
Tierney - stock.adobe.com
SD-WAN, 5G remote work technologies enable future networks
In this roundup of networking blogs, learn how SD-WAN and 5G can benefit business continuity plans for network infrastructure and whether split tunneling is necessary -- or safe.
As remote workforces continue to grow, newer networking technologies can adapt to and enhance remote work policies for organizations.
Three networking bloggers recently explored how networking technologies, such as software-defined WAN (SD-WAN) and 5G, can enable and benefit remote work for enterprise employees, as well as how features like split tunneling could negatively affect remote work. IT teams could beef up future business continuity (BC) plans for network infrastructure if they incorporate SD-WAN and 5G remote work capabilities instead of, or in addition to, traditional options, such as VPNs with split tunneling features.
SD-WAN isn't a stranger to many organizations; the technology is, and has been, popular, as it can benefit organizations as they plan, experience and enable digital transformation strategies. Also, SD-WAN and cloud resources can create reliable, secure connections among branch offices, cloud environments, data centers and company headquarters.
For enterprises with multiple branch office locations, SD-WAN provides several connectivity benefits, wrote Bob Laliberte, practice director and senior analyst at Enterprise Strategy Group, in an ESG blog post. SD-WAN benefits include the following capabilities:
- prioritizes application traffic to ensure voice and video applications consistently perform well;
- uses all existing bandwidth; and
- segments traffic so personal traffic doesn't affect business traffic.
SD-WAN's benefits also shine through in times of increased remote work reliance, such as during a pandemic. Many businesses have accelerated SD-WAN deployments or rethought BC plans since COVID-19 concerns began, Laliberte said, largely because IT leaders believe SD-WAN's benefits don't end at traditional workspaces.
"It stands to reason that, if [SD-WAN] can provide benefits to the branch office, it can do the same for the employee now working from home," Laliberte said.
Dive deeper into Laliberte's analysis of SD-WAN as an essential remote work technology.
With 5G, remote work technology will bring the enterprise to the home office
While 5G isn't yet mainstream, its touted features and benefits point experts toward its potential benefits for remote work. network slicing is one key feature of a 5G remote work technology, wrote Malcolm Rogers, analyst at GlobalData Plc, on the GlobalData blog. Additionally, 5G could be a more affordable connectivity option for organizations with growing remote workforces.
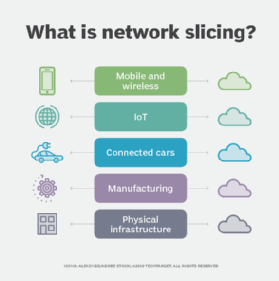
Network slicing architecture virtually divides networks into slices to separate traffic that originates from different services and applications, although these slices typically run in the same hardware. With network slicing in 5G, remote work won't have to compete with traditional home network traffic -- such as streaming or gaming -- for bandwidth. Network slicing would enhance 5G remote work technology, Rogers said.
Another 5G remote work benefit is mobile edge computing capabilities, which move business-critical applications, workloads and sensitive data to the edge of the network and, therefore, closer to remote employees for lower latency and improved performance. Because most people live within cellular coverage areas, 5G is also a more accessible and affordable connectivity option for remote employees to divide networks between home and business uses.
"When combined with a secure 5G network slice, enterprises can be more comfortable moving sensitive data and applications from the headquarters to network edges near their employees' homes," Rogers said.
Learn more of Rogers' thoughts on 5G remote work capabilities, edge computing and network slicing.
Long-term remote work may cause the end of split tunneling
Whether an organization uses VPNs, SD-WAN or 5G, remote work requires reliable network security. For organizations with VPN services, this could mean disabling split tunneling, network engineer Russ White wrote on the ECI blog. Split tunneling is a feature that enables a single VPN client to reach more than a single destination, and it has a variety of pros and cons. However, both the pros and cons have one common denominator: malware.
Malware is a program or file with potential to harm users. The two following reasons to disable VPN split tunneling both deal with malware, according to White:
- Without split tunneling, infected data from a compromised endpoint has only one way to get out: through the corporate network. There, internal network controls take over and act against the malware.
- If a user opens a file infected with malware and split tunneling is disabled, those same internal network controls can take over and take preventative action to protect the corporate network.
However, disabling split tunneling also introduces challenges to IT teams. For example, IT teams may struggle to monitor whether employees use the corporate network to access personal data or data unrelated to work. This could also give bad actors access to company networks if an employee opens a compromised file while connected to the corporate VPN.
To avoid the issue of split tunneling altogether, organizations may choose to avoid VPN services.
"There are no clear answers in split tunneling other than moving more towards a web-application style architecture for all access, and reduce VPN use to the minimal possible, to properly support high numbers of remote users," White said.
Explore more of White's analysis of split tunneling pros and cons.







