
Getty Images/iStockphoto
15 common network protocols and their functions explained
Networking makes the internet work, but it needs several key protocols. These common network protocols make communication and connection across the internet possible.
Without network protocols, the modern internet would cease to exist.
Network protocols enable the exchange of information across the internet. They work behind the scenes so effectively that most users don't know what they do and don't think twice about how they work. However, it's important for networking professionals to understand protocols, which are the backbone of effective networking.
Networking protocols are categorized into three main types: communication protocols that facilitate data exchange between devices, management protocols that oversee and control network operations, and security protocols that ensure the protection, authentication and integrity of data during transmission.
To get a better understanding of how these protocols work and how communication occurs between devices on a network, it's useful to examine two fundamental networking models: Open Systems Interconnection (OSI) and Transmission Control Protocol/Internet Protocol (TCP/IP). OSI is a theoretical model with seven distinct layers providing a conceptual network communication framework. The OSI model is valuable for understanding networking concepts.
TCP/IP, on the other hand, is the most widely used model, powering the internet and most private networks. It provides a standardized framework that lets devices easily communicate, ensuring efficient and seamless data exchange.
When comparing both models, the OSI model is similar to a detailed blueprint for constructing a house, where every component is meticulously defined. In contrast, the TCP/IP model represents the actual house built from a simplified version of that blueprint -- it's functional and livable but not as detailed.
TCP/IP is typically divided into four layers, with each layer representing a different set of protocols and having a distinct purpose:
- Application layer. The application layer interacts directly with end users and provides them with network services, including web browsing, file transfers and email communication. Protocols such as domain name system (DNS), Dynamic Host Configuration Protocol (DHCP), File Transfer Protocol (FTP), Hypertext Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), Simple Network Management Protocol (SNMP), Secure Shell (SSH) and Telnet operate at this layer.
- Transport layer. The transport layer provides end-to-end communication between hosts and ensures data delivery. Protocols such as TCP and User Datagram Protocol (UDP) operate at this layer. However, while TCP is designed to be reliable, transport layer protocols aren't always reliable.
- Internet layer. Also known as the network layer, the internet layer is responsible for routing data packets from source to destination across networks. It uses logical IP addresses to determine the best path to send data to its destination. IP is the primary protocol operating at this layer, but other protocols, such as Address Resolution Protocol (ARP) and Internet Control Message Protocol (ICMP), also operate there.
- Link layer. Also known as the data link layer, this layer is responsible for the physical transmission of data over network hardware, using protocols such as Ethernet for wired networks or a variation of 802.11 for wireless or Wi-Fi networks.
Other specialized protocols important to the functioning of the internet work alongside or as part of the network layer in the TCP/IP model. However, they aren't considered core to the TCP/IP stack. These include routing protocols, such as Border Gateway Protocol (BGP) and Open Shortest Path First (OSPF).
This glossary explores 15 common network protocols that administrators should be familiar with. It also provides information about these protocols' main functions and their importance in computer networks.
Application layer protocols
1. Domain name system
DNS is an application layer protocol that acts as the internet's phone directory. Each device on the internet has a unique and corresponding IP address, similar to a phone number. However, it's hard for humans to remember numerical labels, so DNS uses a resolution process to solve this problem.
When a user types a domain name, such as google.com, into a web browser, the computer sends a request to a DNS server to find the corresponding IP address so the user's computer connects to the correct server. DNS servers also help with the reverse process, resolving numerical IP addresses to their corresponding domain names.
DNS is essentially a directory of fully qualified domain names (FQDNs) and their corresponding IPv4 or IPv6 addresses. It contains various types of records, including the following:
- A record. An A record is used to map an FQDN to an IPv4 address.
- AAAA record. This record maps an FQDN to an IPv6 address.
- Canonical name record. A CNAME record works as an alias and maps one domain name to another.
- Mail exchanger record. An MX record lists mail servers for domain mail exchange.
- Pointer record. A PTR record is a reverse lookup that maps an IP address to an FQDN.
Other records related to the DNS structure include top-level domains and root servers.
IoT protocols explained
Here are five of the top protocols and their features that matter most to IoT. Download your free guide now.
2. Dynamic Host Configuration Protocol
DHCP automates the process of assigning IP addresses to network endpoints so they can communicate with other network devices over IP. Whenever a device joins a network with a DHCP server for the first time, DHCP automatically assigns it a new IP address and continues to do so each time a device moves locations on the network. Without DHCP, network administrators must manually assign IP addresses to each new device.
