
stock.adobe.com
Network security in 2020 highlights zero trust, SD-branch
In this roundup of networking blogs, experts explore various aspects of network security -- from old and evergreen to new and innovative -- and the roles they play in 2020.
Bad actors grow more advanced every day, so organizations must ensure their network security is consistently up to date and as efficient as possible.
This is especially true for network security in 2020, as many organizations moved network resources to cloud environments and remote workforces grew as a result of the COVID-19 pandemic. Three networking bloggers explored different aspects of network security in 2020: zero-trust networks, network access control (NAC) and software-defined branch (SD-branch).
Overall, while innovative network security technologies benefit organizations in new ways, evergreen network security features are also crucial to secure network resources.
Zero-trust networks and chocolate chip cookies
In the past, many experts thought ideal network security was like the ideal chocolate chip cookie: tough and crunchy on the outside but soft in the middle. However, network security in 2020 and beyond must be tough and crunchy all the way through, according to network engineer Russ White. A soft center doesn't protect the rest of the cookie's center -- or organization -- from bad actors or insider attacks, so network security must be tough throughout the organization.
The crunchy cookie, in the network security context, is zero-trust networks. Zero-trust models aim to protect networks from attackers and prevent attackers from moving laterally through the network, White said in a Rule11 blog post. However, modern networks aren't freshly baked cookies at all. Due to adoption of cloud environments and growing remote workforces, modern networks are like cookie dough that spreads and softens the network edge until bad actors can access its weak spots from almost anywhere.
"There just isn't a hard edge any longer to harden; just because someone is 'inside' the topological bounds of your network does not mean they are authorized to be there or to access data and applications," White said.
Learn more about zero-trust networks in White's post.
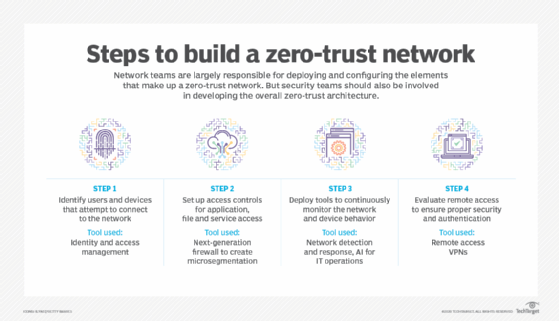
What's new with NAC?
Even amid new and tougher requirements for network security in 2020, NAC is an evergreen skill for network engineers. NAC makes network resources available strictly to authenticated and trusted endpoints and enables network teams to monitor those endpoints when they're on the network. Senior network engineer Deirra Footman delved into NAC's technical details in a recent post on her blog, CCIE By 30.
Footman explored NAC for 802.1x -- a security protocol for 802.11-compliant wireless LANs -- as well as requirements for 802.1x Extensible Authentication Protocol (EAP). EAP is arguably more accessible than Media Access Control address-based authentication, Footman said, as network engineers use MAC address-based authentication primarily for devices that can't use 802.1x EAP, including uninterruptible power supply devices or IP cameras.
While NAC is nothing new, Footman noted a nontraditional approach to support NAC. With this approach, network teams use information from address resolution protocol poisoning -- or ARP spoofing -- attacks in which bad actors circulate false ARP messages over a LAN to link their MAC addresses with authorized endpoints' IP addresses.
"Essentially, you would install an appliance or sensor on the network that monitors and captures ARP packets when a device connects to the network. This appliance can analyze information like device models, operating systems, etc. This information is then sent to a controller and evaluated based on the policies you set. Access is then granted or denied based on the policies set," Footman said.
Explore more of Footman's explanation of NAC.
Software-defined network security in 2020 and beyond
SD-branch entered the network security space in the late 2010s, with intentions to collapse separate branch networking and security functionalities into a single appliance. While the concept of SD-branch isn't new, the term SD-branch itself is gaining interest, to the chagrin of Gartner analyst Andrew Lerner, who said in a recent Gartner blog post that he doesn't love the idea of another software-defined term.
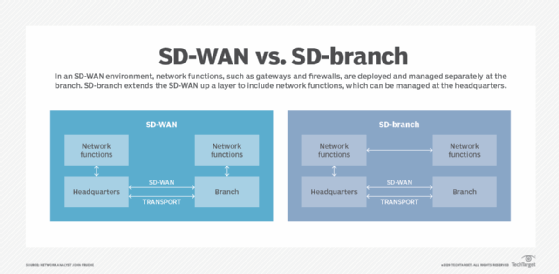
Regardless, Gartner jumped on the bandwagon, and Lerner said SD-branch must support key network appliances, such as WAN gateways and firewalls. SD-branch must also ensure those appliances have unified capabilities, such as reporting, visibility and automation capabilities, through one main console. With SD-branch, enterprises can automatically deploy a single, centralized policy from one location to devices in one or multiple locations.
"The notion of unified management of [a] branch office kit has been around. In prior years, [it] was referred to as BoB (branch office in a box). ... I suppose 'SD-branch' is a lot snazzier (but not SASE-er) than BoB3.0 or SecureNextGenBoBaaS," Lerner said.
Discover Lerner's list of other essential SD-branch features.






