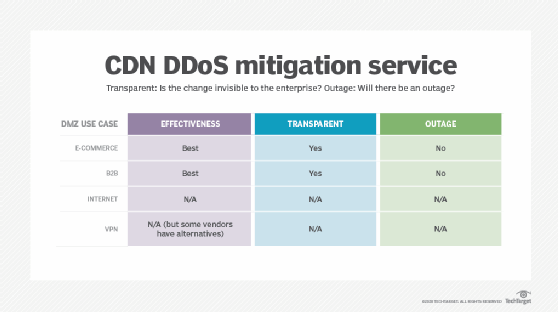
CDNs and DDoS mitigation
With a CDN strategy, enterprises contract with a full-service CDN to protect critical infrastructure and e-commerce applications. Typical CDN vendors include firms like Akamai and Cloudflare, but such services can also be delivered through cloud service offerings, like Microsoft Azure and AWS.
The CDN concept was originally developed and pioneered by firms like Akamai to improve website scalability and performance. By forward deploying servers around the country or even around the world, performance improved dramatically for web-based content. Studies showed that simply decomposing a website's base pages, graphics and other static content had a remarkable effect on user perceptions.
However, early in the deployment of these services, it also became apparent that CDN-based websites fared better than self-hosted sites in availability, redundancy and security. The indirect use of corporate servers kept website attacks off the enterprise altogether. The much wider capability of major CDN vendors also led to the discovery that CDN-based systems fared better than self-hosted systems during significant volumetric attacks.
Most of these CDN services come with DNS and other advanced persistent threat services built in. While a CDN is the best choice for any e-commerce application, this option does present some drawbacks and limitations, including the following:
- some redesign may be necessary for e-commerce applications;
- redesign is necessary for B2B portals;
- DNS changes are required; and
- cost.
How to choose a DDoS mitigation strategy
The DMZ today is complex, and no single strategy works for everyone. That said, most enterprises running an e-commerce or B2B portal would be best served by the use of a CDN. However, outbound employee use of the internet and inbound VPN access require a separate approach.
Enterprises that debate whether to buy a DDoS protection service or go DIY for any remaining internet access should consider the following factors:
- Does your staff have the expertise to DIY?
- If so, can you maintain this expertise over time?
If the answer to either of these is no, you should buy the DDoS service -- but remember to test it upfront and on a regular schedule. Enterprises should also note that some ISPs offer DNS and CDN services, as well as DDoS protection, and some CDN vendors offer services that replace VPNs.