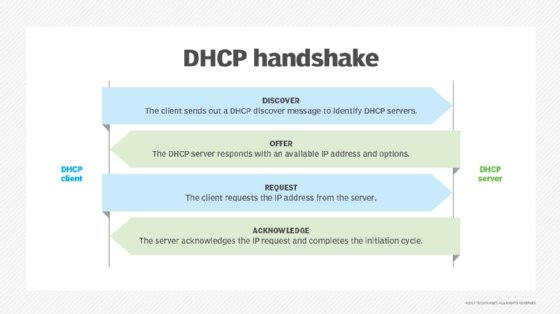
When a device connects to a network, a DHCP handshake takes place. In this handshake process, the device and DHCP server communicate using the following steps:
- The device establishes a connection and sends a DHCP broadcast request on the LAN to find a DHCP server that could assign an IP address to it.
- One or more DHCP servers respond, offering available IP addresses.
- The device selects an address and formally requests it.
- If the server approves, it acknowledges the request and records the device's IP address, MAC address and other relevant details, such as the hostname and subnet mask.
- The IP address is leased to the device for a short period, after which the lease expires.
- Once 50% of the lease time has elapsed, the device can begin requesting a lease renewal.
Besides dynamically assigning IP addresses, a DHCP server also passes essential network configuration information, such as subnet masks, default gateways, DNS server addresses and domain names, to the requesting device. This enables devices to communicate seamlessly within both local and external networks.
3. File Transfer Protocol
FTP is a client-server protocol that transfers files between a client and a server and operates over TCP/IP. It uses two communication channels: the command channel and the data channel. Clients request files through the command channel and receive access to download, edit and copy the file, among other actions, through the data channel.
While FTP is a file-transferring protocol, it doesn't encrypt data and sends it in plaintext, making it vulnerable to security risks. Therefore, most businesses opt for file transfer protocols that are secure, such as Secure FTP, to safely transfer files over a network.
4. Hypertext Transfer Protocol
HTTP operates on a client-server model and is the primary method by which web browsers and servers communicate to share information over the internet. While its main purpose is to transfer webpages and provide other resources during web browsing, it is also able to transfer data, facilitating file sharing.
When a user enters a website domain and tries to access it, HTTP establishes a connection to the server hosting the domain and provides access to the website. For example, when a user types a domain name, such as google.com, into their browser, HTTP connects to the web server hosting that domain. The web server then responds by sending the HTML content or the code that defines the structure and content of the webpage.
Another form of HTTP is HTTP Secure. HTTPS can encrypt a user's HTTP requests and webpages, providing greater network security and preventing common cybersecurity threats, such as man-in-the-middle attacks.
HTTPS is more widely used than HTTP because of its improved security features, and most major browsers now only support HTTPS.
5. Simple Mail Transfer Protocol
SMTP -- the most widely used email protocol -- is part of the TCP/IP suite and controls how email clients send users' email messages. Email servers use SMTP to send email messages from the client to the email server to the receiving email server. However, SMTP doesn't control how email clients receive messages -- just how clients send messages. Essentially, it's just a mail delivery protocol and not used for retrieval of messages.
That said, SMTP requires other protocols to ensure email messages are sent and received properly. It can work with Post Office Protocol 3 or Internet Message Access Protocol, both of which control how an email server receives email messages.
6. Simple Network Management Protocol
SNMP is a network management protocol that helps network admins manage and monitor network devices, such as routers, switches, printers and firewalls. It gathers device information to monitor network performance and health. Network administrators often use SNMP to detect and troubleshoot network issues.
SNMP uses a manager-agent model and the following components:
- SNMP manager. This is the central system that communicates with the agents and requests or updates information.
- SNMP agent. This is a software component installed on devices such as routers and switches and sends information to the manager.
- Management information base. The MIB acts as a database and contains device information.
Here is how SNMP works:
- Manager request. The SNMP manager sends a request using the SNMP protocol to an SNMP agent on a device. The request includes information, such as CPU use and interface status.
- Agent response. The SNMP agent retrieves the requested information from the MIB and sends it back to the manager in an SNMP response.
- Manager action. The manager is now able to display the information, log it or use it to trigger an action. For example, it can send an alert or change a configuration.
