kentoh - Fotolia
A glossary of the VPN terminology you need to know
For organizations with remote workforces, VPNs can be an essential part of daily life. This VPN glossary explores the essential terms and phrases that constitute VPN services.
Enterprises' embrace of remote work accelerated due to COVID-19, and it likely won't subside when the pandemic is a distant memory.
A staple of remote work is the VPN. With a VPN, organizations can provide their remote employees with secure network connectivity nearly indistinguishable from standard office connectivity. VPNs support full-time remote employees, employees who occasionally work from home and temporarily long-term remote employees. Yet, as with other network security concepts, VPN terminology can be difficult to understand. From encryption to protocols to tunneling, each word and phrase of VPN terminology is crucial to understand VPNs as a whole.
This glossary explores 12 key phrases of VPN terminology, including different types of VPNs and various protocols that VPN services use.
The essential VPN terminology you need to know
Advanced Encryption Standard. AES is a block cipher -- a method of text encryption -- developed and implemented globally to secure and encrypt highly classified and sensitive data. For example, the U.S. government uses AES to protect its sensitive data. AES is often compared to the Rivest-Shamir-Adleman algorithm, and VPN providers use either AES or RSA in VPN services.
Dynamic multipoint VPN. DMVPNs are one type of VPN that essentially applies mesh network topology to an organization's VPN connections. DMVPNs directly connect all sites within a network to one another. So, traffic isn't required to pass through an organization's headquarters, and each site can share data to another branch location.
Encryption. No list of VPN terminology is complete without the word encryption -- a process to disguise classified data and convert it into a secret code, which must be decrypted once the data arrives at its destination. VPNs encrypt connections between an organization's network and network resources and authorized users or employees.
Gateway. All data enters and exits networks through gateways. Gateways are network nodes that connect two networks with different transmission protocols and translate those protocols so the networks can communicate. Nearly every type of VPN uses gateways to connect users to networks.
Hardware VPN. A hardware VPN is another type of VPN, which is more expensive than a software-based VPN. However, hardware VPNs provide more security than software, can support more clients and provide load balancing to those clients. Hardware VPNs are physical appliances with the same features as standard VPNs but suit enterprise use cases better.
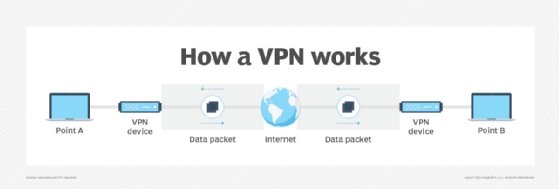
Internet Protocol Security. IPsec is a protocol that secures IP network traffic and provides the foundation for security services to enable network security at the IP layer. VPNs may use IPsec or other security protocols to enable extra security for organizations with network infrastructure that isn't able to provide security on its own.
Mobile VPN. Mobile VPNs are a type of VPN for mobile and other devices that move between physical locations. Mobile VPN tunnels use logical IP addresses, not physical addresses, to enable seamless VPN connectivity while devices roam. With mobile VPNs, users can move between private and public networks without risk to their security or connectivity.
Remote access. With remote access, users can connect to their organizations' networks remotely from somewhere other than their workplaces, such as from home. VPNs enable remote access. Also, a remote access VPN is a common type of VPN, which connects users to company networks through a VPN gateway and requires user authentication before it grants the user network access. Remote access VPNs typically use IPsec or Secure Sockets Layer protocols to enable secure connectivity.
Secure Sockets Layer. Like IPsec, SSL is a protocol to secure network connectivity for users. SSL typically secures connections over insecure networks, including the internet. In addition, another type of VPN is the SSL VPN, which strictly uses SSL or Transport Layer Security protocols to enable secure network connectivity.
Telecommuting. Telecommuting is when employees can complete any part of their workdays from outside traditional workplaces or office settings. This is also called working remotely. The internet introduced capabilities that kick-started telecommuting, such as email, collaboration platforms and video conferencing. VPNs enable telecommuting capabilities, as remote employees can access company networks and network resources securely through a VPN as if they are in the workplace.
Tunneling. Tunneling, or port forwarding, is a process designed to privately transmit data between networks. Tunneling enables networks to communicate securely over a public network or the internet. VPNs use tunneling protocols to encrypt data that moves between a company network and its employees' VPN clients, and unauthorized users can't access that secure data.
Virtual private network. This collection of VPN terminology ends with the acronym itself: VPN. VPNs encrypt connections between remote, authorized users and an organization's network and network resources. VPNs use secure software, which runs on authorized devices and clients so employees can access the same essential network resources they could if they directly connected to the company network. VPNs can enable secure remote access to and from branch offices, as well as for employees unable to physically work in their office space.







