
ra2 studio - Fotolia
Consider these 3 fundamentals of cloud architecture
In this roundup of networking blogs, experts explore three networking fundamentals of cloud architecture for both public and private cloud networks.
Cloud networking may not seem drastically different from traditional networking and legacy network architectures anymore, but some best practices won't function as well in the cloud as they do in on-premises data centers.
A handful of networking bloggers recently dove deep into the fundamentals of cloud architectures and discussed best practices enterprises can follow to get familiar with the cloud.
When network teams introduce cloud services to their networks, they might think the easiest route is to move existing network technologies and policies to the cloud. However, this practice can lead to improper networking habits and a poorly functioning network, Gartner analyst Andrew Lerner said in his personal blog on the fundamentals of cloud architecture for public clouds.
Carrying traditional policies over to a public cloud network could limit the network's access to cloud features, increase network complexity and raise network expenses. Instead of using traditional technologies and practices, network teams can take advantage of their cloud provider's cloud-native capabilities and benefits, Lerner said.
"Don't just forklift existing network policies/practices. Instead, modernize the notion of network 'ownership' by shifting focus from control to governance within IaaS environments," he wrote.
Most traditional networking vendors offer IaaS-capable versions of their service offerings, such as switches, routers, firewalls and more, he added.
Read more of Lerner's thoughts on fundamentals in public cloud architecture.
Fundamentals of cloud architecture regarding state
An area that frequently falls under the radar with cloud and microservices is state, which refers to a system's desired or operational set of conditions. Many current cloud services don't fully address potential issues that could arise with state, according to Tom Nolle, president of CIMI Corp. Cloud systems should ideally have stateful behavior that records previous user interactions and events. Currently, however, state in the cloud lacks a consistent definition, as cloud environments mostly host front-end transactions for businesses instead of all an organization's data.
In order to bring state to the stateless, IT should consider state control factors such as front-end control, back-end control and orchestration, Nolle said. By ensuring state control, IT teams can keep track of historical state information for easier access and management.
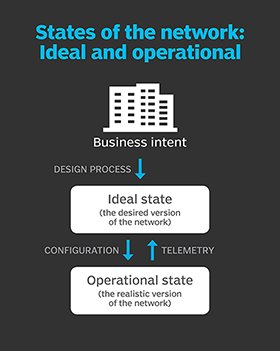
Organizations need more than just information from user interactions. It's crucial for the cloud environment to also store data from all transactions as well as the information necessary for understanding the data. If state databases recorded various transaction stages that teams can access through the cloud, this could enable more back-end state control and support.
Orchestration also plays a role in a cloud's stateful behavior, though it provides more distributed control than the other two factors. Orchestration can help store information on cloud modeling and sequencing, according to Nolle. However, these mechanisms are not consistent among cloud providers, which could cause issues with security and data storage.
"Since we're still seeing multiple implementation options among public cloud providers, that means that state management and persistent data strategies aren't portable without some tuning," Nolle wrote.
Dive further into Nolle's thoughts on state's relationship to the cloud.
Tips for building private cloud infrastructures
Network teams looking to bring virtual networking to private clouds have three main options, according to Ivan Pepelnjak on his ipSpace blog. These three methods of implementation include the following:
- Hypervisor-based overlays. Hypervisors isolate OSes and applications from hardware, and this option separates networking from physical infrastructure to reduce moving parts and provide stability. This is the most scalable of the three options, Pepelnjak said.
- Overlays based on top-of-rack switching. Also known as ToR, this type of switching connects computing equipment within a single or nearby rack and connects this equipment to an in-rack switch. IT can build this overlay using a virtual extensible LAN or Ethernet VPN. This option works best for network environments with virtual LANs that aren't static or fixed.
- ToR-based overlays with cloud orchestration. Vendors combine these services to alleviate issues with scalability, according to Pepelnjak, yet this method can be unreliable and difficult to control. With this option, ToR switches can connect directly to the system or require vendors to add a controller.
As with most services, network teams should choose the option that works best for their network.
"As always, there is no right answer -- you have to figure out what matters most: scalability, forwarding performance or ease-of-deployment... but whatever you do, try to keep the number of moving parts and interdependent components to the bare minimum," Pepelnjak wrote.
Explore more of Pepelnjak's thoughts on building private cloud infrastructure.