Since SNMP is a standardized protocol, it's compatible with devices from different vendors.
7. Secure Shell
The SSH protocol provides a way to securely connect to and send commands to a device over an insecure network, such as the internet. It uses cryptography for authentication and establishes an encrypted digital tunnel between devices, protecting communication from eavesdropping and tampering.
SSH is widely used for the remote administration of servers, network devices and other systems. It automates various tasks on these remote systems, including software updates, backups and system monitoring. Additionally, it offers tunneling or port forwarding, which enables data packets to traverse networks that are otherwise inaccessible.
8. Telnet
Telnet is designed for remote connectivity. It establishes connections between a remote endpoint and a host machine to enable a remote session. Telnet prompts the user at the remote endpoint to log on. Once the user is authenticated, Telnet gives the endpoint access to network resources and data at the host computer.
Telnet has existed since the 1960s and was the first draft of the modern internet. However, Telnet lacks sophisticated security protection as it transmits data in plaintext, including usernames and passwords. Because of these security concerns, Telnet isn't commonly used anymore. While generally deprecated, it could occasionally be used in certain scenarios, such as basic network connectivity testing, to check if a port is open on a remote server, although it's not recommended. Some older legacy systems might still rely on Telnet, but this is rare.
Transport layer protocols
9. Transmission Control Protocol
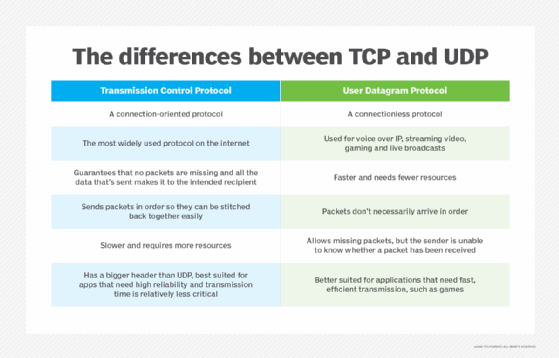
TCP is a connection-oriented transport layer protocol that offers reliable delivery through packet sequencing, retransmission of lost packets and flow control.
It arranges packets in order after IP has delivered them. TCP numbers individual packets because IP can send packets to their destinations through different routes and get them out of order. TCP checks and reassembles the packets at the destination before delivering them to the application. IP's job is complete once the packet reaches the destination host; TCP's job begins at this point. It takes over to ensure reliable and in-order delivery to the application.
TCP also detects errors in the sending process, including if any packets are missing based on TCP's numbered system, and it requires IP to retransmit missing packets. Through this process, the TCP/IP suite controls communication across the internet.
10. User Datagram Protocol
UDP is an alternative to TCP and also works with IP to transmit time-sensitive data. UDP enables low-latency data transmissions between internet applications, making it ideal for real-time applications where low latency is important, but some data loss is acceptable, such as with VoIP, audio or video streaming, and online gaming.
Unlike TCP, UDP is connectionless and doesn't wait for all packets to arrive. Instead, UDP transmits all packets even if some haven't arrived.
UDP solely transmits packets and doesn't offer packet sequencing, organizing or retransmission. TCP, on the other hand, transmits, organizes and ensures the packets arrive. While UDP is a lightweight protocol and works faster than TCP, it's also less reliable.
Internet layer protocols
11. Address Resolution Protocol
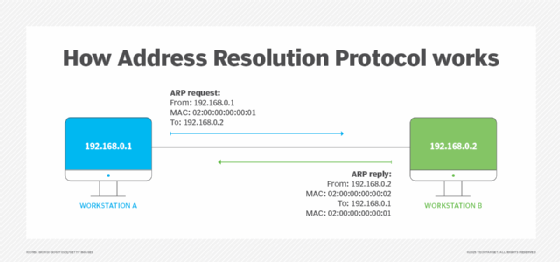
ARP maps IP addresses to physical MAC addresses of devices and vice versa within a LAN so devices can communicate with one another. ARP is necessary because IP and MAC addresses are different lengths and operate on different layers of the OSI model.
These addresses must be mapped for proper network communication and data transfer among connected devices. ARP isn't required every time devices attempt to communicate because the LAN's host system maps and stores the associations in its ARP cache. As a result, the ARP resolution process is mainly used when new devices join the network.
