
maxkabakov - Fotolia
Cisco SecureX provides front end for all security tools
Cisco SecureX, unveiled at RSA, provides centralized intelligence from all the vendor's security products. Also at RSA, Juniper adds encrypted traffic analysis to the Juniper ATP Cloud.
SAN FRANCISCO -- Cisco has launched a cloud-based front end for its security products. The software, called SecureX, provides a central location for viewing intelligence and responding to threats.
Cisco, which introduced SecureX this week at the RSA Conference, said it would offer the all-in-one console at no additional charge. The company plans to make the product available at the end of May to all security customers.
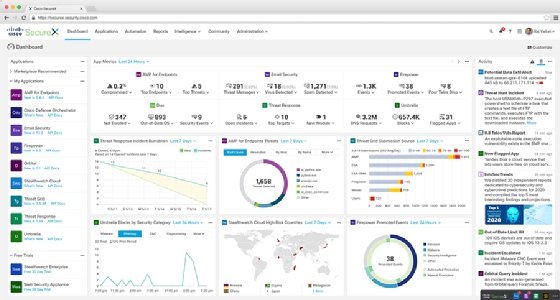
Cisco SecureX aggregates data generally seen through the user interface of each Cisco product. Some of the applications displayed in the SecureX dashboard include Email Security, Advanced Malware Protection for Endpoints and Stealthwatch Cloud, which monitors for threats on public cloud platforms. Others include Firepower Threat Defense, a next-generation firewall, and Umbrella, a cloud-based internet security gateway.
Security teams will appreciate the option of trying a no-cost tool that can replace multiple products, said Jon Oltsik, an analyst at Enterprise Strategy Group. Cisco has been developing an architecture that aggregates intelligence and features from its security products for almost 10 years.
However, Cisco is not alone in building an aggregation platform. Other vendors include Palo Alto Networks and McAfee, Oltsik said. "The key will be the degree of integration."
Customers who log in to SecureX with a unique username and password will see a list of their licensed security products on the left-side of the front end's dashboard. On the right will be a collection of widgets. Each provides visualizations of the telemetry taken from a connected application.
On the top of the dashboard are drop-down lists that let customers go to a specific product, get more granular intelligence or access reports. Customers also can choose an automation tab for performing tasks like configuring firewalls or creating and managing policies.
The software engines behind SecureX include Defense Orchestrator, which is Cisco's platform for managing policies in its firewalls and intrusion prevention systems. Also under the covers is Threat Response, which is the company's integration software for aggregating threat intelligence.
Cisco wants to make SecureX a hub for third-party products, as well as its technology. The vendor has connected the front end to the public APIs of 60 products outside its portfolio. Accessing telemetry from a listed third-party application requires inputting its license key into SecureX.
Cisco's security business is competing in the fastest growing IT segment today. Cisco generated $2.7 billion in revenue from security in the company's 2019 fiscal year. By 2022, Cisco would like to be one of several security vendors that could reach $5 billion in annual revenue, Oltsik said.
"That's what Cisco is chasing," he said.
Juniper improves security in ATP Cloud
In other security news at RSA, Juniper Networks announced that it had added encrypted traffic analysis to the cloud version of the company's Advanced Threat Prevention software. Juniper sells ATP Cloud as an add-on to the company's SRX firewalls.
Juniper has opted for behavior-based security in its encrypted traffic analysis engine. The former is a proactive approach that monitors activity for deviations from standard behavior patterns. When an anomaly is detected, ATP orders the SRX firewall to block suspected files.
In general, ATP scans files, including email attachments, to identify those that might originate from an infected host, such as a remote server, a PC or a mobile device. ATP also looks for malicious activity in logs collected from third-party security devices, such as firewalls and web and email gateways.
Juniper also introduced Security Intelligence (SecIntel) to the cloud-based management software of the company's Mist Wi-Fi system. SecIntel monitors for threats in wireless traffic on Mist access points. Customers' SRX firewalls would block traffic identified as possibly malicious.
Juniper will require Mist customers to buy a separate license for SecIntel. The vendor plans to make the service generally available in the second quarter.






