stateful inspection
What is stateful inspection in networking?
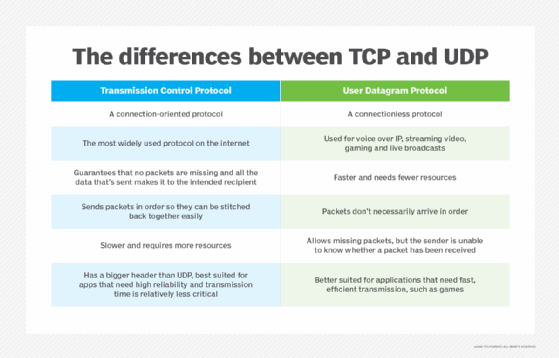
Stateful inspection, also known as dynamic packet filtering, is a firewall technology that monitors the state of active connections and uses this information to determine which network packets to allow through the firewall. Stateful inspection is commonly used in place of stateless inspection, or static packet filtering, and is well suited to Transmission Control Protocol (TCP) and similar protocols, although it can also support protocols such as User Datagram Protocol (UDP).
Stateful inspection is a network firewall technology used to filter data packets based on state and context. Check Point Software Technologies developed the technique in the early 1990s to address the limitations of stateless inspection. Stateful inspection has since emerged as an industry standard and is now one of the most common firewall technologies in use today.
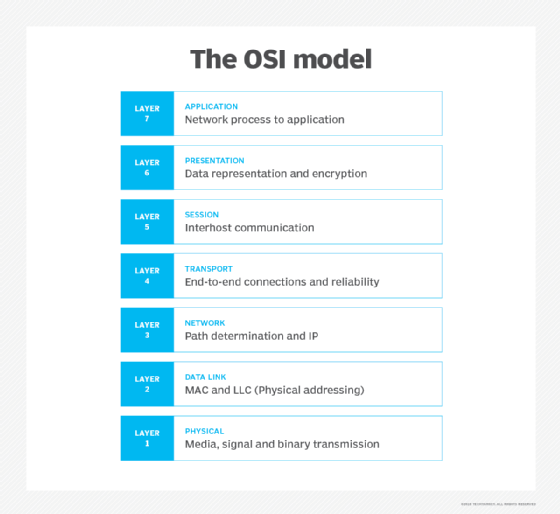
Stateful inspection operates primarily at the transport and network layers of the Open Systems Interconnection (OSI) model for how applications communicate over a network, although it can also examine application layer traffic, if only to a limited degree. Packet filtering is based on the state and context information that the firewall derives from a session's packets:
- State. The state of the connection, as it's specified in the session packets. In TCP, for example, the state is reflected in specific flags, such as SYN, ACK and FIN. The firewall stores state information in a table and updates the information regularly.
- Context. Information such as source and destination Internet Protocol (IP) addresses and ports, sequence numbers and other types of metadata. The firewall also stores context information and updates it regularly.
By tracking both state and context information, stateful inspection can provide a greater degree of security than with earlier approaches to firewall protection. The stateful firewall inspects incoming traffic at multiple layers in the network stack, while providing more granular control over how traffic is filtered. The firewall can also compare inbound and outbound packets against the stored session data to assess communication attempts.
What are stateful and stateless inspection?
Stateful inspection has largely replaced stateless inspection, an older technology that checks only the packet headers. The stateless firewall uses predefined rules to determine whether a packet should be permitted or denied. It relies on only the most basic information, such as source and destination IP addresses and port numbers, and never looks past the packet's header, making it easier for attackers to penetrate the perimeter.
For example, an attacker could pass malicious data through the firewall simply by indicating "reply" in the header.
Stateful inspection can monitor much more information about network packets, making it possible to detect threats that a stateless firewall would miss. A stateful firewall maintains context across all its current sessions, rather than treating each packet as an isolated entity, as is the case with a stateless firewall. However, a stateful firewall requires more processing and memory resources to maintain the session data, and it's more susceptible to certain types of attacks, including denial of service.
With stateless inspection, lookup operations have much less of an impact on processor and memory resources, resulting in faster performance even if traffic is heavy. That said, a stateless firewall is more interested in classifying data packets than inspecting them, treating each packet in isolation without the session context that comes with stateful inspection. This also results in less filtering capabilities and greater vulnerability to other types of network attacks.
How does stateful inspection work?
Stateful inspection monitors communications packets over a period of time and examines both incoming and outgoing packets. The firewall tracks outgoing packets that request specific types of incoming packets and allows incoming packets to pass through only if they constitute a proper response.
A stateful firewall monitors all sessions and verifies all packets, although the process it uses can vary depending on the firewall technology and the communication protocol being used.
For example, when the protocol is TCP, the firewall captures a packet's state and context information and compares it to the existing session data. If a matching entry already exists, the packet is allowed to pass through the firewall. If no match is found, the packet must then undergo specific policy checks. At that point, if the packet meets the policy requirements, the firewall assumes that it's for a new connection and stores the session data in the appropriate tables. It then permits the packet to pass. If the packet doesn't meet the policy requirements, the packet is rejected.
The process works a little differently for UDP and similar protocols. Unlike TCP, UDP is a connectionless protocol, so the firewall cannot rely on the types of state flags inherent to TCP. Instead, it must use context information, such as IP addresses and port numbers, along with other types of data. In effect, the firewall takes a pseudo-stateful approach to approximate what it can achieve with TCP.
In a firewall that uses stateful inspection, the network administrator can set the parameters to meet specific needs. For example, an administrator might enable logging, block specific types of IP traffic or limit the number of connections to or from a single computer.
In a typical network, ports are closed unless an incoming packet requests connection to a specific port and then only that port is opened. This practice prevents port scanning, a well-known hacking technique.