12. Internet Control Message Protocol
ICMP is a supporting protocol on the internet layer of the TCP/IP model. It's mainly used for network diagnostics, troubleshooting, error reporting and some limited control functions between network devices. It helps identify network connectivity issues and manage the flow of data packets. However, it doesn't transfer data, such as the content of a webpage or an email.
Ping and traceroute commands both use ICMP to test connectivity and trace packet routes. Common ICMP messages include the following:
- Echo Request and Echo Reply.
- Destination Unreachable.
- Time Exceeded.
- Redirect Message.
13. Internet Protocol
IP functions similarly to a postal service. When users send and receive data from their devices, the data gets spliced into packets. Packets are like letters with two IP addresses: one for the sender and one for the recipient.
After the packet leaves the sender, it goes to a gateway or router, similar to a post office, which guides it toward its destination. Packets continue to travel through several gateways until they reach their destinations.
IP is commonly paired with TCP to ensure reliable data delivery. IP sends packets to their destinations as they arrive, while TCP makes sure they are in the correct sequence since IP is connectionless and can deliver them out of order if they take different routes across the network.
Want to learn more about common network protocols?
Check out these video definitions from TechTarget's YouTube channel, Eye on Tech, to get more insight into common network protocols.
Other specialized protocols
14. Border Gateway Protocol
BGP makes the internet work. This routing protocol helps with the exchange of routing information between different autonomous systems. An AS is a group of IP networks or prefixes under the control of a single administrative entity with a defined routing policy. This entity could be a large organization, ISP, university or government agency.
As data travels across the internet, it must pass through multiple ASes to reach its destination. Within an AS, routers use BGP to advertise the active networks they manage to their neighboring routers. These neighbors then exchange routing information, learning about local networks within the same AS and networks reachable through external ASes as sessions are established between edge routers of different ASes.
Information exchange within the same AS is handled through Internal BGP, or iBGP, while information exchange between external ASes is managed using External BGP, or eBGP. As routers are added or removed within networks, BGP dynamically propagates route changes, announcing additions and removals to its neighbors to maintain up-to-date routing tables.
To select the most efficient route for data to travel across ASes, BGP evaluates various attributes, such as the AS path length and policy preferences. While BGP is best known for routing traffic across the internet between ASes, it's also used within large, complex data center networks to advertise network reachability and ensure efficient traffic routing.
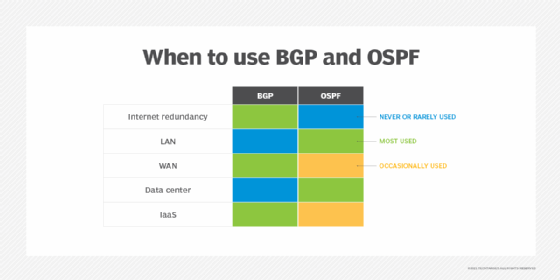
15. Open Shortest Path First
OSPF is a dynamic link-state routing protocol for IP networks. It works with IP to send packets to their destinations. IP aims to send packets on the quickest route possible, which OSPF is designed to accomplish. OSPF opens the shortest, or fastest, path first for packets. It also updates routing tables -- a set of rules that control where packets travel -- and alerts routers of changes to the routing table or network when a change occurs.
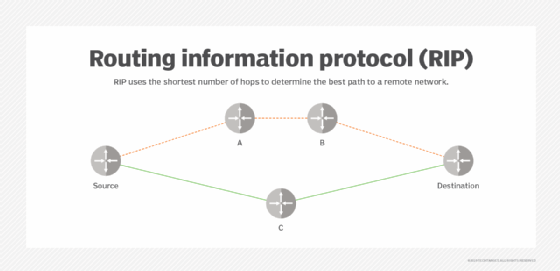
OSPF is similar to and supports Routing Information Protocol (RIP), which directs traffic based on the number of hops it must take along a route, and it has also replaced RIP in many networks. OSPF was developed as a streamlined and scalable alternative to RIP. For example, RIP sends updated routing tables out every 30 seconds, while OSPF sends updates only when necessary and makes updates to the particular part of the table where the change occurred. Also, OSPF typically uses more sophisticated metrics, such as bandwidth, delay and link cost, rather than hop counts to choose the best paths.
OSPF is well suited for larger networks or enterprises as it provides a full view of the network topology.
Kinza Yasar is a technical writer for WhatIs and has a background in computer networking.
Michaela Goss is senior site editor for TechTarget's Customer Experience and Content Management sites.







